Contents
- Fixing vulnerabilities in an isolated network
- Scenario: Fixing third-party software vulnerabilities in an isolated network
- About fixing third-party software vulnerabilities in an isolated network
- Configuring the Administration Server with internet access to fix vulnerabilities in an isolated network
- Configuring isolated Administration Servers to fix vulnerabilities in an isolated network
- Transmitting patches and installing updates in an isolated network
- Disabling the option to transmit patches and install updates in an isolated network
Fixing vulnerabilities in an isolated network
This section describes the steps that you can take to fix third-party software vulnerabilities on managed devices connected to Administration Servers that do not have internet access.
Scenario: Fixing third-party software vulnerabilities in an isolated network
You can install updates and fix vulnerabilities of the third-party software installed on managed devices in an isolated network. Such networks include Administration Servers and managed devices connected to them that have no internet access. To fix vulnerabilities in this kind of network, you need an Administration Server connected to the internet. Then, you will be able to download patches (required updates) by using the Administration Server with internet access, and then transmit the patches to isolated Administration Servers.
You can download the third-party software updates issued by software vendors, but you cannot download updates for Microsoft software on isolated Administration Servers by using Kaspersky Security Center.
To find out how the process of fixing vulnerabilities in an isolated network works, see the description and scheme of this process.
Prerequisites
Before you start, do the following:
- Allocate one device for connecting to the internet and downloading patches. This device will be counted as the Administration Server with internet access.
- Install Kaspersky Security Center, no earlier than version 14, on the following devices:
- Allocated device, which will act as the Administration Server with internet access
- Isolated devices, which will act as the Administration Servers isolated from the internet (hereinafter referred to as isolated Administration Servers)
- Make sure that every Administration Server has enough disk space for downloading and storing updates and patches.
Stages
Installing updates and fixing third-party software vulnerabilities on managed devices of isolated Administration Servers has the following stages:
- Configuring the Administration Server with internet access
Prepare your Administration Server with internet access to handle requests on required third-party software updates and to download patches.
- Configuring isolated Administration Servers
Prepare your isolated Administration Servers so they can regularly form lists of required updates and handle patches downloaded by the Administration Server with internet access. After configuring, isolated Administration Servers do not try to download patches from the internet anymore. Instead, they get updates through patches.
- Transmitting patches and installing updates on isolated Administration Servers
After you finished configuring Administration Servers, you can transmit the required updates lists and patches between the Administration Server with internet access and isolated Administration Servers. Next, updates from patches will be installed on managed devices by using the Install required updates and fix vulnerabilities task.
Results
Thus, the third-party software updates are transmitted to isolated Administration Servers and installed on connected managed devices by using Kaspersky Security Center. It is enough to configure Administration Servers once, and after that you can get updates as often as you need, for example, once or several times per day.
About fixing third-party software vulnerabilities in an isolated network
The process of fixing third-party software vulnerabilities in an isolated network is shown in the figure and described below. You can repeat this process periodically.
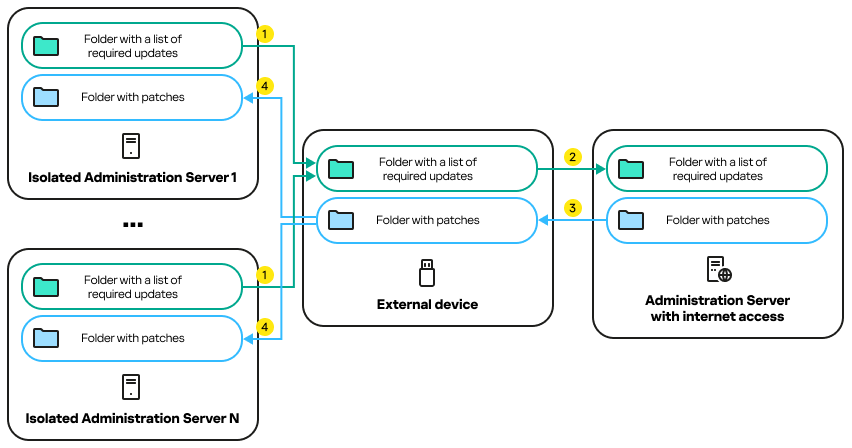
The process of transmitting patches and the list of required updates between the Administration Server with internet access and isolated Administration Servers
Every Administration Server isolated from the internet (hereinafter referred to as an isolated Administration Server) generates a list of updates that are required to be installed on managed devices connected to this Administration Server. The list of required updates is stored in a specific folder and presents a set of binary files. Each file has a name that contains the ID of the patch with the required update. As a result, every file in the list points to a specific patch.
By using an external device, you transfer the list of required updates from the isolated Administration Server to the allocated Administration Server with internet access. After that, the allocated Administration Server downloads patches from the internet and puts them in a separate folder.
When all patches are downloaded and located in the special folder for them, you move the patches to every isolated Administration Server from which you took a list of required updates. You save patches to the folder created especially for them on the isolated Administration Server. As a result, the Install required updates and fix vulnerabilities task runs patches and installs updates on managed devices of the isolated Administration Servers.
Configuring the Administration Server with internet access to fix vulnerabilities in an isolated network
To prepare for fixing vulnerabilities and transmitting patches in an isolated network, first configure an Administration Server with internet access, and then configure the isolated Administration Servers.
To configure an Administration Server with internet access:
- Create two folders on a disk where Administration Server is installed:
- Folder for the list of required updates
- Folder for patches
You can name these folders whatever you like.
- Grant the Modify access rights to the KLAdmins group in the created folders, by using the standard administrative tools of the operating system.
- Use the klscflag utility to write the paths to the folders in the Administration Server properties.
Run the Windows command prompt by using administrator rights, and then change your current directory to the directory with the klscflag utility. The klscflag utility is located in the folder where Administration Server is installed. The default installation path is <Disk>:\Program Files (x86)\Kaspersky Lab\Kaspersky Security Center.
- Enter the following commands at the Windows command prompt:
- To set the path to the folder for patches:
klscflag -fset -pv klserver -n VAPM_DATA_EXPORT_PATH -t s -v "<
path to the folder>" - To set the path to the folder for the list of required updates:
klscflag -fset -pv klserver -n VAPM_REQ_IMPORT_PATH -t s -v "<
path to the folder>"
Example:
klscflag -fset -pv klserver -n VAPM_DATA_EXPORT_PATH -t s -v "C:\FolderForPatches" - To set the path to the folder for patches:
- If necessary, use the klscflag utility to specify how often the Administration Server should check for new patch requests:
klscflag -fset -pv klserver -n VAPM_DATA_EXPORT_PERIOD_SEC -t d -v<value in seconds>The default value is 120 seconds.
Example:
klscflag -fset -pv klserver -n VAPM_DATA_EXPORT_PERIOD_SEC -t d -v 150 - Create the Find vulnerabilities and required updates task to obtain information about patches for the third-party software installed on the managed devices, and then set the task schedule.
- Create the Fix vulnerabilities task to specify patches for the third-party software used to fix vulnerabilities, and then set the task schedule.
Run tasks manually if you want them to run earlier than it is specified in the schedule. The order in which tasks are started is important. The Fix vulnerabilities task must be run after finishing the Find vulnerabilities and required updates task.
- Restart the Administration Server service.
Now, the Administration Server with internet access is ready to download and transmit updates to isolated Administration Servers. Before you start fixing vulnerabilities, configure the isolated Administration Servers.
Configuring isolated Administration Servers to fix vulnerabilities in an isolated network
After you finished configuring the Administration Server with internet access, prepare every isolated Administration Server in your network, so you can fix vulnerabilities and install updates on managed devices connected to isolated Administration Servers.
To configure isolated Administration Servers, perform the following actions on every Administration Server:
- Activate a license key for the Vulnerability and Patch Management (VAPM) feature.
- Create two folders on a disk where Administration Server is installed:
- Folder where the list of required updates will appear
- Folder for patches
You can name these folders whatever you like.
- Grant the Modify permission to the KLAdmins group in the created folders, by using the standard administrative tools of the operating system.
- Use the klscflag utility to write the paths to the folders in the Administration Server properties.
Run the Windows command prompt by using administrator rights, and then change your current directory to the directory with the klscflag utility. The klscflag utility is located in the folder where Administration Server is installed. The default installation path is <Disk>:\Program Files (x86)\Kaspersky Lab\Kaspersky Security Center.
- Enter the following commands at the Windows command prompt:
- To set the path to the folder for patches:
klscflag -fset -pv klserver -n VAPM_DATA_IMPORT_PATH -t s -v "<
path to the folder>" - To set the path to the folder for the list of required updates:
klscflag -fset -pv klserver -n VAPM_REQ_EXPORT_PATH -t s -v "<
path to the folder>"
Example:
klscflag -fset -pv klserver -n VAPM_DATA_IMPORT_PATH -t s -v "C:\FolderForPatches" - To set the path to the folder for patches:
- If necessary, use the klscflag utility to specify how often the isolated Administration Server should check for new patches:
klscflag -fset -pv klserver -n VAPM_DATA_IMPORT_PERIOD_SEC -t d -v <
value in seconds>The default value is 120 seconds.
Example:
klscflag -fset -pv klserver -n VAPM_DATA_IMPORT_PERIOD_SEC -t d -v 150 - If necessary, use the klscflag utility to calculate the SHA256 hashes of patches:
klscflag -fset -pv klserver -n VAPM_DATA_IMPORT_VERIFY_HASH -t d -v 1
If you enter this command, you can make sure that the patches have not been modified during their transfer to the isolated Administration Server and that you have received the correct patches containing the required updates.
By default, Kaspersky Security Center does not calculate the SHA256 hashes of patches. If you enable this option, after the isolated Administration Server receives patches, Kaspersky Security Center computes their hashes and compares the acquired values with the hashes stored in the Administration Server database. If the calculated hash does not match the hash in the database, an error occurs and you have to replace the incorrect patches.
- Create the Find vulnerabilities and required updates task to obtain information about patches for the third-party software installed on the managed devices, and then set the task schedule.
- Create the Fix vulnerabilities task to specify patches for the third-party software used to fix vulnerabilities, and then set the task schedule.
Run tasks manually if you want them to run earlier than it is specified in the schedule. The order in which tasks are started is important. The Fix vulnerabilities task must be run after finishing the Find vulnerabilities and required updates task.
- Restart the Administration Server service.
After configuring all Administration Servers, you can move patches and lists of required updates, and fix third-party software vulnerabilities on managed devices in the isolated network.
Transmitting patches and installing updates in an isolated network
After you have finished configuring Administration Servers, you can transfer patches containing the required updates from the Administration Server with internet access to isolated Administration Servers. You can transmit and install updates as often as you need, for example, once or several times per day.
You need an external device, such as a removable drive, to transfer patches and the list of required updates between Administration Servers. Therefore, make sure that the external device has enough disk space for downloading and storing patches.
The process of transmitting patches and the list of required updates is shown in the figure and described below:

The process of transmitting patches and the list of required updates between the Administration Server with internet access and isolated Administration Servers
To install updates and fix vulnerabilities on managed devices connected to isolated Administration Servers:
- Start the Install required updates and fix vulnerabilities task if it is not yet running.
- Connect an external device to any isolated Administration Server.
- Create two folders on the external device: one for the list of required updates and one for patches. You can name these folders whatever you like.
If you created these folders earlier, clear them.
- Copy the list of required updates from every isolated Administration Server and paste this list into the folder for the list of required updates on the external device.
As a result, you unite all lists acquired from all isolated Administration Servers into one folder. This folder contains binary files with the IDs of patches required for all isolated Administration Servers.
- Connect the external device to the Administration Server with internet access.
- Copy the list of required updates from the external device and paste this list into the folder for the list of required updates on the Administration Server with internet access.
All required patches are automatically downloaded from the internet to the folder for patches on the Administration Server. This can take several hours.
- Make sure that all required patches are downloaded. For this purpose, you can do one of the following:
- Check the folder for patches on the Administration Server with internet access. All patches that were specified in the list of required updates should be downloaded to the necessary folder. This is more convenient if a small number of patches is required.
- Prepare a special script, for example, a shell script. If you get a large number of patches, this will be difficult to check on your own that all patches have been downloaded. In such cases, it is better to automate the check.
- Copy the patches from the Administration Server with internet access and paste them into the corresponding folder on your external device.
- Transfer the patches to every isolated Administration Server. Put the patches into a specific folder for them.
As a result, every isolated Administration Server creates an actual list of updates that are required for managed devices connected to the current Administration Server. After the Administration Server with internet access receives the list of required updates, the Administration Server downloads patches from the internet. When these patches appear on isolated Administration Servers, the Install required updates and fix vulnerabilities task handles the patches. Thus, updates are installed on managed devices and third-party software vulnerabilities are fixed.
When the Install required updates and fix vulnerabilities task is running, do not reboot the Administration Server device and do not run the Backup of Administration Server data task (it will also cause a reboot). As a result, the Install required updates and fix vulnerabilities task is interrupted, and updates are not installed. In this case, you have to restart this task manually or wait for the task to start according to the configured schedule.
Disabling the option to transmit patches and install updates in an isolated network
You can disable transmitting patches on isolated Administration Servers, for example, if you decided to take one or more Administration Servers out of an isolated network. Thus, you can reduce the number of patches and time to download them.
To disable the option to transmit patches on isolated Administration Servers:
- If you want to take all Administration Servers out of isolation, in the properties of the Administration Server with internet access, delete the paths to the folders for patches and the list of required updates. If you want to keep some Administration Servers in an isolated network, skip this step.
Run the Windows command prompt by using administrator rights, and then change your current directory to the directory with the klscflag utility. The klscflag utility is located in the folder where Administration Server is installed. The default installation path is <Disk>:\Program Files (x86)\Kaspersky Lab\Kaspersky Security Center.
Enter the following commands at the command prompt:
- To delete the path to the folder for patches:
klscflag -fset -pv klserver -n VAPM_DATA_EXPORT_PATH -t s -v ""
- To delete the path to the folder for the list of required updates:
klscflag -fset -pv klserver -n VAPM_REQ_IMPORT_PATH -t s -v ""
- To delete the path to the folder for patches:
- Restart the Administration Server service if you deleted the paths to the folders on this Administration Server.
- In the properties of every Administration Server that you want to take out of isolation, delete the paths to the folders for patches and the list of required updates.
Enter the following commands at the Windows command prompt, using administrator rights:
- To delete the path to the folder for patches:
klscflag -fset -pv klserver -n VAPM_DATA_IMPORT_PATH -t s -v ""
- To delete the path to the folder for the list of required updates:
klscflag -fset -pv klserver -n VAPM_REQ_EXPORT_PATH -t s -v ""
- To delete the path to the folder for patches:
- Restart the service of every Administration Server on which you deleted the paths to the folders.
As a result, if you reconfigured the Administration Server with internet access, you will no longer receive patches through Kaspersky Security Center. If you reconfigured only some isolated Administration Servers, for example, taking some of them out of the isolated network, you will get patches only for the remaining isolated Administration Servers.
If you want to start fixing vulnerabilities on disabled isolated Administration Servers in the future, you have to configure these Administration Servers and the Administration Server with internet access once again.