Contents
Flow security model
The Flow security model lets you associate resources with finite-state machines, receive and modify the states of finite-state machines, and check whether the state of the finite-state machine is within the defined set of states. For example, an entity can be associated with a finite-state machine to allow or prohibit this entity from using storage and/or the network depending on the state of the finite-state machine.
A PSL file containing a description of the Flow security model is located in the KasperskyOS SDK at the following path:
toolchain/include/nk/flow.psl
Flow security model object
To use the Flow security model, you need to create an object or objects of this model.
One Flow security model object lets you associate a set of resources with a set of finite-state machines that have the same configuration. A resource can be associated with only one finite-state machine of each Flow security model object.
A Flow security model object has the following parameters:
type State– type that determines the set of states of the finite-state machine (variant type that combines text literals).config– configuration of the finite-state machine:states– set of states of the finite-state machine (must match the set of states defined by theStatetype).initial– initial state of the finite-state machine.transitions– description of the permissible transitions between states of the finite-state machine.
All parameters of a Flow security model object are required.
Example:
policy object service_flow : Flow {
type State = "sleep" | "started" | "stopped" | "finished"
config = { states : ["sleep", "started", "stopped", "finished"]
, initial : "sleep"
, transitions : { "sleep" : ["started"]
, "started" : ["stopped", "finished"]
, "stopped" : ["started", "finished"]
}
}
}
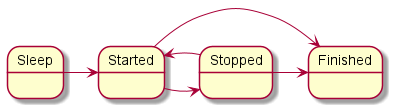
Diagram of finite-state machine states in the example
A Flow security model object can be covered by a security audit. You can also define the audit completion conditions specific to the Flow security model. To do so, use the following construct in the audit configuration description:
omit : [<"state 1">[,] ...] – the audit is not performed if the finite-state machine is in one of the listed states.
It is necessary to create multiple objects of the Flow security model in the following cases:
- You need to configure a security audit differently for different objects of the Flow security model (for example, you can apply different audit profiles or different audit configurations of the same profile for different objects).
- You need to distinguish between calls of methods provided by different objects of the Flow security model (audit data includes the name of the security model method and the name of the object that provides this method, so you can verify that the method of a specific object was called).
- You need to use finite-state machines with different configurations.
Flow security model init rule
init {sid : <Sid>}
It creates a finite-state machine and associates it with the resource that has the security ID sid. The created finite-state machine has the configuration defined in the settings of the Flow security model object being used.
It returns the "allowed" result if an association was created between the finite-state machine and the resource.
It returns the "denied" result in the following cases:
- The resource with the security ID
sidis already associated with a finite-state machine of the Flow security model object being used. - Security ID
sidis out of the permissible range.
Example:
/* An entity of the Server class will be allowed to start if
* when initiating the startup, an association is created
* between this entity and the finite-state machine. Otherwise the startup of a
Server-class entity will be denied. */
execute dst=Server {
service_flow.init {sid : dst_sid}
}
Flow security model fini rule
fini {sid : <Sid>}
It deletes the association between the finite-state machine and the resource that has the security ID sid. The finite-state machine that is no longer associated with the resource is destroyed.
It returns the "allowed" result if the association between the finite-state machine and the resource was deleted.
It returns the "denied" result in the following cases:
- The resource with the security ID
sidis not associated with a finite-state machine of the Flow security model object being used. - Security ID
sidis out of the permissible range.
Flow security model enter rule
enter {sid : <Sid>, state : <State>}
It switches the finite-state machine associated with the resource that has the security ID sid to the specified state.
It returns the "allowed" result if the finite-state machine was switched to the specified state.
It returns the "denied" result in the following cases:
- The transition to the specified
statefrom the current state is not permitted by the configuration of the finite-state machine. - The resource with the security ID
sidis not associated with a finite-state machine of the Flow security model object being used. - Security ID
sidis out of the permissible range.
Example:
/* Any client in the solution will be allowed to query
* a server of the Server class if the finite-state machine
* associated with this server will be switched
to the "started" state when initiating the query. Otherwise
* any client in the solution will be denied to query
* a server of the Server class. */
request dst=Server {
service_flow.enter {sid : dst_sid, state : "started"}
}
Flow security model allow rule
allow {sid : <Sid>, states : <Set<State>>}
It verifies that the state of the finite-state machine associated with the resource that has the security ID sid is in the set of defined states.
It returns the "allowed" result if the state of the finite-state machine is in the set of defined states.
It returns the "denied" result in the following cases:
- The state of the finite-state machine is not in the set of defined
states. - The resource with the security ID
sidis not associated with a finite-state machine of the Flow security model object being used. - Security ID
sidis out of the permissible range.
Example:
/* Any client in the solution is allowed to query a server
* of the Server class if the finite-state machine associated with this server
* is in the started or stopped state. Otherwise any client
* in the solution will be prohibited from querying a server of the Server class. */
request dst=Server {
service_flow.allow {sid : dst_sid, states : ["started", "stopped"]}
}
Flow security model query expression
query {sid : <Sid>}
It is intended to be used as an expression that verifies fulfillment of the conditions in the choice construct (for details on the choice construct, see "Binding methods of security models to security events"). It checks the state of the finite-state machine associated with the resource that has the security ID sid. Depending on the results of this check, various options for security event processing can be performed.
It runs incorrectly in the following cases:
- The resource with the security ID
sidis not associated with a finite-state machine of the Flow security model object being used. - Security ID
sidis out of the permissible range.
If the expression runs incorrectly, the Kaspersky Security Module returns the "denied" decision.
Example:
/* Any client in the solution is allowed to
* query a server of the ResourceDriver class
* if the finite-state machine associated with this
* server is in the started or
* stopped state. Otherwise any client in the solution
* is prohibited from querying a server in the class of
*ResourceDriver. */
request dst=ResourceDriver {
choice (service_flow.query {sid : dst_sid}) {
"started" : grant ()
"stopped" : grant ()
_ : deny ()
}
}