Contents
- Fixing third-party software vulnerabilities
- Scenario: Finding and fixing third-party software vulnerabilities
- About finding and fixing software vulnerabilities
- Viewing information about software vulnerabilities
- Viewing statistics of vulnerabilities on managed devices
- Scanning applications for vulnerabilities
- Fixing vulnerabilities in applications
- Fixing vulnerabilities in an isolated network
- Scenario: Fixing third-party software vulnerabilities in an isolated network
- About fixing third-party software vulnerabilities in an isolated network
- Configuring the Administration Server with internet access to fix vulnerabilities in an isolated network
- Configuring isolated Administration Servers to fix vulnerabilities in an isolated network
- Transmitting patches and installing updates in an isolated network
- Disabling the option to transmit patches and install updates in an isolated network
- Ignoring software vulnerabilities
- Selecting user fixes for vulnerabilities in third-party software
- Rules for update installation
Fixing third-party software vulnerabilities
This section describes the features of Kaspersky Security Center that relate to fixing vulnerabilities in the software installed on managed devices.
Scenario: Finding and fixing third-party software vulnerabilities
This section provides a scenario for finding and fixing vulnerabilities on the managed devices running Windows. You can find and fix software vulnerabilities in the operating system and in third-party software, including Microsoft software.
Prerequisites
- Kaspersky Security Center is deployed in your organization.
- There are managed devices running Windows in your organization.
- Internet connection is required for Administration Server to perform the following tasks:
- To make a list of recommended fixes for vulnerabilities in Microsoft software. The list is created and regularly updated by Kaspersky specialists.
- To fix vulnerabilities in third-part software other than Microsoft software.
Stages
Finding and fixing software vulnerabilities proceeds in stages:
- Scanning for vulnerabilities in the software installed on the managed devices
To find vulnerabilities in the software installed on the managed devices, run the Find vulnerabilities and required updates task. When this task is complete, Kaspersky Security Center receives the lists of detected vulnerabilities and required updates for the third-party software installed on the devices that you specified in the task properties.
The Find vulnerabilities and required updates task is created automatically by Kaspersky Security Center Quick Start Wizard. If you did not run the Wizard, start it now or create the task manually.
How-to instructions:
- Administration Console: Scanning applications for vulnerabilities, Scheduling the Find vulnerabilities and required updates task
- Kaspersky Security Center Web Console: Creating the Find vulnerabilities and required updates task, Find vulnerabilities and required updates task settings
- Analyzing the list of detected software vulnerabilities
View the Software vulnerabilities list and decide which vulnerabilities are to be fixed. To view detailed information about each vulnerability, click the vulnerability name in the list. For each vulnerability in the list, you can also view the statistics on the vulnerability on managed devices.
How-to instructions:
- Administration Console: Viewing information about software vulnerabilities, Viewing statistics of vulnerabilities on managed devices
- Kaspersky Security Center Web Console: Viewing information about software vulnerabilities, Viewing statistics of vulnerabilities on managed devices
- Configuring vulnerabilities fix
When the software vulnerabilities are detected, you can fix the software vulnerabilities on the managed devices by using the Install required updates and fix vulnerabilities task or the Fix vulnerabilities task.
The Install required updates and fix vulnerabilities task is used to update and fix vulnerabilities in third-party software, including Microsoft software, installed on the managed devices. This task allows you to install multiple updates and fix multiple vulnerabilities according to certain rules. Note that this task can be created only if you have the license for the Vulnerability and Patch Management feature. To fix software vulnerabilities the Install required updates and fix vulnerabilities task uses recommended software updates.
The Fix vulnerabilities task does not require the license option for the Vulnerability and Patch Management feature. To use this task, you must manually specify user fixes for vulnerabilities in third-party software listed in the task settings. The Fix vulnerabilities task uses recommended fixes for Microsoft software and user fixes for third-party software.
You can start Vulnerabilities Fix Wizard that creates one of these tasks automatically, or you can create one of these tasks manually.
How-to instructions:
- Administration Console: Selecting user fixes for vulnerabilities in third-party software, Fixing vulnerabilities in applications
- Kaspersky Security Center Web Console: Selecting user fixes for vulnerabilities in third-party software, Fixing vulnerabilities in third-party software, Creating the Install required updates and fix vulnerabilities task
- Scheduling the tasks
To be sure that the vulnerabilities list is always up-to-date, schedule the Find vulnerabilities and required updates task to run it automatically from time to time. The recommended average frequency is once a week.
If you have created the Install required updates and fix vulnerabilities task, you can schedule it to run with the same frequency as the Find vulnerabilities and required updates task or less often. When scheduling the Fix vulnerabilities task, note that you have to select fixes for Microsoft software or specify user fixes for third-party software every time before starting the task.
When scheduling the tasks, make sure that a task to fix vulnerability starts after the Find vulnerabilities and required updates task is complete.
- Ignoring software vulnerabilities (optional)
If you want, you can ignore software vulnerabilities to be fixed on all managed devices or only on the selected managed devices.
How-to instructions:
- Administration Console: Ignoring software vulnerabilities
- Kaspersky Security Center Web Console: Ignoring software vulnerabilities
- Running a vulnerability fix task
Start the Install required updates and fix vulnerabilities task or the Fix vulnerability task. When the task is complete, make sure that it has the Completed successfully status in the task list.
- Create the report on results of fixing software vulnerabilities (optional)
To view detailed statistics on the vulnerabilities fix, generate the Report on vulnerabilities. The report displays information about software vulnerabilities that are not fixed. Thus you can have an idea about finding and fixing vulnerabilities in third-party software, including Microsoft software, in your organization.
How-to instructions:
- Administration Console: Creating and viewing a report
- Kaspersky Security Center Web Console: Generating and viewing a report
- Checking configuration of finding and fixing vulnerabilities in third-party software
Be sure that you have done the following:
- Obtained and reviewed the list of software vulnerabilities on managed devices
- Ignored software vulnerabilities if you wanted
- Configured the task to fix vulnerabilities
- Scheduled the tasks to find and to fix software vulnerabilities so that they start sequentially
- Checked that the task to fix software vulnerabilities was run
Results
If you have created and configured the Install required updates and fix vulnerabilities task, the vulnerabilities are fixed on the managed devices automatically. When the task is run, it correlates the list of available software updates to the rules specified in the task settings. All software updates that meet the criteria in the rules will be downloaded to the Administration Server repository and will be installed to fix software vulnerabilities.
If you have created the Fix vulnerabilities task, only software vulnerabilities in Microsoft software are fixed.
About finding and fixing software vulnerabilities
Kaspersky Security Center detects and fixes software
on managed devices running Microsoft Windows families operating systems. Vulnerabilities are detected in the operating system and in third-party software, including Microsoft software.Updates functionality (including providing anti-virus signature updates and codebase updates), as well as KSN functionality may not be available in the software in the U.S.
Finding software vulnerabilities
To find software vulnerabilities, Kaspersky Security Center uses characteristics from the database of known vulnerabilities. This database is created by Kaspersky specialists. It contains information about vulnerabilities, such as vulnerability description, vulnerability detect date, vulnerability severity level. You can find the details of software vulnerabilities on Kaspersky website.
Kaspersky Security Center uses the Find vulnerabilities and required updates task to find software vulnerabilities.
Fixing software vulnerabilities
To fix software vulnerabilities Kaspersky Security Center uses software updates issued by the software vendors. The software updates metadata is downloaded to the Administration Server repository as a result of the following tasks run:
- Download updates to the Administration Server repository. This task is intended to download updates metadata for Kaspersky and third-party software. This task is created automatically by the Kaspersky Security Center Quick Start Wizard. You can create the Download updates to the Administration Server repository task manually.
- Perform Windows Update synchronization. This task is intended to download updates metadata for Microsoft software.
Software updates to fix vulnerabilities can be represented as full distribution packages or patches. Software updates that fix software vulnerabilities are named fixes. Recommended fixes are those that are recommended for installation by Kaspersky specialists. User fixes are those that are manually specified for installation by users. To install a user fix, you have to create an installation package containing this fix.
If you have the Kaspersky Security Center license with the Vulnerability and Patch Management feature, to fix software vulnerabilities you can use Install required updates and fix vulnerabilities task. This task automatically fixes multiple vulnerabilities installing recommended fixes. For this task, you can manually configure certain rules to fix multiple vulnerabilities.
If you do not have the Kaspersky Security Center license with the Vulnerability and Patch Management feature, to fix software vulnerabilities, you can use the Fix vulnerabilities task. By means of this task, you can fix vulnerabilities by installing recommended fixes for Microsoft software and user fixes for other third-party software.
For security reasons, any third-party software updates that you install by using the Vulnerability and Patch Management feature are automatically scanned for malware by Kaspersky technologies. These technologies are used for automatic file checks and include virus scanning, static analysis, dynamic analysis, behavior analysis in the sandbox environment, and machine learning.
Kaspersky experts do not perform manual analysis of third-party software updates that can be installed by using the Vulnerability and Patch Management feature. In addition, Kaspersky experts do not search for vulnerabilities (known or unknown) or undocumented features in such updates, as well as do not perform other types of analysis of the updates other than the specified in the paragraph above.
A user interaction may be required when you update a third-party application or fix a vulnerability in a third-party application on a managed device. For example, the user may be prompted to close the third-party application if it is currently open.
To fix some software vulnerabilities, you must accept the End User License Agreement (EULA) for installing the software if EULA acceptance is requested. If you decline the EULA, the software vulnerability is not fixed.
Viewing information about software vulnerabilities
To view a list of vulnerabilities detected on client devices,
In the Advanced → Application management folder in the console tree, select the Software vulnerabilities subfolder.
The page displays a list of vulnerabilities in applications detected on managed devices.
To obtain information about a selected vulnerability,
Select Properties from the context menu of the vulnerability.
The properties window of the vulnerability opens, displaying the following information:
- Application in which the vulnerability has been detected.
- List of devices on which the vulnerability has been detected.
- Information on whether the vulnerability has been fixed.
To view the report on all detected vulnerabilities,
In the Software vulnerabilities folder, click the View report on vulnerabilities link.
A report on vulnerabilities in applications installed on devices will be generated. You can view this report in the node with the name of the relevant Administration Server, by opening the Reports tab.
Viewing statistics of vulnerabilities on managed devices
You can view statistics for each software vulnerability on managed devices. Statistics are represented as a diagram. The diagram displays the number of devices with the following statuses:
- Ignored on: <number of devices>. This status is assigned if, in the vulnerability properties, you have manually set the option to ignore the vulnerability.
- Fixed on: <number of devices>. This status is assigned if the task to fix the vulnerability has successfully completed.
- Fix scheduled on: <number of devices>. This status is assigned if you have created the task to fix the vulnerability, but the task is not performed yet.
- Patch applied on: <number of devices>. This status is assigned if you have manually selected a software update to fix the vulnerability, but this software update has not fixed the vulnerability.
- Fix required on: <number of devices>. This status is assigned if the vulnerability was fixed only on some managed devices, and the vulnerability is required to be fixed on more managed devices.
To view the statistics of a vulnerability on managed devices:
- In the Advanced → Application management folder in the console tree, select the Software vulnerabilities subfolder.
The page displays a list of vulnerabilities in applications detected on managed devices.
- Select a vulnerability for which you want to view the statistics.
In the block for working with a selected object, a diagram of the vulnerability statuses is displayed. Clicking a status opens a list of devices on which the vulnerability has the selected status.
Scanning applications for vulnerabilities
If you have configured the application through the Quick Start Wizard, the Vulnerability scan task is created automatically. You can view the task in the Managed devices folder, on the Tasks tab.
To create a task for vulnerability scanning in applications installed on client devices:
- In the console tree, select Advanced → Application management, and then select the Software vulnerabilities subfolder.
- In the workspace, select Additional actions → Configure vulnerability scan.
If a task for vulnerability scanning already exists, the Tasks tab of the Managed devices folder is displayed, with the existing task selected. Otherwise, the Find Vulnerabilities and Required Updates Task Creation Wizard starts. Follow the steps of the Wizard.
- In the Select the task type window, select Find vulnerabilities and required updates.
- On the Settings page of the Wizard, specify the task settings as follows:
- On the Configure task schedule page of the Wizard, you can create a schedule for task start. If necessary, specify the following settings:
- On the Define the task name page of the Wizard, specify the name for the task that you are creating. A task name cannot be more than 100 characters long and cannot include any special characters ("*<>?\:|).
- On the Finish task creation page of the Wizard, click the Finish button to close the Wizard.
If you want the task to start as soon as the Wizard finishes, select the Run the task after the Wizard finishes check box.
After the Wizard completes its operation, the Find vulnerabilities and required updates task appears in the list of tasks in the Managed devices folder, on the Tasks tab.
In addition to the settings that you specify during task creation, you can change other properties of a created task.
When the Find vulnerabilities and required updates task is complete, Administration Server displays a list of vulnerabilities found in applications installed on the device; it also displays all software updates required to fix the vulnerabilities detected.
If the task results contain the 0x80240033 "Windows Update Agent error 80240033 ("License terms could not be downloaded.")" error, you can resolve this issue through the Windows Registry.
Administration Server does not display the list of required software updates when you sequentially run two tasks—the Perform Windows Update synchronization task that has the Download express installation files option disabled, and then the Find vulnerabilities and required updates task. In order to view the list of required software updates, you must run the Find vulnerabilities and required updates task again.
Network Agent receives information about any available Windows updates and other Microsoft product updates from Windows Update or the Administration Server, if the Administration Server acts as the WSUS server. Information is transmitted when applications are started (if this is provided for by the policy) and at each routine run of the Find vulnerabilities and required updates task on client devices.
You can find the details of third-party software that can be updated through Kaspersky Security Center by visiting the Technical Support website, on the Kaspersky Security Center page, in the Server Management section.
Fixing vulnerabilities in applications
If you have selected Find and install required updates on the Update management settings page of the Quick Start Wizard, the Install required updates and fix vulnerabilities task is created automatically. The task is displayed in the workspace of the Managed devices folder, on the Tasks tab.
Otherwise, you can do any of the following:
- Create a task for fixing vulnerabilities by installing available updates.
- Add a rule for fixing a vulnerability to an existing vulnerability fix task.
A user interaction may be required when you update a third-party application or fix a vulnerability in a third-party application on a managed device. For example, the user may be prompted to close the third-party application if it is currently open.
Fixing vulnerabilities by creating a vulnerability fix task
You can do any of the following:
- Create a task for fixing multiple vulnerabilities that meet certain rules.
- Select a vulnerability and create a task for fixing it and similar vulnerabilities.
To fix vulnerabilities that meet certain rules:
- In the console tree, select Administration Server on devices for which you want to fix vulnerabilities.
- In the View menu of the main application window, select Configure interface.
- In the window that opens, select the Display Vulnerability and Patch Management check box, and then click OK.
- In the window with the application message, click OK.
- Restart the Administration Console, so the changes take effect.
- In the console tree, select the Managed devices folder.
- In the workspace, select the Tasks tab.
- Click the Create a task button to run the Add Task Wizard. Follow the steps of the Wizard.
- On the Select the task type page of the Wizard, select the Install required updates and fix vulnerabilities task.
If the task is not displayed, check whether your account has the Read, Modify, and Execute rights for the System management: Vulnerability and patch management functional area. You cannot create and configure the Install required updates and fix vulnerabilities task without these access rights.
- On the Settings page of the Wizard, specify the task settings as follows:
- On the Selecting an operating system restart option page of the Wizard, select the action to perform when the operating system on client devices must be restarted after the operation:
- On the Configure task schedule page of the Wizard, you can create a schedule for task start. If necessary, specify the following settings:
- On the Define the task name page of the Wizard, specify the name for the task that you are creating. A task name cannot be more than 100 characters long and cannot include any special characters ("*<>?\:|).
- On the Finish task creation page of the Wizard, click the Finish button to close the Wizard.
If you want the task to start as soon as the Wizard finishes, select the Run the task after the Wizard finishes check box.
After the Wizard completes its operation, the Install required updates and fix vulnerabilities task is created and displayed in the Tasks folder.
In addition to the settings that you specify during task creation, you can change other properties of a created task.
If the task results contain the 0x80240033 "Windows Update Agent error 80240033 ("License terms could not be downloaded.")" error, you can resolve this issue through the Windows Registry.
To fix a specific vulnerability and similar ones:
- In the Advanced → Application management folder in the console tree, select the Software vulnerabilities subfolder.
- Select the vulnerability that you want to fix.
- Click the Run Vulnerability Fix Wizard button.
The Vulnerability Fix Wizard starts.
The Vulnerability Fix Wizard features are only available under the Vulnerability and Patch Management license.
Follow the steps of the Wizard.
- In the Search for existing vulnerability fix tasks window, specify the following parameters:
- If you choose to search for existing vulnerability fix tasks and if the search retrieves some tasks, you can view properties of these tasks or start them manually. No further actions are required.
Otherwise, click the New vulnerability fix task button.
- Select the type of the vulnerability fix rule to be added to the new task, and then click the Finish button.
- Make your choice in the displayed prompt about installing all previous application updates. Click Yes if you agree to the installation of successive application versions incrementally if this is required for installing the selected updates. Click No if you want to update applications in a straightforward fashion, without installing successive versions. If installing the selected updates is not possible without installing previous versions of applications, the updating of the application fails.
The Updates Installation and Vulnerabilities Fix Task Creation Wizard starts. Follow the steps of the Wizard.
- On the Selecting an operating system restart option page of the Wizard, select the action to perform when the operating system on client devices must be restarted after the operation:
- On the Select devices to which the task will be assigned page of the Wizard, select one of the following options:
- On the Configure task schedule page of the Wizard, you can create a schedule for task start. If necessary, specify the following settings:
- On the Define the task name page of the Wizard, specify the name for the task that you are creating. A task name cannot be more than 100 characters long and cannot include any special characters ("*<>?\:|).
- On the Finish task creation page of the Wizard, click the Finish button to close the Wizard.
If you want the task to start as soon as the Wizard finishes, select the Run the task after the Wizard finishes check box.
When the Wizard completes, the Install required updates and fix vulnerabilities task is created and displayed in the Tasks folder.
In addition to the settings that you specify during task creation, you can change other properties of a created task.
Fixing a vulnerability by adding a rule to an existing vulnerability fix task
To fix a vulnerability by adding a rule to an existing vulnerability fix task:
- In the Advanced → Application management folder in the console tree, select the Software vulnerabilities subfolder.
- Select the vulnerability that you want to fix.
- Click the Run Vulnerability Fix Wizard button.
The Vulnerability Fix Wizard starts.
The Vulnerability Fix Wizard features are only available under the Vulnerability and Patch Management license.
Follow the steps of the Wizard.
- In the Search for existing vulnerability fix tasks window, specify the following parameters:
- If you choose to search for existing vulnerability fix tasks and if the search retrieves some tasks, you can view properties of these tasks or start them manually. No further actions are required.
Otherwise, click the Add vulnerability fix rule to existing task button.
- Select the task to which you want to add a rule, and then click the Add rule button.
Also, you can view properties of the existing tasks, start them manually, or create a new task.
- Select the type of rule to be added to the selected task, and then click the Finish button.
- Make your choice in the displayed prompt about installing all previous application updates. Click Yes if you agree to the installation of successive application versions incrementally if this is required for installing the selected updates. Click No if you want to update applications in a straightforward fashion, without installing successive versions. If installing the selected updates is not possible without installing previous versions of applications, the updating of the application fails.
A new rule for fixing the vulnerability is added to the existing Install required updates and fix vulnerabilities task.
Fixing vulnerabilities in an isolated network
This section describes the steps that you can take to fix third-party software vulnerabilities on managed devices connected to Administration Servers that do not have internet access.
Scenario: Fixing third-party software vulnerabilities in an isolated network
You can install updates and fix vulnerabilities of the third-party software installed on managed devices in an isolated network. Such networks include Administration Servers and managed devices connected to them that have no internet access. To fix vulnerabilities in this kind of network, you need an Administration Server connected to the internet. Then, you will be able to download patches (required updates) by using the Administration Server with internet access, and then transmit the patches to isolated Administration Servers.
You can download the third-party software updates issued by software vendors, but you cannot download updates for Microsoft software on isolated Administration Servers by using Kaspersky Security Center.
To find out how the process of fixing vulnerabilities in an isolated network works, see the description and scheme of this process.
Prerequisites
Before you start, do the following:
- Allocate one device for connecting to the internet and downloading patches. This device will be counted as the Administration Server with internet access.
- Install Kaspersky Security Center, no earlier than version 14, on the following devices:
- Allocated device, which will act as the Administration Server with internet access
- Isolated devices, which will act as the Administration Servers isolated from the internet (hereinafter referred to as isolated Administration Servers)
- Make sure that every Administration Server has enough disk space for downloading and storing updates and patches.
Stages
Installing updates and fixing third-party software vulnerabilities on managed devices of isolated Administration Servers has the following stages:
- Configuring the Administration Server with internet access
Prepare your Administration Server with internet access to handle requests on required third-party software updates and to download patches.
- Configuring isolated Administration Servers
Prepare your isolated Administration Servers so they can regularly form lists of required updates and handle patches downloaded by the Administration Server with internet access. After configuring, isolated Administration Servers do not try to download patches from the internet anymore. Instead, they get updates through patches.
- Transmitting patches and installing updates on isolated Administration Servers
After you finished configuring Administration Servers, you can transmit the required updates lists and patches between the Administration Server with internet access and isolated Administration Servers. Next, updates from patches will be installed on managed devices by using the Install required updates and fix vulnerabilities task.
Results
Thus, the third-party software updates are transmitted to isolated Administration Servers and installed on connected managed devices by using Kaspersky Security Center. It is enough to configure Administration Servers once, and after that you can get updates as often as you need, for example, once or several times per day.
About fixing third-party software vulnerabilities in an isolated network
The process of fixing third-party software vulnerabilities in an isolated network is shown in the figure and described below. You can repeat this process periodically.
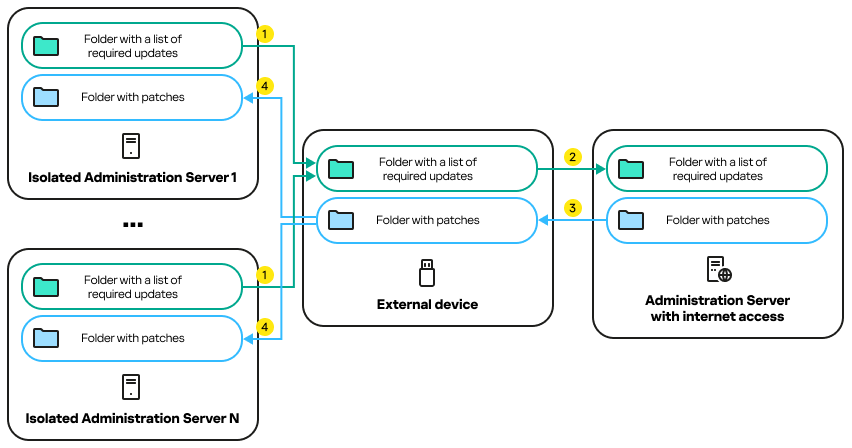
The process of transmitting patches and the list of required updates between the Administration Server with internet access and isolated Administration Servers
Every Administration Server isolated from the internet (hereinafter referred to as an isolated Administration Server) generates a list of updates that are required to be installed on managed devices connected to this Administration Server. The list of required updates is stored in a specific folder and presents a set of binary files. Each file has a name that contains the ID of the patch with the required update. As a result, every file in the list points to a specific patch.
By using an external device, you transfer the list of required updates from the isolated Administration Server to the allocated Administration Server with internet access. After that, the allocated Administration Server downloads patches from the internet and puts them in a separate folder.
When all patches are downloaded and located in the special folder for them, you move the patches to every isolated Administration Server from which you took a list of required updates. You save patches to the folder created especially for them on the isolated Administration Server. As a result, the Install required updates and fix vulnerabilities task runs patches and installs updates on managed devices of the isolated Administration Servers.
Configuring the Administration Server with internet access to fix vulnerabilities in an isolated network
To prepare for fixing vulnerabilities and transmitting patches in an isolated network, first configure an Administration Server with internet access, and then configure the isolated Administration Servers.
To configure an Administration Server with internet access:
- Create two folders on a disk where Administration Server is installed:
- Folder for the list of required updates
- Folder for patches
You can name these folders whatever you like.
- Grant the Modify access rights to the KLAdmins group in the created folders, by using the standard administrative tools of the operating system.
- Use the klscflag utility to write the paths to the folders in the Administration Server properties.
Run the Windows command prompt by using administrator rights, and then change your current directory to the directory with the klscflag utility. The klscflag utility is located in the folder where Administration Server is installed. The default installation path is <Disk>:\Program Files (x86)\Kaspersky Lab\Kaspersky Security Center.
- Enter the following commands at the Windows command prompt:
- To set the path to the folder for patches:
klscflag -fset -pv klserver -n VAPM_DATA_EXPORT_PATH -t s -v "<
path to the folder>" - To set the path to the folder for the list of required updates:
klscflag -fset -pv klserver -n VAPM_REQ_IMPORT_PATH -t s -v "<
path to the folder>"
Example:
klscflag -fset -pv klserver -n VAPM_DATA_EXPORT_PATH -t s -v "C:\FolderForPatches" - To set the path to the folder for patches:
- If necessary, use the klscflag utility to specify how often the Administration Server should check for new patch requests:
klscflag -fset -pv klserver -n VAPM_DATA_EXPORT_PERIOD_SEC -t d -v<value in seconds>The default value is 120 seconds.
Example:
klscflag -fset -pv klserver -n VAPM_DATA_EXPORT_PERIOD_SEC -t d -v 150 - Create the Find vulnerabilities and required updates task to obtain information about patches for the third-party software installed on the managed devices, and then set the task schedule.
- Create the Fix vulnerabilities task to specify patches for the third-party software used to fix vulnerabilities, and then set the task schedule.
Run tasks manually if you want them to run earlier than it is specified in the schedule. The order in which tasks are started is important. The Fix vulnerabilities task must be run after finishing the Find vulnerabilities and required updates task.
- Restart the Administration Server service.
Now, the Administration Server with internet access is ready to download and transmit updates to isolated Administration Servers. Before you start fixing vulnerabilities, configure the isolated Administration Servers.
Configuring isolated Administration Servers to fix vulnerabilities in an isolated network
After you finished configuring the Administration Server with internet access, prepare every isolated Administration Server in your network, so you can fix vulnerabilities and install updates on managed devices connected to isolated Administration Servers.
To configure isolated Administration Servers, perform the following actions on every Administration Server:
- Activate a license key for the Vulnerability and Patch Management (VAPM) feature.
- Create two folders on a disk where Administration Server is installed:
- Folder where the list of required updates will appear
- Folder for patches
You can name these folders whatever you like.
- Grant the Modify permission to the KLAdmins group in the created folders, by using the standard administrative tools of the operating system.
- Use the klscflag utility to write the paths to the folders in the Administration Server properties.
Run the Windows command prompt by using administrator rights, and then change your current directory to the directory with the klscflag utility. The klscflag utility is located in the folder where Administration Server is installed. The default installation path is <Disk>:\Program Files (x86)\Kaspersky Lab\Kaspersky Security Center.
- Enter the following commands at the Windows command prompt:
- To set the path to the folder for patches:
klscflag -fset -pv klserver -n VAPM_DATA_IMPORT_PATH -t s -v "<
path to the folder>" - To set the path to the folder for the list of required updates:
klscflag -fset -pv klserver -n VAPM_REQ_EXPORT_PATH -t s -v "<
path to the folder>"
Example:
klscflag -fset -pv klserver -n VAPM_DATA_IMPORT_PATH -t s -v "C:\FolderForPatches" - To set the path to the folder for patches:
- If necessary, use the klscflag utility to specify how often the isolated Administration Server should check for new patches:
klscflag -fset -pv klserver -n VAPM_DATA_IMPORT_PERIOD_SEC -t d -v <
value in seconds>The default value is 120 seconds.
Example:
klscflag -fset -pv klserver -n VAPM_DATA_IMPORT_PERIOD_SEC -t d -v 150 - If necessary, use the klscflag utility to calculate the SHA256 hashes of patches:
klscflag -fset -pv klserver -n VAPM_DATA_IMPORT_VERIFY_HASH -t d -v 1
If you enter this command, you can make sure that the patches have not been modified during their transfer to the isolated Administration Server and that you have received the correct patches containing the required updates.
By default, Kaspersky Security Center does not calculate the SHA256 hashes of patches. If you enable this option, after the isolated Administration Server receives patches, Kaspersky Security Center computes their hashes and compares the acquired values with the hashes stored in the Administration Server database. If the calculated hash does not match the hash in the database, an error occurs and you have to replace the incorrect patches.
- Create the Find vulnerabilities and required updates task to obtain information about patches for the third-party software installed on the managed devices, and then set the task schedule.
- Create the Fix vulnerabilities task to specify patches for the third-party software used to fix vulnerabilities, and then set the task schedule.
Run tasks manually if you want them to run earlier than it is specified in the schedule. The order in which tasks are started is important. The Fix vulnerabilities task must be run after finishing the Find vulnerabilities and required updates task.
- Restart the Administration Server service.
After configuring all Administration Servers, you can move patches and lists of required updates, and fix third-party software vulnerabilities on managed devices in the isolated network.
Transmitting patches and installing updates in an isolated network
After you have finished configuring Administration Servers, you can transfer patches containing the required updates from the Administration Server with internet access to isolated Administration Servers. You can transmit and install updates as often as you need, for example, once or several times per day.
You need an external device, such as a removable drive, to transfer patches and the list of required updates between Administration Servers. Therefore, make sure that the external device has enough disk space for downloading and storing patches.
The process of transmitting patches and the list of required updates is shown in the figure and described below:

The process of transmitting patches and the list of required updates between the Administration Server with internet access and isolated Administration Servers
To install updates and fix vulnerabilities on managed devices connected to isolated Administration Servers:
- Start the Install required updates and fix vulnerabilities task if it is not yet running.
- Connect an external device to any isolated Administration Server.
- Create two folders on the external device: one for the list of required updates and one for patches. You can name these folders whatever you like.
If you created these folders earlier, clear them.
- Copy the list of required updates from every isolated Administration Server and paste this list into the folder for the list of required updates on the external device.
As a result, you unite all lists acquired from all isolated Administration Servers into one folder. This folder contains binary files with the IDs of patches required for all isolated Administration Servers.
- Connect the external device to the Administration Server with internet access.
- Copy the list of required updates from the external device and paste this list into the folder for the list of required updates on the Administration Server with internet access.
All required patches are automatically downloaded from the internet to the folder for patches on the Administration Server. This can take several hours.
- Make sure that all required patches are downloaded. For this purpose, you can do one of the following:
- Check the folder for patches on the Administration Server with internet access. All patches that were specified in the list of required updates should be downloaded to the necessary folder. This is more convenient if a small number of patches is required.
- Prepare a special script, for example, a shell script. If you get a large number of patches, this will be difficult to check on your own that all patches have been downloaded. In such cases, it is better to automate the check.
- Copy the patches from the Administration Server with internet access and paste them into the corresponding folder on your external device.
- Transfer the patches to every isolated Administration Server. Put the patches into a specific folder for them.
As a result, every isolated Administration Server creates an actual list of updates that are required for managed devices connected to the current Administration Server. After the Administration Server with internet access receives the list of required updates, the Administration Server downloads patches from the internet. When these patches appear on isolated Administration Servers, the Install required updates and fix vulnerabilities task handles the patches. Thus, updates are installed on managed devices and third-party software vulnerabilities are fixed.
When the Install required updates and fix vulnerabilities task is running, do not reboot the Administration Server device and do not run the Backup of Administration Server data task (it will also cause a reboot). As a result, the Install required updates and fix vulnerabilities task is interrupted, and updates are not installed. In this case, you have to restart this task manually or wait for the task to start according to the configured schedule.
Disabling the option to transmit patches and install updates in an isolated network
You can disable transmitting patches on isolated Administration Servers, for example, if you decided to take one or more Administration Servers out of an isolated network. Thus, you can reduce the number of patches and time to download them.
To disable the option to transmit patches on isolated Administration Servers:
- If you want to take all Administration Servers out of isolation, in the properties of the Administration Server with internet access, delete the paths to the folders for patches and the list of required updates. If you want to keep some Administration Servers in an isolated network, skip this step.
Run the Windows command prompt by using administrator rights, and then change your current directory to the directory with the klscflag utility. The klscflag utility is located in the folder where Administration Server is installed. The default installation path is <Disk>:\Program Files (x86)\Kaspersky Lab\Kaspersky Security Center.
Enter the following commands at the command prompt:
- To delete the path to the folder for patches:
klscflag -fset -pv klserver -n VAPM_DATA_EXPORT_PATH -t s -v ""
- To delete the path to the folder for the list of required updates:
klscflag -fset -pv klserver -n VAPM_REQ_IMPORT_PATH -t s -v ""
- To delete the path to the folder for patches:
- Restart the Administration Server service if you deleted the paths to the folders on this Administration Server.
- In the properties of every Administration Server that you want to take out of isolation, delete the paths to the folders for patches and the list of required updates.
Enter the following commands at the Windows command prompt, using administrator rights:
- To delete the path to the folder for patches:
klscflag -fset -pv klserver -n VAPM_DATA_IMPORT_PATH -t s -v ""
- To delete the path to the folder for the list of required updates:
klscflag -fset -pv klserver -n VAPM_REQ_EXPORT_PATH -t s -v ""
- To delete the path to the folder for patches:
- Restart the service of every Administration Server on which you deleted the paths to the folders.
As a result, if you reconfigured the Administration Server with internet access, you will no longer receive patches through Kaspersky Security Center. If you reconfigured only some isolated Administration Servers, for example, taking some of them out of the isolated network, you will get patches only for the remaining isolated Administration Servers.
If you want to start fixing vulnerabilities on disabled isolated Administration Servers in the future, you have to configure these Administration Servers and the Administration Server with internet access once again.
Ignoring software vulnerabilities
You can ignore software vulnerabilities to be fixed. The reasons to ignore software vulnerabilities might be, for example, the following:
- You do not consider the software vulnerability to be critical to your organization.
- You understand that the software vulnerability fix can damage data related to the software that required the vulnerability fix.
- You are sure that the software vulnerability is not dangerous for your organization's network because you use other measures to protect your managed devices.
You can ignore a software vulnerability on all managed devices or only on selected managed devices.
To ignore a software vulnerability on all managed devices:
- In the Advanced → Application management folder in the console tree, select the Software vulnerabilities subfolder.
The workspace of the folder displays a list of vulnerabilities in applications detected on devices by the Network Agent installed on them.
- Select the vulnerability you want to ignore.
- Select Properties from the context menu of the vulnerability.
The properties window of the vulnerability opens.
- On the General section, select the Ignore vulnerability option.
- Click OK.
The software vulnerability properties window is closed.
The software vulnerability is ignored on all managed devices.
To ignore a software vulnerability on the selected managed device:
- Open the properties window of the selected managed device and select the Software vulnerabilities section.
- Select a software vulnerability.
- Ignore selected vulnerability.
The software vulnerability is ignored on the selected device.
The ignored software vulnerability will not be fixed after the completion of the Fix vulnerabilities task or Install required updates and fix vulnerabilities task. You can exclude ignored software vulnerabilities from the list of vulnerabilities by using a filter.
Selecting user fixes for vulnerabilities in third-party software
To use the Fix vulnerabilities task, you must manually specify the software updates to fix the vulnerabilities in third-party software listed in the task settings. The Fix vulnerabilities task uses recommended fixes for Microsoft software and user fixes for other third-party software. User fixes are software updates to fix vulnerabilities that the administrator manually specifies for installation.
To select user fixes for vulnerabilities in third-party software:
- In the Advanced → Application management folder in the console tree, select the Software vulnerabilities subfolder.
The workspace of the folder displays a list of vulnerabilities in applications detected on devices by the Network Agent installed on them.
- Select the vulnerability for which you want to specify a user fix.
- Select Properties from the context menu of the vulnerability.
The properties window of the vulnerability opens.
- In the User fixes and other fixes section, click the Add button.
The list of available installation packages is displayed. The list of displayed installation packages corresponds to the Remote installation → Installation packages list. If you have not created an installation package containing a user fix for selected vulnerability, you can create the package now by starting the New Package Wizard.
- Select an installation package (or packages) containing a user fix (or user fixes) for the vulnerability in third-party software.
- Click OK.
The installation packages containing user fixes for the software vulnerability are specified. When the Fix vulnerabilities task is started, the installation package will be installed, and the software vulnerability will be fixed.
Rules for update installation
When fixing vulnerabilities in applications, you must specify rules for update installation. These rules determine updates to install and vulnerabilities to fix.
The exact settings depend on whether you create a rule for updates of Microsoft applications, of third-party applications (applications made by software vendors other than Kaspersky and Microsoft), or of all applications. When creating a rule for Microsoft applications or third-party applications, you can select specific applications and application versions for which you want to install updates. When creating a rule for all applications, you can select specific updates that you want to install and vulnerabilities that you want to fix by means of installing updates.
To create a new rule for updates of all applications:
- On the Settings page of the Add Task Wizard, click the Add button.
The Rule Creation Wizard starts. Follow the steps of the Wizard.
- On the Rule type page, select Rule for all updates.
- On the General criteria page, use the drop-down lists to specify the following settings:
- On the Updates page, select the updates to be installed:
- On the Vulnerabilities page, select vulnerabilities that will be fixed by installing the selected updates:
- On the Name page, specify the name for the rule that you are creating. You can later change this name in the Settings section of the properties window of the created task.
After the Rule Creation Wizard completes its operation, the new rule is created and displayed in the Specify rules for installing updates field of the Add Task Wizard.
To create a new rule for updates of Microsoft applications:
- On the Settings page of the Add Task Wizard, click the Add button.
The Rule Creation Wizard starts. Follow the steps of the Wizard.
- On the Rule type page, select Rule for Windows Update.
- On the General criteria page, specify the following settings:
- On the Applications page, select the applications and application versions for which you want to install updates. By default, all applications are selected.
- On the Categories of updates page, select the categories of updates to be installed. These categories are the same as in Microsoft Update Catalog. By default, all categories are selected.
- On the Name page, specify the name for the rule that you are creating. You can later change this name in the Settings section of the properties window of the created task.
After the Rule Creation Wizard completes its operation, the new rule is created and displayed in the Specify rules for installing updates field of the Add Task Wizard.
To create a new rule for updates of third-party applications:
- On the Settings page of the Add Task Wizard, click the Add button.
The Rule Creation Wizard starts. Follow the steps of the Wizard.
- On the Rule type page, select Rule for third-party updates.
- On the General criteria page, specify the following settings:
- On the Applications page, select the applications and application versions for which you want to install updates. By default, all applications are selected.
- On the Name page, specify the name for the rule that you are creating. You can later change this name in the Settings section of the properties window of the created task.
After the Rule Creation Wizard completes its operation, the new rule is created and displayed in the Specify rules for installing updates field of the Add Task Wizard.