Contents
- Developing security policies
- Formal specifications of KasperskyOS-based solution components
- Describing a security policy for a KasperskyOS-based solution
- General information about a KasperskyOS-based solution security policy description
- PSL language syntax
- Describing the global parameters of a KasperskyOS-based solution security policy
- Including PSL files
- Including EDL files
- Creating security model objects
- Binding methods of security models to security events
- Describing security audit profiles
- Describing and performing tests for a KasperskyOS-based solution security policy
- PSL data types
- Examples of binding security model methods to security events
- Example descriptions of basic security policies for KasperskyOS-based solutions
- Example descriptions of security audit profiles
- Example descriptions of tests for KasperskyOS-based solution security policies
- KasperskyOS Security models
- Pred security model
- Bool security model
- Math security model
- Struct security model
- Base security model
- Regex security model
- HashSet security model
- StaticMap security model
- StaticMap security model object
- StaticMap security model init rule
- StaticMap security model fini rule
- StaticMap security model set rule
- StaticMap security model commit rule
- StaticMap security model rollback rule
- StaticMap security model get expression
- StaticMap security model get_uncommited expression
- Flow security model
- Mic security model
- Methods of KasperskyOS core endpoints
- Virtual memory endpoint
- I/O endpoint
- Threads endpoint
- Handles endpoint
- Processes endpoint
- Synchronization endpoint
- File system endpoints
- Time endpoint
- Hardware abstraction layer endpoint
- XHCI controller management endpoint
- Audit endpoint
- Profiling endpoint
- I/O memory management endpoint
- Connections endpoint
- Power management endpoint
- Notifications endpoint
- Hypervisor endpoint
- Trusted Execution Environment endpoints
- IPC interrupt endpoint
- CPU frequency management endpoint
Formal specifications of KasperskyOS-based solution components
Solution development includes the creation of formal specifications for its components that form a global picture for the Kaspersky Security Module. A formal specification of a KasperskyOS-based solution component (hereinafter referred to as the formal specification of the solution component) is comprised of a system of IDL, CDL and EDL descriptions (IDL and CDL descriptions are optional) for this component. These descriptions are used to automatically generate transport code of solution components, and source code of the security module and the initializing program. The formal specifications of solution components are also used as source data for the solution security policy description.
Just like solution components, the KasperskyOS kernel also has a formal specification (for details, see "Methods of KasperskyOS core endpoints").
Each solution component corresponds to an EDL description. In terms of a formal specification, a solution component is a container for components that provide endpoints. Multiple instances of one solution component may be used at the same time, which means that multiple processes can be started from the same executable file. Processes that correspond to the same EDL description are processes of the same class. An EDL description defines the name of a process class and the components for which a process of the defined class serves as a container.
Each component that is part of a solution component corresponds to a CDL description. This description defines the component name, provided endpoints, security interface, and embedded components. Components can simultaneously provide endpoints, support a security interface, and serve as containers for other components. Each component can provide multiple endpoints with one or more interfaces.
Each interface is defined in an IDL description. This description defines the interface name, signatures of interface methods, and data types for the parameters of interface methods. The data comprising signatures of interface methods and definitions of data types for parameters of interface methods is referred to as a package.
Processes that do not contain components may only act as clients. Processes that contain components can act as servers and/or clients. If components from a process provide endpoints, the process can act as a server and a client at the same time. If components from a process do not provide endpoints (and only support a security interface), the process can act only as a client.
The formal specification of a solution component does not define how this component will be implemented. In other words, the presence of components in a formal specification of a solution component does not mean that these components will be present in the architecture of this solution component.
Names of process classes, components, packages and interfaces
Process classes, components, packages and interfaces are identified by their names in IDL, CDL and EDL descriptions. The names of process classes, components and packages form three sets of names within a KasperskyOS-based solution, in which any name is unique within its own set. A set of package names includes a set of interface names.
The name of a process class, component, package or interface is a link to the IDL, CDL or EDL file in which this name is defined. This link is a path to the IDL, CDL or EDL file (without the extension and dot before it) relative to the directory that is included in the set of directories where the source code generators search for IDL, CDL and EDL files. (This set of directories is defined by parameters -I <path to files>.) A dot is used as a separator in a path description.
For example, the kl.core.NameServer process class name is a link to the EDL file named NameServer.edl, which is located in the KasperskyOS SDK at the following path:
sysroot-*-kos/include/kl/core
However, source code generators must be configured to search for IDL, CDL and EDL files in the following directory:
sysroot-*-kos/include
The name of an IDL, CDL or EDL file begins with an uppercase letter and must not contain any underscores _.
EDL description
EDL descriptions are put into separate *.edl files, which contain the following data:
- Process class name. The following declaration is used:
entity <process class name>
- [Optional] List of instances of components. The following declaration is used:
components {
<component instance name : component name>
...
}
Each component instance is indicated in a separate line. The component instance name must not contain any underscores
_. The list can contain multiple instances of one component. Each component instance in the list has a unique name.
The EDL language is case sensitive.
Single-line comments and multi-line comments can be used in an EDL description.
Supported endpoints and the security interface can be defined in an EDL description the same way they are defined in a CDL description. However, this practice is not recommended because EDL descriptions and CDL descriptions are usually created by different participants of the development process for KasperskyOS-based solutions. CDL descriptions are created by developers of system programs and application software. EDL descriptions are created by developers that integrate system programs and application software into a unified solution.
Examples of EDL files
Hello.edl
// Class of processes that do not contain components.
entity Hello
Signald.edl
/* Class of processes that contain
* one instance of one component. */
entity kl.Signald
components {
signals : kl.Signals
}
LIGHTCRAFT.edl
/* Class of processes that contain
* two instances of different components. */
entity kl.drivers.LIGHTCRAFT
components {
KUSB : kl.drivers.KUSB
KIDF : kl.drivers.KIDF
}
CDL description
CDL descriptions are put into separate *.cdl files, which contain the following data:
- The name of the component. The following declaration is used:
component <component name>
- [Optional] Security interface. The following declaration is used:
security <interface name>
- [Optional] List of endpoints. The following declaration is used:
endpoints {
<endpoint name : interface name>
...
}
Each endpoint is indicated in a separate line. The endpoint name must not contain any underscores
_. The list can contain multiple endpoints with the same interface. Each endpoint in the list has a unique name. - [Optional] List of instances of embedded components. The following declaration is used:
components {
<component instance name : component name>
...
}
Each component instance is indicated in a separate line. The component instance name must not contain any underscores
_. The list can contain multiple instances of one component. Each component instance in the list has a unique name.
The CDL language is case sensitive.
Single-line comments and multi-line comments can be used in a CDL description.
At least one optional declaration is used in a CDL description. If a CDL description does not use at least one optional declaration, this description will correspond to an "empty" component that does not provide endpoints, does not contain embedded components, and does not support a security interface.
Examples of CDL files
KscProductEventsProvider.cdl
// Component provides one endpoint.
component kl.KscProductEventsProvider
endpoints {
eventProvider : kl.IKscProductEventsProvider
}
KscConnectorComponent.cdl
// Component provides multiple endpoints.
component kl.KscConnectorComponent
endpoints {
KscConnCommandSender : kl.IKscConnCommandSender
KscConnController : kl.IKscConnController
KscConnSettingsHolder : kl.IKscConnSettingsHolder
KscDataProvider : kl.IKscDataProvider
ProductDataHolder : kl.IProductDataHolder
KscDataNotifier : kl.IKscDataNotifier
KscConnectorStateNotifier : kl.IKscConnectorStateNotifier
}
FsVerifier.cdl
/* Component does not provide endpoints, supports
* a security interface, and contains one instance
* of another component. */
component FsVerifier
security Approve
components {
verifyComp : Verify
}
IDL description
IDL descriptions are put into separate *.idl files, which contain the following data:
- Package name. The following declaration is used:
package <package name>
- [Optional] Packages from which the data types for interface method parameters are imported. The following declaration is used:
import <package name>
- [Optional] Definitions of data types for parameters of interface methods.
- [Optional] Signatures of interface methods. The following declaration is used:
interface {
<interface method name([parameters])>;
...
}
Each method signature is indicated in a separate line. The method name must not contain any underscores
_. Each method in the list has a unique name. The parameters of methods are divided into input parameters (in), output parameters (out), and parameters for transmitting error information (error).Input parameters and output parameters are transmitted in IPC requests and IPC responses, respectively. Error parameters are transmitted in IPC responses if the server cannot correctly handle the corresponding IPC requests.
The server can inform a client about IPC request processing errors via error parameters as well as through output parameters of interface methods. If the server sets the error flag in an IPC response when an error occurs, this IPC response will contain the error parameters without any output parameters. Otherwise this IPC response will contain output parameters just like when requests are correctly processed. (The error flag is set in IPC responses by using the
nk_err_reset()macro defined in thenk/types.hheader file from the KasperskyOS SDK.)An IPC response sent with the error flag set and an IPC response with the error flag not set are considered to be different types of events for the Kaspersky Security Module. When describing a solution security policy, this difference lets you conveniently distinguish between the processing of events associated with the correct execution of IPC requests and the processing of events associated with incorrect execution of IPC requests. If the server does not set the error flag in IPC responses, the security module must check the values of output parameters indicating errors to properly process events related to the incorrect execution of IPC requests. (A client can check the state of the error flag in an IPC response even if the corresponding interface method does not contain error parameters. To do so, the client uses the
nk_msg_check_err()macro defined in thenk/types.hheader file from the KasperskyOS SDK.)Signatures of interface methods cannot be imported from other IDL files.
The IDL language is case sensitive.
Single-line comments and multi-line comments can be used in an IDL description.
At least one optional declaration is used in a IDL description. If an IDL description does not use at least one optional declaration, this description will correspond to an "empty" package that does not assign any interface methods or data types (including from other IDL descriptions).
Some IDL files from the KasperskyOS SDK do not describe interface methods, but instead only contain definitions of data types. These IDL files are used only as exporters of data types.
If a package contains a description of interface methods, the interface name matches the package name.
Examples of IDL files
Env.idl
package kl.Env
// Definitions of data types for interface method parameters
typedef string<128> Name;
typedef string<256> Arg;
typedef sequence<Arg,256> Args;
// Interface includes one method.
interface {
Read(in Name name, out Args args, out Args envs);
}
Kpm.idl
package kl.Kpm
// Import data types for parameters of interface methods
import kl.core.Types
// Definition of data type for parameters of interface methods
typedef string<64> String;
/* Interface includes multiple methods.
* Some methods do not have any parameters. */
interface {
Shutdown();
Reboot();
PowerButtonPressedWait();
TerminationSignalWait(in UInt32 entityId, in String entityName);
EntityTerminated(in UInt32 entityId);
Terminate(in UInt32 callingEntityId);
}
MessageBusSubs.idl
package kl.MessageBusSubs
// Import data types for interface method parameters
import kl.MessageBusTypes
/* Interface includes a method that has
* input and output parameters, and
* an error parameter.*/
interface {
Wait(in ClientId id,
out Message topic,
out BundleId dataId,
error ResultCode result);
}
WaylandTypes.idl
// Package contains only definitions of data types.
package kl.WaylandTypes
typedef UInt32 ClientId;
typedef bytes<8192> Buffer;
typedef string<4096> ConnectionId;
typedef SInt32 SsizeT;
typedef UInt32 SizeT;
typedef SInt32 ShmFd;
typedef SInt32 ShmId;
typedef bytes<16384000> ShmBuffer;
IDL data types
Primitive types
IDL supports the following primitive types:
SInt8,SInt16,SInt32,SInt64(signed integer)UInt8,UInt16,UInt32,UInt64(unsigned integer)Handle(value whose binary representation consists of multiple fields, including a handle field and a handle permissions mask field)bytes<<size in bytes>>(byte buffer)string<<size in bytes>>(string buffer)
A byte buffer is a memory area with a size that does not exceed the defined number of bytes. A string buffer is a byte buffer whose last byte is a terminating zero. The maximum size of a string buffer is a unit larger than the defined size due to the additional byte with the terminating zero. To transfer a byte buffer or string buffer via IPC, the amount of memory that is actually occupied by this buffer will be used.
For numeric types, you can declare named constants by using the reserved word const:
const UInt32 DeviceNameMax = 64;
const UInt32 HandleTypeUserLast = 0x0001FFFF;
Constants are used to avoid problems associated with "magic numbers". For example, if an IDL description defines constants for return codes of an interface method, you can interpret these codes without additional information when describing a policy.
In addition to primitive types, the IDL language supports composite types, such as unions, structures, arrays and sequences. In a definition of composite types, constants of primitive types may be applied as parameters (for example, to assign an array size).
The bytes<<size in bytes>> and string<<size in bytes>> constructs are used in definitions of composite types, signatures of interface methods, and when creating type aliases because they define anonymous types (types without a name).
Unions
A union lets you store different types of data in one memory area. In an IPC message, a union is provided with an additional tag field that lets you define which specific member of the union is used.
The following construct is used to define a union:
union <type name> {
<member type> <member name>;
...
}
Example of a union definition:
union ExitInfo {
UInt32 code;
ExceptionInfo exc;
}
Structures
The following construct is used to define a structure:
struct <type name> {
<field type> <field name>;
...
}
Example of a structure definition:
struct SessionEvqParams {
UInt32 count;
UInt32 align;
UInt32 size;
}
Arrays
The following construct is used to define an array:
array<<type of elements, number of elements>>
This construct is used in definitions of other composite types, signatures of interface methods, and when creating type aliases because it defines an anonymous type.
Sequences
A sequence is a variable-sized array. When defining a sequence, its maximum number of elements is specified. However, you can actually transmit less than this number (via IPC). In this case, only an amount of memory necessary for the transmitted elements will be used.
The following construct is used to define a sequence:
sequence<<type of elements, number of elements>>
This construct is used in definitions of other composite types, signatures of interface methods, and when creating type aliases because it defines an anonymous type.
Types based on composite types
Composite types can be used to define other composite types. The definition of an array or sequence can also be included in the definition of another type:
struct BazInfo {
array<UInt8, 100> a;
sequence<sequence<UInt32, 100>, 200> b;
string<100> c;
bytes<4096> d;
UInt64 e;
}
The definition of a union or structure cannot be included in the definition of another type. However, a previously described definition of a union or structure can be included in a type definition. This is done by indicating the names of the included types in the type definition:
union foo {
UInt32 value1;
UInt8 value2;
}
struct bar {
UInt32 a;
UInt8 b;
}
struct BazInfo {
foo x;
bar y;
}
Creating aliases of types
Type aliases make it more convenient to work with types. For example, type aliases can be used to assign mnemonic names to types that have abstract names. Assigned aliases for anonymous types also let you receive named types.
The following construct is used to create a type alias:
typedef <type name/anonymous type definition> <type alias>
Example of creating mnemonic aliases:
typedef UInt64 ApplicationId;
typedef Handle PortHandle;
Example of creating an alias for an array definition:
typedef array<UInt8, 4> IP4;
Example of creating an alias for a sequence definition:
const UInt32 MaxDevices = 8;
struct Device {
string<32> DeviceName;
UInt8 DeviceID;
}
typedef sequence<Device, MaxDevices> Devices;
Example of creating an alias for a union definition:
union foo {
UInt32 value1;
UInt8 value2;
}
typedef foo bar;
Defining anonymous types in signatures of interface methods
Anonymous types can be defined in signatures of interface methods.
Example of defining a sequence in an interface method signature:
Poll(in Generation generation,
in UInt32 timeout,
out Generation currentGeneration,
out sequence<Report, DeviceMax> report,
out UInt32 count,
out UInt32 rc);
Describing a security policy for a KasperskyOS-based solution
A KasperskyOS-based solution security policy description (hereinafter also referred to as a solution security policy description or policy description) provides a set of interrelated text files with the psl extension that contain declarations in the PSL language. Some files reference other files through an inclusion declaration, which results in a hierarchy of files with one top-level file. The top-level file is specific to the solution. Files of lower and intermediate levels contain parts of the solution security policy description that may be specific to the solution or may be re-used in other solutions.
Some of the files of the lower and intermediate levels are provided in the KasperskyOS SDK. These files contain definitions of the basic data types and formal descriptions of KasperskyOS security models. KasperskyOS security models (hereinafter referred to as security models) serve as the framework for implementing security policies for KasperskyOS-based solutions. Files containing formal descriptions of security models reference a file containing definitions of the basic data types that are used in the descriptions of models.
The other files of lower and intermediate levels are created by the policy description developer if any parts of the policy description need to be re-used in other solutions. A policy description developer can also put parts of the policy description into separate files for convenient editing.
The top-level file references files containing definitions of basic data types and descriptions of security models that are applied in the part of the solution security policy that is described in this file. The top-level file also references all files of the lower and intermediate levels that were created by the policy description developer.
The top-level file is normally named security.psl, but it can have any other name in the *.psl format.
General information about a KasperskyOS-based solution security policy description
In simplified terms, a KasperskyOS-based solution security policy description consists of bindings that associate descriptions of security events with calls of methods provided by security model objects. A security model object is an instance of a class whose definition is a formal description of a security model (in a PSL file). Formal descriptions of security models contain signatures of methods of security models that determine the permissibility of interactions between different processes and between processes and the KasperskyOS kernel. These methods are divided into two types:
- Security model rules are methods of security models that return a "granted" or "denied" result. Security model rules can change security contexts (for information about a security context, see "Resource Access Control").
- Security model expressions are methods of security models that return values that can be used as input data for other methods of security models.
A security model object provides methods that are specific to one security model and stores the parameters used by these methods (for example, the initial state of a finite-state machine or the size of a container for specific data). The same object can be used to work with multiple resources. (In other words, you do not need to create a separate object for each resource.) However, this object will independently use the security contexts of these resources. Likewise, multiple objects of one or more different security models can be used to work with the same resource. In this case, different objects will use the security context of the same resource without any reciprocal influence.
Security events serve as signals indicating the initiation of interaction between different processes and between processes and the KasperskyOS kernel. Security events include the following events:
- Clients send IPC requests.
- Servers or the kernel send IPC responses.
- The kernel or processes initialize the startup of processes.
- The kernel starts.
- Processes query the Kaspersky Security Module via the security interface.
Security events are processed by the security module.
Security models
The KasperskyOS SDK provides PSL files that describe the following security models:
- Base – methods that implement basic logic.
- Pred – methods that implement comparison operations.
- Bool – methods that implement logical operations.
- Math – methods that implement integer arithmetic operations.
- Struct – methods that provide access to structural data elements (for example, access to parameters of interface methods transmitted in IPC messages).
- Regex – methods for text data validation based on regular expressions.
- HashSet – methods for working with one-dimensional tables associated with resources.
- StaticMap – methods for working with two-dimensional "key–value" tables associated with resources.
- Flow – methods for working with finite-state machines associated with resources.
- Mic – methods for implementing Mandatory Integrity Control (MIC).
Security event handling by the Kaspersky Security Module
The Kaspersky Security Module calls all methods (rules and expressions) of security models related to an occurring security event. If all rules returned the "granted" result, the security module returns the "granted" decision. If even one rule returned the "denied" result, the security module returns the "denied" decision.
If even one method related to an occurring security event cannot be correctly performed, the security module returns the "denied" decision.
If no rule is related to an occurring security event, the security module returns the "denied" decision. In other words, all interactions between solution components and between those components and the KasperskyOS kernel are denied by default (Default Deny principle) unless those interactions are explicitly allowed by the solution security policy.
Security audit
A security audit (hereinafter also referred to as an audit) is the following sequence of actions. The Kaspersky Security Module notifies the KasperskyOS kernel about decisions made by this module. Then the kernel forwards this data to the system program Klog, which decodes this data and forwards it to the system program KlogStorage (data is transmitted via IPC). The latter prints the received data via standard output or saves it to a file.
Security audit data (hereinafter referred to as audit data) refers to information about decisions made by the Kaspersky Security Module, which includes the actual decisions ("granted" or "denied"), descriptions of security events, results from calling methods of security models, and data on incorrect IPC messages. Data on calls of security model expressions is included in the audit data just like data on calls of security model rules.
Page topPSL language syntax
Basic rules
- Declarations can be listed in any sequence in a file.
- One declaration can be written to one or multiple lines. The second and subsequent lines of the declaration must be written with indentations relative to the first line. The closing brace that completes the declaration can be written on the first line.
- A multi-line declaration utilizes different-sized indentations to reflect the nesting of constructs comprising this declaration. The second and subsequent lines of a multi-line construct enclosed in braces must be written with an indentation relative to the first line of this construct. The closing brace of a multi-line construct can be written with an indentation or on the first line of the construct.
- The PSL language is case sensitive.
- Single-line comments and multi-line comments are supported:
/* This is a comment
* And this, too */
// Another comment
Types of declarations
The PSL language has declarations for the following purposes:
- Describing the global parameters of a solution security policy
- Including PSL files
- Including EDL files
- Creating security model objects
- Binding methods of security models to security events
- Describing security audit profiles
- Describing solution security policy tests
Describing the global parameters of a KasperskyOS-based solution security policy
Global parameters include the following parameters of a solution security policy:
- Execute interface used by the KasperskyOS kernel when querying the Kaspersky Security Module to notify it about kernel startup or about initiating the startup of a process by the kernel or by other processes. To assign this interface, use the following declaration:
execute: kl.core.Execute
KasperskyOS currently supports only one execute interface (
Execute) defined in the file namedkl/core/Execute.idl. (This interface consists of onemainmethod, which has no parameters and does not perform any actions. Themainmethod is reserved for potential future use.) - [Optional] Global security audit profile and initial security audit runtime-level. To define these parameters, use the following declaration:
audit default = <security audit profile name> <security audit runtime-level>
Example:
audit default = global 0
The default global profile is the
emptysecurity audit profile described in the file namedtoolchain/include/nk/base.pslfrom the KasperskyOS SDK, and the default security audit runtime-level is 0.
Including PSL files
To include a PSL file, use the following declaration:
use <link to PSL file._>
The link to the PSL file is the file path (without the extension and dot before it) relative to the directory that is included in the set of directories where the nk-psl-gen-c compiler searches for PSL, IDL, CDL, and EDL files. (This set of directories is defined by the parameters -I <path to files> when starting the makekss script or the nk-psl-gen-c compiler.) A dot is used as a separator in a path description. A declaration is ended by the ._ character sequence.
Example:
use policy_parts.flow_part._
This declaration includes the flow_part.psl file, which is located in the policy_parts directory. The policy_parts directory must reside in one of the directories where the nk-psl-gen-c compiler searches for PSL, IDL, CDL, and EDL files. For example, the policy_parts directory may reside in the same directory as the PSL file containing this declaration.
Including a PSL file containing a formal description of a security model
To use the methods of a required security model, you need to include a PSL file containing a formal description of this model. PSL files containing formal descriptions of security models are located in the KasperskyOS SDK at the following path:
toolchain/include/nk
Example:
/* Include the base.psl file containing a formal description of the
* Base security model */
use nk.base._
/* Include the flow.psl file containing a formal description of the
* Flow security model */
use nk.flow._
/* The nk-psl-gen-c compiler must be configured to search for
* PSL, IDL, CDL, and EDL files in the toolchain/include directory. */
Including EDL files
To include an EDL file for the KasperskyOS kernel, use the following declaration:
use EDL kl.core.Core
To include an EDL file for a program (such as a driver or application), use the following declaration:
use EDL <link to EDL file>
The link to the EDL file is the EDL file path (without the extension and dot before it) relative to the directory that is included in the set of directories where the nk-psl-gen-c compiler searches for PSL, IDL, CDL, and EDL files. (This set of directories is defined by the parameters -I <path to files> when starting the makekss script or the nk-psl-gen-c compiler.) A dot is used as a separator in a path description.
Example:
/* Include the UART.edl file, which is located
* in the KasperskyOS SDK at the path sysroot-*-kos/include/kl/drivers. */
use EDL kl.drivers.UART
/* The nk-psl-gen-c compiler must be configured to search for
* PSL, IDL, CDL, and EDL files in the sysroot-*-kos/include directory. */
The nk-psl-gen-c compiler finds IDL and CDL files via EDL files because EDL files contain links to the corresponding CDL files, and the CDL files contain links to the corresponding CDL and IDL files.
Creating security model objects
To call the methods of a required security model, create an object for this security model.
To create a security model object, use the following declaration:
policy object <security model object name : security model name> {
[security model object parameters]
}
The parameters of a security model object are specific to the security model. A description of parameters and examples of creating objects of various security models are provided in the "KasperskyOS security models" section.
Page topBinding methods of security models to security events
To create an attachment between methods of security models and a security event, use the following declaration:
<security event type> [security event selectors] {
[security audit profile]
<called security model rules>
}
Security event type
The following specifiers are used to define the security event type:
request– sending IPC requests.response– sending IPC responses.error– sending IPC responses containing information about errors.security– processes querying the Kaspersky Security Module via the security interface.execute– initializing the startups of processes or the startup of the KasperskyOS kernel.
When processes interact with the security module, they use a mechanism that is different from IPC. However, when describing a policy, queries sent by processes to the security module can be viewed as the transfer of IPC messages because processes actually transmit messages to the security module (the recipient is not indicated in these messages).
The IPC mechanism is not used to start processes. However, when the startup of a process is initiated, the kernel queries the security module and provides information about the initiator of the startup and the started process. For this reason, the policy description developer can consider the startup of a process to be analogous to sending an IPC message from the startup initiator to the started process. When the kernel is started, this is analogous to the kernel sending an IPC message to itself.
Security event selectors
Security event selectors let you clarify the description of the defined type of security event. The following selectors are used:
src=<kernel/process class name> – processes of the defined class or the KasperskyOS kernel are the sources of IPC messages.dst=<kernel/process class name> – processes of the defined class or the kernel are the recipients of IPC messages.interface=<interface name> – describes the following security events:- Clients attempt to use the endpoints of servers or the kernel with the defined interface.
- Processes query the Kaspersky Security Module via the defined security interface.
- The kernel or servers send clients the results from using the endpoints with the defined interface.
component=<component name> – describes the following security events:- Clients attempt to use the core or server endpoints provided by the defined component.
- The kernel or servers send clients the results from using the endpoints provided by the defined component.
endpoint=<qualified endpoint name> – describes the following security events:- Clients attempt to use the defined core or server endpoints.
- The kernel or servers send clients the results from using the defined endpoint.
method=<method name> – describes the following security events:- Clients attempt to query servers or the kernel by calling the defined method of the endpoint.
- Processes query the security module by calling the defined method of the security interface.
- The kernel or servers send clients the results from calling the defined method of the endpoint.
- The kernel notifies the security module about its startup by calling the defined method of the execute interface.
- The kernel initiates the startup of processes by calling the defined method of the execute interface.
- Processes initiate the startup of other processes, which results in the kernel calling the defined method of the execute interface.
Process classes, components, instances of components, interfaces, endpoints, and methods must be named the same as they are in the IDL, CDL, and EDL descriptions. The kernel must be named kl.core.Core.
The qualified name of the endpoint has the format <path to endpoint.endpoint name>. The path to the endpoint is a sequence of component instance names separated by dots. Among these component instances, each subsequent component instance is embedded into the previous one, and the last one provides the endpoint with the defined name.
For security events, specify the qualified name of the security interface method if you need to use the security interface defined in a CDL description. (If you need to use a security interface defined in an EDL description, it is not necessary to specify the qualified name of the method.) The qualified name of a security interface method is a construct in the format <path to security interface.method name>. The path to the security interface is a sequence of component instance names separated by dots. Among these component instances, each subsequent component instance is embedded into the previous one, and the last one supports the security interface that includes the method with the defined name.
If selectors are not specified, the participants of a security event may be any process and the kernel (except security events in which the kernel cannot participate).
You can use combinations of selectors. Selectors can be separated by commas.
There are restrictions on the use of selectors. The interface, component, and endpoint selectors cannot be used for security events of the execute type. The dst, component, and endpoint selectors cannot be used for security events of the security type.
There are also restrictions on combinations of selectors. For security events of the request, response and error types, the method selector can only be used together with one of the endpoint, interface, or component selectors or a combination of them. (The method, endpoint, interface and component selectors must be coordinated. In other words, the method, endpoint, interface, and component must be interconnected.) For security events of the request type, the endpoint selector can be used only together with the dst selector. For security events of the response and error types, the endpoint selector can be used only together with the src selector.
The type and selectors of a security event make up the security event description. It is recommended to describe security events with maximum precision to allow only the required interactions between different processes and between processes and the kernel. If IPC messages of the same type are always verified when processing the defined event, the description of this event is maximally precise.
To ensure that IPC messages of the same type correspond to a security event description, one of the following conditions must be fulfilled for this description:
- For events of the
request,responseanderrortype, the "interface method-endpoint-server class or kernel" chain is unequivocally defined. For example, the security event descriptionrequest dst=Server endpoint=net.Net method=Sendcorresponds to IPC messages of the same type, and the security event descriptionrequest dst=Servercorresponds to any IPC message sent to theServer. - For
securityevents, the security interface method is specified. - The execute-interface method is indicated for
executeevents.There is currently support for only one fictitious method of the
mainexecute-interface. This method is used by default, so it does not have to be defined through themethodselector. This way, any description of anexecutesecurity event corresponds to IPC messages of the same type.
Security audit profile
A security audit profile is defined by the construct audit <security audit profile name>. If a security audit profile is not defined, the global security audit profile is used.
Called security model rules
Called security model rules are defined by a list from the following type of constructs:
[security model object name.]<security model rule name> <parameter>
Input data for security model rules may be values returned by security model expressions. The following construct is used to call a security model expression:
[security model object name.]<security model expression name> <parameter>
Parameters of interface methods can also be used as input data for methods of security models (rules and expressions). (For details about obtaining access to parameters of interface methods, see "Struct security model"). In addition, input data for methods of security models can also be the SID values of processes and the KasperskyOS kernel that are defined by the src_sid and dst_sid reserved words. The first reserved word refers to the SID of the process (or kernel) that is the source of the IPC message. The second reserved word refers to the SID of the process (or kernel) that is the recipient of the IPC message (dst_sid cannot be used for queries to the Kaspersky Security Module).
For calls of some rules and expressions of security models, you can choose not to indicate the security model object name, and you can use operators. For details about the methods of security models, see KasperskyOS Security models.
Embedded constructs for binding methods of security models to security events
In one declaration, you can bind methods of security models to different security events of the same type. To do so, use the match sections that consist of the following types of constructs:
match <security event selectors> {
[security audit profile]
<called security model rules>
}
Match sections can be embedded into another match section. A match section simultaneously uses its own security event selectors and the security event selectors at the level of the declaration and all match sections in which this match section is "wrapped". By default, a match section applies the security audit profile of its own container (match section of the preceding level or the declaration level), but you can define a separate security audit profile for the match section.
In one declaration, you can define different variants for processing a security event depending on the conditions in which this event occurred (for example, depending on the state of the finite-state machine associated with the resource). To do so, use the conditional sections that are elements of the following construct:
choice <call of the security model expression that verifies fulfillment of conditions> {
"<condition 1>" : [{] // Conditional section 1
[security audit profile]
<called security model rules>
[}]
"<condition 2>" : ... // Conditional section 2
...
_ : ... // Conditional section, if no condition is fulfilled.
}
The choice construct can be used within a match section. A conditional section uses the security event selectors and security audit profile of its own container, but you can define a separate security audit profile for a conditional section.
If multiple conditions described in the choice construct are simultaneously fulfilled when a security event is processed, only the one conditional section corresponding to the first matching condition on the list is triggered.
You can verify the fulfillment of conditions in the choice construct only by using the expressions that are specially intended for this purpose. Some security models contain these expressions (for more details, see KasperskyOS Security models).
Examples of binding security model methods to security events
See "Examples of binding security model methods to security events", "Example descriptions of basic security policies for KasperskyOS-based solutions", and "KasperskyOS security models".
Page topDescribing security audit profiles
To perform a security audit, you need to associate security model objects with security audit profile(s). A security audit profile (hereinafter also referred to as an audit profile) combines security audit configurations (hereinafter also referred to as audit configurations), each of which defines the security model objects covered by the audit, and specifies the conditions for conducting the audit. You can define a global audit profile (for more details, see "Describing the global parameters of a KasperskyOS-based solution security policy") and/or assign audit profile(s) at the level of binding security model methods to security events, and/or assign audit profile(s) at the level of match sections or choice sections (for more details, see "Binding methods of security models to security events").
Regardless of whether or not audit profiles are being used, audit data contains information about "denied" decisions that were made by the Kaspersky Security Module when IPC messages were invalid and when handling security events that are not associated with any security model rule.
To describe a security audit profile, use the following declaration:
audit profile <security audit profile name> =
{ <security audit runtime-level> :
// Description of the security audit configuration
{ <security model object name> :
{ kss: <security audit conditions linked to the results
from calls of security model rules>
[, security audit conditions specific to the security model]
}
[,]...
...
}
[,]...
...
}
Security audit runtime-level
The security audit runtime-level (hereinafter referred to as the audit runtime-level) is a global parameter of a solution security policy and consists of an unsigned integer that defines the active security audit configuration. (The word "runtime-level" here refers to the configuration variant and does not necessarily involve a hierarchy.) The audit runtime-level can be changed during operation of the Kaspersky Security Module. This is done by using a specialized method of the Base security model that is called when processes query the security module via the security interface (for more details, see "Base security model"). The initial audit runtime-level is assigned together with the global audit profile (for more details, see "Describing the global parameters of a KasperskyOS-based solution security policy"). An empty audit profile can be explicitly assigned as the global audit profile.
You can define multiple audit configurations in an audit profile. In different configurations, different security model objects can be covered by the audit and different conditions for conducting the audit can be applied. Audit configurations in a profile correspond to different audit runtime-levels. If a profile does not have an audit configuration corresponding to the current audit runtime-level, the security module will activate the configuration that corresponds to the next-lowest audit runtime-level. If a profile does not have an audit configuration for an audit runtime-level equal to or less than the current level, the security module will not use this profile (in other words, an audit will not be performed for this profile).
Audit runtime-levels can be used to regulate the level of detail of an audit, for example. The higher the audit runtime-level, the higher the level of detail. The higher the level of detail, the more security model objects are covered by the audit and/or the less restrictions are applied in the audit conditions.
Another example of applying audit runtime-levels is the capability to shift the audit from one subsystem to another subsystem (for example, shift an audit related to drivers to an audit related to applications, or shift an audit related to the network subsystem to an audit related to the graphic subsystem).
Name of the security model object
The security model object name is indicated so that the methods provided by this object can be covered by the audit. These methods will be covered by the audit whenever they are called, provided that the conditions for conducting the audit are observed.
Information about the decisions of the Kaspersky Security Module contained in audit data includes the overall decision of the security module as well as the results from calling individual methods of security modules covered by the audit. To ensure that information about a security module decision is included in audit data, at least one method called during security event handling must be covered by the audit.
The names of security model objects and the names of methods provided by these objects are included in the audit data.
Security audit conditions
Security audit conditions are defined separately for each object of a security model.
To define the audit conditions related to the results from calling security model rules, use the following constructs:
["granted"]– the audit is performed if the rules return the "granted" result.["denied"]– the audit is performed if the rules return the "denied" result.["granted", "denied"]– the audit is performed if the rules return the "granted" or "denied" result.[]– the audit is not performed, regardless of the result returned by the rules.
Audit conditions related to results from calling rules are not applied to expressions. These conditions must be defined (by any allowed construct) even if the security model contains only expressions because PSL language syntax requires it.
Audit conditions specific to security models are defined by constructs specific to these models (for more details, see KasperskyOS Security models). These conditions apply to rules and expressions. For example, one of these conditions can be the state of a finite-state machine.
Security audit profile for a security audit route
A security audit route includes the kernel and the Klog and KlogStorage processes, which are connected by IPC channels based on the "kernel – Klog – KlogStorage" scheme. Security model methods that are associated with transmission of audit data via this route must not be covered by the audit. Otherwise, this will lead to an avalanche of audit data because any data transmission will give rise to new data.
To "suppress" an audit that was defined by a profile with a wider scope (for example, by a global profile or a profile at the level of binding security model methods to a security event), you need to assign an empty audit profile at the level of binding security model methods to security events or at the level of the match section or choice section.
Example descriptions of audit profiles
See Example descriptions of security audit profiles.
Page topDescribing and performing tests for a KasperskyOS-based solution security policy
A solution security policy is tested to verify whether or not the policy actually allows what should be allowed and denies what should be denied.
To describe a set of tests for a solution security policy, you need to use the following declaration:
assert "<name of test set>" {
// Constructs in PAL (Policy Assertion Language)
[setup {<initial part of tests>}]
sequence "<test name>" {<main part of test>}
...
[finally {<final part of tests>}]
}
You can describe multiple sets of tests by using several of these declarations.
The test set description can optionally include the initial part of the tests and/or the final part of the tests. The execution of each test from the set begins with whatever is described in the initial part of the test and ends with whatever is described in the final part of the test. This lets you describe the repeated initial and/or final parts of tests in each test.
After completing each test, all modifications in the Kaspersky Security Module related to the execution of this test are rolled back.
Each test includes one or more test cases.
Test cases
A test case associates a security event description and values of interface method parameters with an expected decision of the Kaspersky Security Module. If the actual security module decision matches the expected decision, the test case passes. Otherwise it fails.
When a test is run, the test cases are executed in the same sequence in which they are described. In other words, you can test how the security module handles a sequence of security events.
If all test cases within a test pass, the test passes. If even one test case fails to pass, the test fails. A test is terminated on the first failing test case.
A test case description is created in the PAL language and is comprised of a sequence of values:
[expected decision of security module] ["test example name"] <security event type> <security event selectors> [{interface method parameter values}]
The expected decision of the security module can be indicated as grant ("granted"), deny ("denied") or any ("any decision"). If the expected security module decision is not specified, the "granted" decision is expected. If the any value is specified, the security module decision does not have any influence on whether or not the test case passes. In this case, the test case may fail due to errors that occur when the security module processes an IPC message (for example, when the IPC message has an invalid structure).
For information about the types and selectors of security events, and about the limitations when using selectors, see Binding methods of security models to security events. Selectors must ensure that the security event description corresponds to IPC messages of the same type. (When security model methods are bound to security events, selectors may fail to ensure this.)
In security event descriptions, you need to specify the SID instead of the process class name (and the KasperskyOS kernel). However, this requirement does not apply to execute events for which the SID of the started process (or kernel) is unknown. To save the SID of the process or kernel to a variable, you need to use the <- operator in the test case description in the following format:
<variable name> <- execute dst=<kernel/process class name> ...
The SID value will be assigned to the variable even if startup of the process of the defined class (or kernel) is denied by the tested policy but the "denied" decision is expected.
The PAL language supports abbreviated forms of security event descriptions:
security: <Process SID>!<qualified name of security interface method> corresponds tosecurity src=<process SID>method=<qualified name of security interface method>.request: <client SID>~><kernel/server SID>:<qualified name of endpoint.method name> corresponds torequest src=<client SID>dst=<kernel/server SID>endpoint=<qualified name of endpoint>method=<method name>.response: <client SID><~<kernel/server SID>:<qualified name of endpoint.method name> corresponds toresponse src=<kernel/server SID>dst=<client SID>endpoint=<qualified name of endpoint>method=<method name>.
If an interface method has parameters, their values are defined by comma-separated constructs:
<parameter name> : <value>
The names and types of parameters must comply with the IDL description. The sequence order of parameters is not important.
Example definition of parameter values
{ param1 : 23, param2 : "bar", param3: { collection : [5,7,12], filehandle : 15 }, param4 : { name : ["foo", "baz" } }
In this example, the number is passed through the param1 parameter. The string buffer is passed through the param2 parameter. A structure consisting of two fields is passed through the param3 parameter. The collection field contains an array or sequence of three numeric elements. The filehandle field contains the SID. A union or structure containing one field is passed through the param4 parameter. The name field contains an array or sequence of two string buffers.
Currently, only an SID can be indicated as the value of a Handle parameter, and there is no capability to indicate the SID together with a handle permissions mask. For this reason, it is not possible to properly test a solution security policy when the permissions masks of handles influence the security module decisions.
Example descriptions of policy tests
See "Example descriptions of tests for KasperskyOS-based solution security policies".
Test procedure
Descriptions of tests are placed into PSL files, including those that contain a solution security policy description (for example, into the security.psl file).
To run tests, you need to use the --tests run parameter when starting the nk-psl-gen-c compiler:
$ nk-psl-gen-c --tests run <other parameters> security.psl
You also need to indicate the following data for the nk-psl-gen-c compiler:
- Directories that contain auxiliary files from the KasperskyOS SDK (
common,sysroot-*-kos/include,toolchain/include). This set of directories is defined by the parameters-I, -include-dir<path to files>. - Directories that contain PSL, IDL, CDL, and EDL files related to the solution. This set of directories is defined by the parameters
-I, --include-dir<path to files>. - Path to the file that will save the source code of the Kaspersky Security Module and tests. This path is defined by the parameter
-o, --output<path to file>.
The nk-psl-gen-c compiler generates the source code of the security module and tests in the C language, saves this code to a file, and then runs the compilation of this code using gcc and executes the obtained test program. The test program is run in an environment where the KasperskyOS SDK is installed (on a computer running a Linux operating system). It does not utilize the KasperskyOS kernel, system software or applications of the solution.
To generate the source code of the security module and tests without compiling it, you need to use the --tests generate parameter when starting the nk-psl-gen-c compiler.
Test results are printed to the console. To print the test results to a file, you need to use the --test-output <path to file> parameter when starting the nk-psl-gen-c compiler.
Example test results:
# PAL test run
## Execute (1/2)
* Happy path: FAIL
Step 2/2: ExpectGrant Execute "This should not fail"
component/secure_platform/kss/nk/psl/nk-psl-gen-c/tests/examples/include/router.psl:38:5-40:3
* No rule: PASS
## IPC (2/2)
* Happy path: PASS
* No rule: PASS
## Security (2/2)
* Happy path: PASS
* No rule: PASS
The test results contain information about whether or not each test passed or failed. If a test failed, the results indicate which test case from the specific test did not pass, and provide the location of the description of the failed test case in the PSL file.
Page topPSL data types
The data types supported in the PSL language are presented in the table below.
PSL data types
Designations of types |
Description of types |
|---|---|
|
Unsigned integer |
|
Signed integer |
|
Boolean type The Boolean type includes two values: |
|
Text type |
|
The |
|
Text literal A text literal includes one immutable text value. Example definitions of text literals:
|
< |
Integer literal An integer literal includes one immutable integer value. Example definitions of integer literals:
|
< |
Variant type A variant type combines two or more types and may perform the role of either of them. Examples of definitions of variant types:
|
|
Dictionary A dictionary consists of one or more types of fields. A dictionary can be empty. Examples of dictionary definitions:
|
|
Tuple A tuple consists of fields of one or more types in the order in which the types are listed. A tuple can be empty. Examples of tuple definitions:
|
|
Set A set includes zero or more unique elements of the same type. Examples of set definitions:
|
|
List A list includes zero or more elements of the same type. Examples of list definitions:
|
|
Associative array An associative array includes zero or more entries of the "key-value" type with unique keys. Example of defining an associative array:
|
|
Array An array includes a defined number of elements of the same type. Example of defining an array:
|
|
Sequence A sequence includes from zero to the defined number of elements of the same type. Example of defining a sequence:
|
Aliases of certain PSL types
The nk/base.psl file from the KasperskyOS SDK defines the data types that are used as the types of parameters (or structural elements of parameters) and returned values for methods of various security models. Aliases and definitions of these types are presented in the table below.
Aliases and definitions of certain data types in PSL
Type alias |
Type definition |
|---|---|
|
Unsigned integer
|
|
Signed integer
|
|
Integer
|
|
Scalar literal
|
|
Literal
|
|
Type of security ID (SID)
|
|
Type of security ID (SID)
|
|
Dictionary containing fields for the SID and handle permissions mask
|
|
Type of data received by expressions of security models called in the
|
|
Type of data defining the conditions for conducting the security audit
|
Mapping IDL types to PSL types
Data types of the IDL language are used to describe the parameters of interface methods. The input data for security model methods have types from the PSL language. The set of data types in the IDL language differs from the set of data types in the PSL language. Parameters of interface methods transmitted in IPC messages can be used as input data for methods of security models, so the policy description developer needs to understand how IDL types are mapped to PSL types.
Integer types of IDL are mapped to integer types of PSL and to variant types of PSL that combine these integer types (including with other types). For example, signed integer types of IDL are mapped to the Signed type in PSL, and integer types of IDL are mapped to the ScalarLiteral type in PSL.
The Handle type in IDL is mapped to the HandleDesc type in PSL.
Unions and structures of IDL are mapped to PSL dictionaries.
Arrays and sequences of IDL are mapped to arrays and sequences of PSL, respectively.
String buffers in IDL are mapped to the text type in PSL.
Byte buffers in IDL are not currently mapped to PSL types, so the data contained in byte buffers cannot be used as inputs for security model methods.
Page topExamples of binding security model methods to security events
Before analyzing examples, you need to become familiar with the Base security model.
Processing the initiation of process startups
/* The KasperskyOS kernel and any process
* in the solution is allowed to start any
* process. */
execute { grant () }
/* The kernel is allowed to start a process
* of the Einit class. */
execute src=kl.core.Core, dst=Einit { grant () }
/* An Einit-class process is allowed
* to start any process in the solution. */
execute src=Einit { grant () }
Handling the startup of the KasperskyOS kernel
/* The KasperskyOS kernel is allowed to start.
* (This binding is necessary so that the security
* module can be notified of the kernel SID. The kernel starts irrespective
* of whether this is allowed by the solution security policy
* or denied. If the solution security policy denies the
* startup of the kernel, after startup the kernel will terminate its
* execution.) */
execute src=kl.core.Core, dst=kl.core.Core { grant () }
Handling IPC request forwarding
/* Any client in the solution is allowed to query
* any server and the KasperskyOS kernel. */
request { grant () }
/* A client of the Client class is allowed to query
* any server in the solution and the kernel. */
request src=Client { grant () }
/* Any client in the solution is allowed to query
* a server of the Server class. */
request dst=Server { grant () }
/* A client of the Client class is not allowed to
* query a server of the Server class. */
request src=Client dst=Server { deny () }
/* A client of the Client class is allowed to
* query a server of the Server class
* by calling the Ping method of the net.Net endpoint. */
request src=Client dst=Server endpoint=net.Net method=Ping {
grant ()
}
/* Any client in the solution is allowed to query
* a server of the Server class by calling the Send method
* of the endpoint with the MessExch interface. */
request dst=Server interface=MessExch method=Send {
grant ()
}
Handling IPC response forwarding
/* A server of the Server class is allowed to respond to
* queries of a Client-class client that
* calls the Ping method of the net.Net endpoint. */
response src=Server, dst=Client, endpoint=net.Net, method=Ping {
grant ()
}
/* The server containing the kl.drivers.KIDF component
* that provide endpoints with the monitor interface is allowed to
* respond to queries of a DriverManager-class client
* that uses these endpoints. */
response dst=DriverManager component=kl.drivers.KIDF interface=monitor {
grant ()
}
Handling the transmission of IPC responses containing error information
/* A server of the Server class is not allowed to notify a client
* of the Client class regarding errors that occur
* when the client queries the server by calling the
* Ping method of the net.Net endpoint. */
error src=Server, dst=Client, endpoint=net.Net, method=Ping {
deny ()
}
Handling queries sent by processes to the Kaspersky Security Module
/* A process of the Sdcard class will receive the
* "granted" decision from the Kaspersky Security Module
/* by calling the Register method of the security interface.
* (Using the security interface defined
* in the EDL description.) */
security src=Sdcard, method=Register {
grant ()
}
/* A process of the Sdcard class will receive the "denied" decision
* from the security module when calling the Comp.Register method
* of the security interface. (Using the security interface
* defined in the CDL description.) */
security src=Sdcard, method=Comp.Register {
deny ()
}
Using match sections
/* A client of the Client class is allowed to query
* a server of the Server class by calling the Send
* and Receive methods of the net endpoint. */
request src=Client, dst=Server, endpoint=net {
match method=Send { grant () }
match method=Receive { grant () }
}
/* A client of the Client class is allowed to query
* a server of the Server class by calling the Send
* and Receive methods of the sn.Net endpoint and the Write and
* Read methods of the sn.Storage endpoint. */
request src=Client, dst=Server {
match endpoint=sn.Net {
match method=Send { grant () }
match method=Receive { grant () }
}
match endpoint=sn.Storage {
match method=Write { grant () }
match method=Read { grant () }
}
}
Assigning audit profiles
/* Assigning the default global audit profile
* and initial audit runtime-level of 0 */
audit default = global 0
request src=Client, dst=Server {
/* Assigning a parent audit profile at the level of
* binding methods of security models to
* security events */
audit parent
match endpoint=net.Net, method=Send {
/* Assigning a child audit profile at the
* match section level */
audit child
grant ()
}
/* This match section applies a
* parent audit profile. */
match endpoint=net.Net, method=Receive {
grant ()
}
}
/* This binding of the security model method
* to the security event utilizes the
* global audit profile. */
response src=Client, dst=Server {
grant ()
}
Example descriptions of basic security policies for KasperskyOS-based solutions
Before analyzing examples, you need to become familiar with the Struct, Base and Flow security models.
Example 1
The solution security policy in this example allows any interaction between different processes of the Client, Server and Einit classes, and between these processes and the KasperskyOS kernel. The "granted" decision will always be received when these processes query the Kaspersky Security Module. This policy can be used only as a stub during the early stages of development of a KasperskyOS-based solution so that the Kaspersky Security Module does not interfere with interactions. It would be unacceptable to apply such a policy in a real-world KasperskyOS-based solution.
security.psl
execute: kl.core.Execute
use nk.base._
use EDL Einit
use EDL Client
use EDL Server
use EDL kl.core.Core
execute { grant () }
request { grant () }
response { grant () }
error { grant () }
security { grant () }
Example 2
The solution security policy in this example imposes limitations on queries sent from clients of the FsClient class to servers of the FsDriver class. When a client opens a resource controlled by a server of the FsDriver class, a finite-state machine in the unverified state is associated with this resource. A client of the FsClient class is allowed to read data from a resource controlled by a server of the FsDriver class only if the finite-state machine associated with this resource is in the verified state. To switch a resource-associated finite-state machine from the unverified state to the verified state, a process of the FsVerifier class needs to query the Kaspersky Security Module.
In a real-world KasperskyOS-based solution, this policy cannot be applied because it allows an excessive variety of interactions between different processes and between processes and the KasperskyOS kernel.
security.psl
execute: kl.core.Execute
use nk.base._
use nk.flow._
use nk.basic._
policy object file_state : Flow {
type States = "unverified" | "verified"
config = {
states : ["unverified" , "verified"],
initial : "unverified",
transitions : {
"unverified" : ["verified"],
"verified" : []
}
}
}
execute { grant () }
request { grant () }
response { grant () }
use EDL kl.core.Core
use EDL Einit
use EDL FsClient
use EDL FsDriver
use EDL FsVerifier
response src=FsDriver, endpoint=operationsComp.operationsImpl, method=Open {
file_state.init {sid: message.handle.handle}
}
request src=FsClient, dst=FsDriver, endpoint=operationsComp.operationsImpl, method=Read {
file_state.allow {sid: message.handle.handle, states: ["verified"]}
}
security src=FsVerifier, method=Approve {
file_state.enter {sid: message.handle.handle, state: "verified"}
}
Example descriptions of security audit profiles
Before analyzing examples, you need to become familiar with the Base, Regex and Flow security models.
Example 1
// Describing a trace security audit profile
// base – Base security model object
// session – Flow security model object
audit profile trace =
/* If the audit runtime-level is equal to 0, the audit covers
* base object rules when these rules return
* the "denied" result. */
{ 0 :
{ base :
{ kss : ["denied"]
}
}
/* If the audit runtime-level is equal to 1, the audit covers methods
* of the session object in the following cases:
* 1. Rules of the session object return a "granted"
* or "denied" result, and the finite-state machine is in a state
* other than closed.
* 2. A query expression of the session object is called, and the
* finite-state machine is in a state other than closed. */
, 1 :
{ session :
{ kss : ["granted", "denied"]
, omit : ["closed"]
}
}
/* If the audit runtime-level is equal to 2, the audit covers methods
* of the session object in the following cases:
* 1. Rules of the session object return a "granted"
* or "denied" result.
* 2. A query expression of the session object is called. */
, 2 :
{ session :
{ kss : ["granted", "denied"]
}
}
}
Example 2
// Describing a test security audit profile
// base – Base security model object
// re – Regex security model object
audit profile test =
/* If the audit runtime-level is equal to 0, rules of the base object
* and expressions of the re object are not covered by the audit. */
{ 0 :
{ base :
{ kss : []
}
, re :
{ kss : []
, emit : []
}
}
/* If the audit runtime-level is equal to 1, rules of the
* base object are not covered by the audit, and expressions of the
* re object are covered by the audit.*/
, 1 :
{ base :
{ kss : []
}
, re :
{ kss : []
, emit : ["match", "select"]
}
}
/* If the audit runtime-level is equal to 2, rules of the base object
* and expressions of the re object are covered by the audit. Rules
* of the base object are covered by the audit irrespective of the
* result that they return.*/
, 2 :
{ base :
{ kss : ["granted", "denied"]
}
, re :
{ kss : []
, emit : ["match", "select"]
}
}
}
Example descriptions of tests for KasperskyOS-based solution security policies
Example 1
/* Description of a test set that includes only one test. */
assert "some tests" {
/* Description of a test that includes four test cases. */
sequence "first sequence" {
/* It is expected that startup of a Server-class process is allowed.
* If this is true, the s variable will be assigned the SID value
* of the started Server-class process. */
s <- execute dst=Server
/* It is expected that startup of a Client-class process is allowed.
* If this is true, the c variable will be assigned the SID value
* of the started Client-class process. */
c <- execute dst=Client
/* It is expected that a client of the Client class is allowed to query
* a server of the Server class by calling the Ping method of the pingComp.pingImpl endpoint
* with the value parameter equal to 100. */
grant "Client calls Ping" request src=c dst=s endpoint=pingComp.pingImpl
method=Ping { value : 100 }
/* It is expected that a server of the Server class is not allowed to respond to a client
* of the Client class if the client calls the Ping method of the pingComp.pingImpl endpoint.
* (The IPC response does not contain any parameters because the Ping interface method
* has no output parameters.) */
deny "Server cannot respond" response src=s dst=c endpoint=pingComp.pingImpl
method=Ping {}
}
}
Example 2
/* Description of a test set that includes two tests. */
assert "ping tests"{
/* Initial part of each of the two tests */
setup {
s <- execute dst=Server
c <- execute dst=Client
}
/* Description of a test that includes two test cases. */
sequence "ping-ping is denied" {
/* It is expected that a client of the Client class is allowed to query
* a server of the Server class by calling the Ping method of the pingComp.pingImpl endpoint
* with the value parameter equal to 100. */
c ~> s : pingComp.pingImpl.Ping { value : 100 }
/* It is expected that a client of the Client class is not allowed to query
* a server of the Server class by once again calling the Ping method of the pingComp.pingImpl endpoint
* with the value parameter equal to 100. */
deny c ~> s : pingComp.pingImpl.Ping { value : 100 }
}
/* Description of a test that includes two test cases. */
sequence "ping-pong is granted" {
/* It is expected that a client of the Client class is allowed to query
* a server of the Server class by calling the Ping method of the pingComp.pingImpl endpoint
* with the value parameter equal to 100. */
c ~> s : pingComp.pingImpl.Ping { value: 100 }
/* It is expected that a client of the Client class is allowed to query
* a server of the Server class by calling the Pong method of the pingComp.pingImpl endpoint
* with the value parameter equal to 100. */
c ~> s : pingComp.pingImpl.Pong { value: 100 }
}
}
Example 3
/* Description of a test set that includes only one test. */
assert {
/* Description of a test that includes eight test cases. */
sequence {
storage <− execute dst=test.kl.UpdateStorage
manager <− execute dst=test.kl.UpdateManager
deployer <− execute dst=test.kl.UpdateDeployer
downloader <− execute dst=test.kl.UpdateDownloader
grant manager ~>
downloader:UpdateDownloader.Downloader.LoadPackage { url : ”url012345678” }
grant response src=downloader dst=manager endpoint=UpdateDownloader.Downloader
method=LoadPackage { handle : 29, result : 1 }
deny manager ~> deployer:UpdateDeployer.Deployer.Start { handle : 29 }
deny request src=manager dst=deployer endpoint=UpdateDeployer.Deployer
method=Start { handle : 29 }
}
}
Pred security model
The Pred security model lets you perform comparison operations.
A PSL file containing a description of the Pred security model is located in the KasperskyOS SDK at the following path:
toolchain/include/nk/basic.psl
Pred security model object
The basic.psl file contains a declaration that creates a Pred security model object named pred. Consequently, inclusion of the basic.psl file into the solution security policy description will create a Pred security model object by default.
A Pred security model object does not have any parameters and cannot be covered by a security audit.
It is not necessary to create additional Pred security model objects.
Pred security model methods
A Pred security model contains expressions that perform comparison operations and return values of the Boolean type. To call these expressions, use the following comparison operators:
- <
ScalarLiteral>==<ScalarLiteral> – "equals". - <
ScalarLiteral>!=<ScalarLiteral> – "does not equal". - <
Number><<Number> – "is less than". - <
Number><=<Number> – "is less than or equal to". - <
Number>><Number> – "is greater than". - <
Number>>=<Number> – "is greater than or equal to".
The Pred security model also contains the empty expression that lets you determine whether data contains its own structural elements. This expression returns values of the Boolean type. If data does not contain its own structural elements (for example, a set is empty), the expression returns true, otherwise it returns false. To call the expression, use the following construct:
pred.empty <Text | Set | List | Map | ()>
Bool security model
The Bool security model lets you perform logical operations.
A PSL file containing a description of the Bool security model is located in the KasperskyOS SDK at the following path:
toolchain/include/nk/basic.psl
Bool security model object
The basic.psl file contains a declaration that creates a Bool security model object named bool. Consequently, inclusion of the basic.psl file into the solution security policy description will create a Bool security model object by default.
A Bool security model object does not have any parameters and cannot be covered by a security audit.
It is not necessary to create additional Bool security model objects.
Bool security model methods
The Bool security model contains expressions that perform logical operations and return values of the Boolean type. To call these expressions, use the following logical operators:
!<Boolean> – "logical NOT".- <
Boolean>&&<Boolean> – "logical AND". - <
Boolean>||<Boolean> – "logical OR". - <
Boolean>==><Boolean> – "implication" (!<Boolean>||<Boolean>).
The Bool security model also contains the all, any and cond expressions.
The expression all performs a "logical AND" for an arbitrary number of values of Boolean type. It returns values of the Boolean type. It returns true if an empty list of values ([]) is passed via the parameter. To call the expression, use the following construct:
bool.all <List<Boolean>>
The expression any performs a "logical OR" for an arbitrary number of values of Boolean type. It returns values of the Boolean type. It returns false if an empty list of values ([]) is passed via the parameter. To call the expression, use the following construct:
bool.any <List<Boolean>>
cond expression performs a ternary conditional operation. Returns values of the ScalarLiteral type. To call the expression, use the following construct:
bool.cond
{ if : <Boolean> // Condition
, then : <ScalarLiteral> // Value returned when the condition is true
, else : <ScalarLiteral> // Value returned when the condition is false
}
In addition to expressions, the Bool security model includes the assert rule that works the same as the rule of the same name included in the Base security model.
Math security model
The Math security model lets you perform integer arithmetic operations.
A PSL file containing a description of the Math security model is located in the KasperskyOS SDK at the following path:
toolchain/include/nk/basic.psl
Math security model object
The basic.psl file contains a declaration that creates a Math security model object named math. Consequently, inclusion of the basic.psl file into the solution security policy description will create a Math security model object by default.
A Math security model object does not have any parameters and cannot be covered by a security audit.
It is not necessary to create additional Math security model objects.
Math security model methods
The Math security model contains expressions that perform integer arithmetic operations. To call a part of these expressions, use the following arithmetic operators:
- <
Number>+<Number> – "addition". Returns values of theNumbertype. - <
Number>-<Number> – "subtraction". Returns values of theNumbertype. - <
Number>*<Number> – "multiplication". Returns values of theNumbertype.
The other expressions are as follows:
neg<Signed> – "change number sign". Returns values of theSignedtype.abs<Signed> – "get module of number". Returns values of theSignedtype.sum<List<Number>> – "add numbers from list". Returns values of theNumbertype. It returns0if an empty list of values ([]) is passed via the parameter.product<List<Number>> – "multiply numbers from list". Returns values of theNumbertype. It returns1if an empty list of values ([]) is passed via the parameter.
To call these expressions, use the following construct:
math.<expression name> <parameter>
Struct security model
The Struct security model lets you obtain access to structural data elements.
A PSL file containing a description of the Struct security model is located in the KasperskyOS SDK at the following path:
toolchain/include/nk/basic.psl
Struct security model object
The basic.psl file contains a declaration that creates a Struct security model object named struct. Consequently, inclusion of the basic.psl file into the solution security policy description will create a Struct security model object by default.
A Struct security model object does not have any parameters and cannot be covered by a security audit.
It is not necessary to create additional Struct security model objects.
Struct security model methods
The Struct security model contains expressions that provide access to structural data elements. To call these expressions, use the following constructs:
- <
{...}>.<field name> – "get access to dictionary field". the type of returned data corresponds to the type of dictionary field. - <
List | Set | Sequence | Array>.[<element number>]– "get access to data element". The type of returned data corresponds to the type of elements. The numbering of elements starts with zero. When out of bounds of dataset, the expression terminates with an error and the Kaspersky Security Module returns the "denied" decision. - <
HandleDesc>.handle– "get SID". Returns values of theHandletype. (For details on the correlation between handles and SID values, see "Resource Access Control"). - <
HandleDesc>.rights– "get handle permissions mask". Returns values of theUInt32type.
Parameters of interface methods are saved in a special dictionary named message. To obtain access to an interface method parameter, use the following construct:
message.<interface method parameter name>
The parameter name is specified in accordance with the IDL description.
To obtain access to structural elements of parameters, use the constructs corresponding to expressions of the Struct security model.
To use expressions of the Struct security model, the security event description must be sufficiently precise so that it corresponds to IPC messages of the same type (for more details, see "Binding methods of security models to security events"). IPC messages of this type must contain the defined parameters of the interface method, and the interface method parameters must contain the defined structural elements.
Base security model
The Base security model lets you implement basic logic.
A PSL file containing a description of the Base security model is located in the KasperskyOS SDK at the following path:
toolchain/include/nk/base.psl
Base security model object
The base.psl file contains a declaration that creates a Base security model object named base. Consequently, inclusion of the base.psl file into the solution security policy description will create a Base security model object by default. Methods of this object can be called without indicating the object name.
A Base security model object does not have any parameters.
A Base security model object can be covered by a security audit. There are no audit conditions specific to the Base security model.
It is necessary to create additional objects of the Base security model in the following cases:
- You need to configure a security audit differently for different objects of the Base security model (for example, you can apply different audit profiles or different audit configurations of the same profile for different objects).
- You need to distinguish between calls of methods provided by different objects of the Base security model (audit data includes the name of the security model method and the name of the object that provides this method, so you can verify that the method of a specific object was called).
Base security model methods
The Base security model contains the following rules:
grant ()It has a parameter of the
()type. It returns the "granted" result.Example:
/* A client of the foo class is allowed
* to query a server of the bar class. */
request src=foo dst=bar { grant () }
assert<Boolean>It returns the "granted" result if the
truevalue is passed via the parameter. Otherwise it returns the "denied" result.Example:
/* Any client in the solution will be allowed to query a server of the foo class
* by calling the Send method of the net.Net endpoint if the port parameter
* of the Send method will be used to pass a value greater than 80. Otherwise any
* client in the solution will be prohibited from querying a server of the
* foo class by calling the Send method of the net.Net endpoint. */
request dst=foo endpoint=net.Net method=Send { assert (message.port > 80) }
deny<Boolean | ()>It returns the "denied" result if the
trueor()value is passed via the parameter. Otherwise it returns the "granted" result.Example:
/* A server of the foo class is not allowed to
* respond to a client of the bar class. */
response src=foo dst=bar { deny () }
set_level<UInt8>It sets the security audit runtime-level equal to the value passed via this parameter. It returns the "granted" result. (For more details about the security audit runtime-level, see "Describing security audit profiles".)
Example:
/* A process of the foo class will receive the "allowed" decision from the
* Kaspersky Security Module if it calls the
* SetAuditLevel security interface method to change the security audit runtime-level. */
security src=foo method=SetAuditLevel { set_level (message.audit_level) }
Regex security model
The Regex security model lets you implement text data validation based on statically defined regular expressions.
A PSL file containing a description of the Regex security model is located in the KasperskyOS SDK at the following path:
toolchain/include/nk/regex.psl
Regex security model object
The regex.psl file contains a declaration that creates a Regex security model object named re. Consequently, inclusion of the regex.psl file into the solution security policy description will create a Regex security model object by default.
A Regex security model object does not have any parameters.
A Regex security model object can be covered by a security audit. In this case, you also need to define the audit conditions specific to the Regex security model. To do so, use the following constructs in the audit configuration description:
emit : ["match"]– the audit is performed if thematchmethod is called.emit : ["select"]– the audit is performed if theselectmethod is called.emit : ["match", "select"]– the audit is performed if thematchorselectmethod is called.emit : []– the audit is not performed.
It is necessary to create additional objects of the Regex security model in the following cases:
- You need to configure a security audit differently for different objects of the Regex security model (for example, you can apply different audit profiles or different audit configurations of the same profile for different objects).
- You need to distinguish between calls of methods provided by different objects of the Regex security model (audit data includes the name of the security model method and the name of the object that provides this method, so you can verify that the method of a specific object was called).
Regex security model methods
The Regex security model contains the following expressions:
match {text :<Text>, pattern :<Text>}Returns a value of the
Booleantype. If the specifiedtextmatches thepatternregular expression, it returnstrue. Otherwise it returnsfalse.Example:
assert (re.match {text : message.text, pattern : "[0-9]*"})
select {text :<Text>}It is intended to be used as an expression that verifies fulfillment of the conditions in the
choiceconstruct (for details on thechoiceconstruct, see "Binding methods of security models to security events"). It checks whether the specifiedtextmatches regular expressions. Depending on the results of this check, various options for security event handling can be performed.Example:
choice (re.select {text : "hello world"}) {
"hello\ .*": grant ()
".*world" : grant ()
_ : deny ()
}
Syntax of regular expressions of the Regex security model
A regular expression for the match method of the Regex security model can be written in two ways: within the multi-line regex block or as a text literal.
When writing a regular expression as a text literal, all backslash instances must be doubled.
For example, the following two regular expressions are identical:
// Regular expression within the multi-line regex block
{ pattern:
```regex
Hello\ world\!
```
, text: "Hello world!"
}
// Regular expression as a text literal (doubled backslash)
{ pattern: "Hello\\ world\\!"
, text: "Hello world!"
}
Regular expressions for the select method of the Regex security model are written as text literals with a double backslash.
A regular expression is defined as a template string and may contain the following:
- Literals (ordinary characters)
- Metacharacters (characters with special meanings)
- White-space characters
- Character sets
- Character groups
- Operators for working with characters
Regular expressions are case sensitive.
Literals and metacharacters in regular expressions
- A literal can be any ASCII character except the metacharacters
.()*&|!?+[]\and a white-space character. (Unicode characters are not supported.)For example, the regular expression
KasperskyOScorresponds to the textKasperskyOS. - Metacharacters have special meanings that are presented in the table below.
Special meanings of metacharacters
Metacharacter
Special meaning
[]Square brackets (braces) denote the beginning and end of a set of characters.
()Round brackets (parentheses) denote the beginning and end of a group of characters.
*An asterisk denotes an operator indicating that the character preceding it can repeat zero or more times.
+A plus sign denotes an operator indicating that the character preceding it can repeat one or more times.
?A question mark denotes an operator indicating that the character preceding it can repeat zero or one time.
!An exclamation mark denotes an operator excluding the subsequent character from the list of valid characters.
|A vertical line denotes an operator for selection between characters (logically close to the "OR" conjunction).
&An ampersand denotes an operator for overlapping of multiple conditions (logically close to the "AND" conjunction).
.A dot denotes any character.
For example, the regular expression
K.Scorresponds to the sequences of charactersKOS,KoS,KESand a multitude of other sequences consisting of three characters that begin withKand end withS, and in which the second character can be any character: literal, metacharacter, or dot.\\<metaSymbol>A backslash indicates that the metacharacter that follows it will lose its special meaning and instead be interpreted as a literal. A backslash placed before a metacharacter is known as an escape character.
For example, a regular expression that consists of a dot metacharacter (
.) corresponds to any character. However, a regular expression that consists of a backslash with a dot (\.) corresponds to only a dot character.Accordingly, a backslash also escapes another subsequent backslash. For example, the regular expression
C:\\Userscorresponds to the sequence of charactersC:\Users. - The
^and$characters are not used to designate the start and end of a line.
White-space characters in regular expressions
- A space character has an ASCII code of
20in a hexadecimal number system and has an ASCII code of40in an octal number system. Although a space character does not infer any special meaning, it must be escaped to avoid any ambiguous interpretation by the regular expression interpreter.For example, the regular expression
Hello\ worldcorresponds to the sequence of charactersHello world. \rCarriage return character.
\nLine break character.
\tHorizontal tab character.
Definition of a character based on its octal or hexadecimal code in regular expressions
\x{<hex>}Definition of a character using its
hexcode from the ASCII character table. The character code must be less than0x100.For example, the regular expression
Hello\x{20}worldcorresponds to the sequence of charactersHello world.\o{<octal>}Definition of a character using its
octalcode from the ASCII character table. The character code must be less than0o400.For example, the regular expression
\o{75}corresponds to the=character.
Sets of characters in regular expressions
A character set is defined within square brackets [] as a list or range of characters. A character set tells the regular expression interpreter that only one of the characters listed in the set or range of characters can be at this specific location in a sequence of characters. A character set cannot be left blank.
[<BracketSpec>]– character set.One character corresponds to any character from the
BracketSpeccharacter set.For example, the regular expression
K[OE]Scorresponds to the sequences of charactersKOSandKES.[^<BracketSpec>]– inverted character set.One character corresponds to any character that is not in the
BracketSpeccharacter set.For example, the regular expression
K[^OE]Scorresponds to the sequences of charactersKAS,K8Sand any other sequences consisting of three characters that begin withKand end withS, excludingKOSandKES.
The BracketSpec character set can be listed explicitly or can be defined as a range of characters. When defining a range of characters, the first and last character in the set must be separated with a hyphen.
[<Digit1>-<DigitN>]Any number from the range
Digit1,Digit2, ... ,DigitN.For example, the regular expression
[0-9]corresponds to any numerical digit. The regular expressions[0-9]and[0123456789]are identical.Please note that a range is defined by one character before a hyphen and one character after the hyphen. The regular expression
[1-35]corresponds only to the characters1,2,3and5, and does not represent the range of numbers from1to35.[<Letter1>-<LetterN>]Any English letter from the range
Letter1,Letter2, ... ,LetterN(these letters must be in the same case).For example, the regular expression
[a-zA-Z]corresponds to all letters in uppercase and lowercase from the ASCII character table.
The ASCII code for the upper boundary character of a range must be higher than the ASCII code for the lower boundary character of the range.
For example, the regular expressions [5-2] or [z-a] are invalid.
The hyphen (minus) - character is interpreted as a special character only within a set of characters. Outside of a character set, a hyphen is a literal. For this reason, the \ metacharacter does not have to precede a hyphen. To use a hyphen as a literal within a character set, it must be indicated first or last in the set.
Examples:
The regular expressions [-az] and [az-] correspond to the characters a, z and -.
The regular expression [a-z] corresponds to any of the 26 English letters from a to z in lowercase.
The regular expression [-a-z] corresponds to any of the 26 English letters from a to z in lowercase and -.
The circumflex (caret character) ^ is interpreted as a special character only within a character set when it is located directly after an opening square bracket. Outside of a character set, a circumflex is a literal. For this reason, the \ metacharacter does not have to precede a circumflex. To use a circumflex as a literal within a character set, it must be indicated in a location other than first in the set.
Examples:
The regular expression [0^9] correspond to the characters 0, 9 and ^.
The regular expression [^09] corresponds to any character except 0 and 9.
Within a character set, the metacharacters *.&|!?+ lose their special meaning and are instead interpreted as literals. Therefore, they do not have to be preceded by the \ metacharacter. The backslash \ retains its special meaning within a character set.
For example, the regular expressions [a.] and [a\.] are identical and correspond to the character a and a dot interpreted as a literal.
Groups of characters and operators in regular expressions
A character group uses parentheses () to distinguish its portion (subexpression) within a regular expression. Groups are normally used to allocate subexpressions as operands. Groups can be embedded into each other.
Operators are applied to more than one character in a regular expression only if they are immediately before or after the definition of a set or group of characters. If this is the case, the operator is applied to the entire group or set of characters.
The syntax contains definitions of the following operators (listed in descending order of their priority):
!<Expression>, whereExpressioncan be a character, set or group of characters.This operator excludes the
Expressionfrom the list of valid expressions.Examples:
The regular expression
K!OScorresponds to the sequences of charactersKoS,KES, and a multitude of other sequences that consist of three characters and begin withKand end withS, excludingKOS.The regular expression
K!(OS)corresponds to the sequences of charactersKos,KES,KOT, and a multitude of other sequences that consist of three characters and begin withK, excludingKOS.The regular expression
K![OE]Scorresponds to the sequences of charactersKoS,KeS,K;S, and a multitude of other sequences that consist of three characters and begin withKand end withS, excludingKOSandKES.- <
Expression>*, whereExpressioncan be a character, set or group of characters.This operator means that the
Expressionmay occur in the specific position zero or more times.Examples:
The regular expression
0-9*corresponds to the sequences of characters0-,0-9,0-99, ... .The regular expression
(0-9)*corresponds to the empty sequence""and the sequences of characters0-9,0-90-9, ... .The regular expression
[0-9]*corresponds to the empty sequence""and any non-empty sequence of numbers. - <
Expression>+, whereExpressioncan be a character, set or group of characters.This operator means that the
Expressionmay occur in the specific position one or more times.Examples:
The regular expression
0-9+corresponds to the sequences of characters0-9,0-99,0-999, ... .The regular expression
(0-9)+corresponds to the sequences of characters0-9,0-90-9, ... .The regular expression
[0-9]+corresponds to any non-empty sequence of numbers. - <
Expression>?, whereExpressioncan be a character, set or group of characters.This operator means that the
Expressionmay occur in the specific position zero or one time.Examples:
The regular expression
https?://corresponds to the sequences of charactershttp://andhttps://.The regular expression
K(aspersky)?OScorresponds to the sequences of charactersKOSandKasperskyOS. - <
Expression1><Expression2> – concatenation.Expression1andExpression2can be characters, sets or groups of characters.This operator does not have a specific designation. In the resulting expression,
Expression2followsExpression1.For example, concatenation of the sequences of characters
microandkernelwill result in the sequence of charactersmicrokernel. - <
Expression1>|<Expression2> – disjunction.Expression1andExpression2can be characters, sets or groups of characters.This operator selects either
Expression1orExpression2.Examples:
The regular expression
KO|EScorresponds to the sequences of charactersKOandES, but notKOSorKESbecause the concatenation operator has a higher priority than the disjunction operator.The regular expression
Press (OK|Cancel)corresponds to the sequences of charactersPress OKorPress Cancel.The regular expression
[0-9]|()corresponds to numbers from0to9or an empty string. - <
Expression1>&<Expression2> – conjunction.Expression1andExpression2can be characters, sets or groups of characters.This operator intersects the result of
Expression1with the result ofExpression2.Examples:
The regular expression
[0-9]&[^3]corresponds to numbers from0to9, excluding3.The regular expression
[a-zA-Z]&()corresponds to all English letters and an empty string.
HashSet security model
The HashSet security model lets you associate resources with one-dimensional tables of unique values of the same type, add or delete these values, and check whether a defined value is in the table. For example, a process of the network server can be associated with the set of ports that this server is allowed to open. This association can be used to check whether the server is allowed to initiate the opening of a port.
A PSL file containing a description of the HashSet security model is located in the KasperskyOS SDK at the following path:
toolchain/include/nk/hashmap.psl
HashSet security model object
To use the HashSet security model, you need to create an object or objects of this model.
A HashSet security model object contains a pool of one-dimensional tables of the same size intended for storing the values of one type. A resource can be associated with only one table from the tables pool of each HashSet security model object.
A HashSet security model object has the following parameters:
type Entry– type of values in tables (these can be integer types,Booleantype, and dictionaries and tuples based on integer types and theBooleantype).config– configuration of the pool of tables:set_size– size of the table.pool_size– number of tables in the pool.
All parameters of a HashSet security model object are required.
Example:
policy object S : HashSet {
type Entry = UInt32
config =
{ set_size : 5
, pool_size : 2
}
}
A HashSet security model object can be covered by a security audit. There are no audit conditions specific to the HashSet security model.
It is necessary to create multiple objects of the HashSet security model in the following cases:
- You need to configure a security audit differently for different objects of the HashSet security model (for example, you can apply different audit profiles or different audit configurations of the same profile for different objects).
- You need to distinguish between calls of methods provided by different objects of the HashSet security model (audit data includes the name of the security model method and the name of the object that provides this method, so you can verify that the method of a specific object was called).
- You need to use tables of different sizes and/or with different types of values.
HashSet security model init rule
init {sid : <Sid>}
It associates a free table from the tables pool with the sid resource. If the free table contains values after its previous use, these values are deleted.
It returns the "allowed" result if an association was created between the table and the sid resource.
It returns the "denied" result in the following cases:
- There are no free tables in the pool.
- The
sidresource is already associated with a table from the tables pool of the HashSet security model object being used. - The
sidvalue is outside of the permissible range.
Example:
/* A process of the Server class will be allowed to start if,
* at startup initiation, an association will be created
* between this process and the table. Otherwise the startup of a process of the
* Server class will be denied. */
execute dst=Server {
S.init {sid : dst_sid}
}
HashSet security model fini rule
fini {sid : <Sid>}
It deletes the association between the table and the sid resource (the table becomes free).
It returns the "allowed" result if the association between the table and the sid resource was deleted.
It returns the "denied" result in the following cases:
- The
sidresource is not associated with a table from the tables pool of the HashSet security model object being used. - The
sidvalue is outside of the permissible range.
HashSet security model add rule
add {sid : <Sid>, entry : <Entry>}
It adds the entry value to the table associated with the sid resource.
It returns the "allowed" result in the following cases:
- The rule added the
entryvalue to the table associated with thesidresource. - The table associated with the
sidresource already contains theentryvalue.
It returns the "denied" result in the following cases:
- The table associated with the
sidresource is completely full. - The
sidresource is not associated with a table from the tables pool of the HashSet security model object being used. - The
sidvalue is outside of the permissible range.
Example:
/* A process of the Server class will receive the "allowed" decision from
* the Kaspersky Security Module by calling the
* Add security interface method if, when this method is called, the value
* 5 will be added to the table associated with this
* process, or is already in the table. Otherwise
* a process of the Server class will receive the "denied" decision from the
* security module by calling the
* Add security interface method. */
security src=Server, method=Add {
S.add {sid : src_sid, entry : 5}
}
HashSet security model remove rule
remove {sid : <Sid>, entry : <Entry>}
It deletes the entry value from the table associated with the sid resource.
It returns the "allowed" result in the following cases:
- The rule deleted the
entryvalue from the table associated with thesidresource. - The table associated with the
sidresource does not contain theentryvalue.
It returns the "denied" result in the following cases:
- The
sidresource is not associated with a table from the tables pool of the HashSet security model object being used. - The
sidvalue is outside of the permissible range.
HashSet security model contains expression
contains {sid : <Sid>, entry : <Entry>}
It checks whether the entry value is in the table associated with the sid resource.
It returns a value of the Boolean type. If the entry value is in the table associated with the sid resource, it returns true. Otherwise it returns false.
It runs incorrectly in the following cases:
- The
sidresource is not associated with a table from the tables pool of the HashSet security model object being used. - The
sidvalue is outside of the permissible range.
When the expression runs incorrectly, the Kaspersky Security Module returns the "denied" decision.
Example:
/* A process of the Server class will receive the "allowed" decision from
* the Kaspersky Security Module by calling the
* Check security interface method if the value 42 is in the table
* associated with this process. Otherwise a process of the
* Server class will receive the "denied" decision from the security module
/* by calling the Check security interface method. */
security src=Server, method=Check {
assert(S.contains {sid : src_sid, entry : 42})
}
StaticMap security model
The StaticMap security model lets you associate resources with two-dimensional "key–value" tables, read and modify the values of keys. For example, a process of the driver can be associated with the MMIO memory region that this driver is allowed to use. This will require two keys whose values define the starting address and the size of the MMIO memory region. This association can be used to check whether the driver can query the MMIO memory region that it is attempting to access.
Keys in the table have the same type but are unique and immutable. The values of keys in the table have the same type.
There are two simultaneous instances of the table: base instance and working instance. Both instances are initialized by the same data. Changes are made first to the working instance and then can be added to the base instance, or vice versa: the working instance can be changed by using previous values from the base instance. The values of keys can be read from the base instance or working instance of the table.
A PSL file containing a description of the StaticMap security model is located in the KasperskyOS SDK at the following path:
toolchain/include/nk/staticmap.psl
StaticMap security model object
To use the StaticMap security model, you need to create an object or objects of this model.
A StaticMap security model object contains a pool of two-dimensional "key–value" tables that have the same size. A resource can be associated with only one table from the tables pool of each StaticMap security model object.
A StaticMap security model object has the following parameters:
type Value– type of values of keys in tables (integer types are supported).config– configuration of the pool of tables:keys– table containing keys and their default values (keys have theKey = Text | List<UInt8>type).pool_size– number of tables in the pool.
All parameters of a StaticMap security model object are required.
Example:
policy object M : StaticMap {
type Value = UInt16
config =
{ keys:
{ "k1" : 0
, "k2" : 1
}
, pool_size : 2
}
}
A StaticMap security model object can be covered by a security audit. There are no audit conditions specific to the StaticMap security model.
It is necessary to create multiple objects of the StaticMap security model in the following cases:
- You need to configure a security audit differently for different objects of the StaticMap security model (for example, you can apply different audit profiles or different audit configurations of the same profile for different objects).
- You need to distinguish between calls of methods provided by different objects of the StaticMap security model (audit data includes the name of the security model method and the name of the object that provides this method, so you can verify that the method of a specific object was called).
- You need to use tables with different sets of keys and/or different types of key values.
StaticMap security model init rule
init {sid : <Sid>}
It associates a free table from the tables pool with the sid resource. Keys are initialized by the default values.
It returns the "allowed" result if an association was created between the table and the sid resource.
It returns the "denied" result in the following cases:
- There are no free tables in the pool.
- The
sidresource is already associated with a table from the tables pool of the StaticMap security model object being used. - The
sidvalue is outside of the permissible range.
Example:
/* A process of the Server class will be allowed to start if,
* at startup initiation, an association will be created
* between this process and the table. Otherwise the startup of a process of the
* Server class will be denied. */
execute dst=Server {
M.init {sid : dst_sid}
}
StaticMap security model fini rule
fini {sid : <Sid>}
It deletes the association between the table and the sid resource (the table becomes free).
It returns the "allowed" result if the association between the table and the sid resource was deleted.
It returns the "denied" result in the following cases:
- The
sidresource is not associated with a table from the tables pool of the StaticMap security model object being used. - The
sidvalue is outside of the permissible range.
StaticMap security model set rule
set {sid : <Sid>, key : <Key>, value : <Value>}
It assigns the specified value to the specified key in the working instance of the table associated with the sid resource.
It returns the "allowed" result if the specified value was assigned to the specified key in the working instance of the table associated with the sid resource. (The current value of the key will be overwritten even if it is equal to the new value.)
It returns the "denied" result in the following cases:
- The specified
keyis not in the table associated with thesidresource. - The
sidresource is not associated with a table from the tables pool of the StaticMap security model object being used. - The
sidvalue is outside of the permissible range.
Example:
/* A process of the Server class will receive the "allowed" decision from
* the Kaspersky Security Module by calling the
* Set security interface method if, when this method is called, the value 2
* will be assigned to key k1 in the working instance of the table
* associated with this process. Otherwise a process of the
* Server class will receive the "denied" decision from the security module
/* by calling the Set security interface method. */
security src=Server, method=Set {
M.set {sid : src_sid, key : "k1", value : 2}
}
StaticMap security model commit rule
commit {sid : <Sid>}
It copies the values of keys from the working instance to the base instance of the table associated with the sid resource.
It returns the "allowed" result if the values of keys were copied from the working instance to the base instance of the table associated with the sid resource.
It returns the "denied" result in the following cases:
- The
sidresource is not associated with a table from the tables pool of the StaticMap security model object being used. - The
sidvalue is outside of the permissible range.
StaticMap security model rollback rule
rollback {sid : <Sid>}
It copies the values of keys from the base instance to the working instance of the table associated with the sid resource.
It returns the "allowed" result if the values of keys were copied from the base instance to the working instance of the table associated with the sid resource.
It returns the "denied" result in the following cases:
- The
sidresource is not associated with a table from the tables pool of the StaticMap security model object being used. - The
sidvalue is outside of the permissible range.
StaticMap security model get expression
get {sid : <Sid>, key : <Key>}
It returns the value of the specified key from the base instance of the table associated with the sid resource.
It returns a value of the Value type.
It runs incorrectly in the following cases:
- The specified
keyis not in the table associated with thesidresource. - The
sidresource is not associated with a table from the tables pool of the StaticMap security model object being used. - The
sidvalue is outside of the permissible range.
When the expression runs incorrectly, the Kaspersky Security Module returns the "denied" decision.
Example:
/* A process of the Server class will receive the "allowed" decision from
* the Kaspersky Security Module by calling the
* Get security interface method if the value of key k1 in the base
* instance of the table associated with this process
* is not zero. Otherwise a process of the Server class will receive
* the "denied" decision from the security module
* by calling the Get security interface method. */
security src=Server, method=Get {
assert(M.get {sid : src_sid, key : "k1"} != 0)
}
StaticMap security model get_uncommited expression
get_uncommited {sid: <Sid>, key: <Key>}
It returns the value of the specified key from the working instance of the table associated with the sid resource.
It returns a value of the Value type.
It runs incorrectly in the following cases:
- The specified
keyis not in the table associated with thesidresource. - The
sidresource is not associated with a table from the tables pool of the StaticMap security model object being used. - The
sidvalue is outside of the permissible range.
When the expression runs incorrectly, the Kaspersky Security Module returns the "denied" decision.
Page topFlow security model
The Flow security model lets you associate resources with finite-state machines, receive and modify the states of finite-state machines, and check whether the state of the finite-state machine is within the defined set of states. For example, a process can be associated with a finite-state machine to allow or prohibit this process from using storage and/or the network depending on the state of the finite-state machine.
A PSL file containing a description of the Flow security model is located in the KasperskyOS SDK at the following path:
toolchain/include/nk/flow.psl
Flow security model object
To use the Flow security model, you need to create an object or objects of this model.
One Flow security model object lets you associate a set of resources with a set of finite-state machines that have the same configuration. A resource can be associated with only one finite-state machine of each Flow security model object.
A Flow security model object has the following parameters:
type State– type that determines the set of states of the finite-state machine (variant type that combines text literals).config– configuration of the finite-state machine:states– set of states of the finite-state machine (must match the set of states defined by theStatetype).initial– initial state of the finite-state machine.transitions– description of the permissible transitions between states of the finite-state machine.
All parameters of a Flow security model object are required.
Example:
policy object service_flow : Flow {
type State = "sleep" | "started" | "stopped" | "finished"
config = { states : ["sleep", "started", "stopped", "finished"]
, initial : "sleep"
, transitions : { "sleep" : ["started"]
, "started" : ["stopped", "finished"]
, "stopped" : ["started", "finished"]
}
}
}
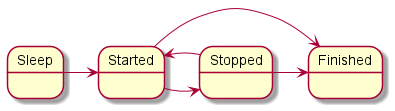
Diagram of finite-state machine states in the example
A Flow security model object can be covered by a security audit. You can also define the audit conditions specific to the Flow security model. To do so, use the following construct in the audit configuration description:
omit : [<"state 1">[,] ...] – the audit is not performed if the finite-state machine is in one of the listed states.
It is necessary to create multiple objects of the Flow security model in the following cases:
- You need to configure a security audit differently for different objects of the Flow security model (for example, you can apply different audit profiles or different audit configurations of the same profile for different objects).
- You need to distinguish between calls of methods provided by different objects of the Flow security model (audit data includes the name of the security model method and the name of the object that provides this method, so you can verify that the method of a specific object was called).
- You need to use finite-state machines with different configurations.
Flow security model init rule
init {sid : <Sid>}
It creates a finite-state machine and associates it with the sid resource. The created finite-state machine has the configuration defined in the settings of the Flow security model object being used.
It returns the "granted" result if an association was created between the finite-state machine and the sid resource.
It returns the "denied" result in the following cases:
- The
sidresource is already associated with a finite-state machine of the Flow security model object being used. - The
sidvalue is outside of the permissible range.
Example:
/* A process of the Server class will be allowed to start
* if, at startup initiation, an association will be created
* between this process and the finite-state machine.
* Otherwise the startup of the Server-class process will be denied. */
execute dst=Server {
service_flow.init {sid : dst_sid}
}
Flow security model fini rule
fini {sid : <Sid>}
It deletes the association between the finite-state machine and the sid resource. The finite-state machine that is no longer associated with the resource is destroyed.
It returns the "granted" result if the association between the finite-state machine and the sid resource was deleted.
It returns the "denied" result in the following cases:
- The
sidresource is not associated with a finite-state machine of the Flow security model object being used. - The
sidvalue is outside of the permissible range.
Flow security model enter rule
enter {sid : <Sid>, state : <State>}
It switches the finite-state machine associated with the sid resource to the specified state.
It returns the "granted" result if the finite-state machine associated with the sid resource was switched to the specified state.
It returns the "denied" result in the following cases:
- The transition to the specified
statefrom the current state is not permitted by the configuration of the finite-state machine associated with thesidresource. - The
sidresource is not associated with a finite-state machine of the Flow security model object being used. - The
sidvalue is outside of the permissible range.
Example:
/* Any client in the solution will be allowed to query
* a server of the Server class if the finite-state machine
* associated with this server will be switched to
* the "started" state when initiating the query. Otherwise
* any client in the solution will be denied to query
* a server of the Server class. */
request dst=Server {
service_flow.enter {sid : dst_sid, state : "started"}
}
Flow security model allow rule
allow {sid : <Sid>, states : <Set<State>>}
It verifies that the state of the finite-state machine associated with the sid is in the set of defined states.
It returns the "granted" result if the state of the finite-state machine associated with the sid resource is in the set of defined states.
It returns the "denied" result in the following cases:
- The state of the finite-state machine associated with the
sidresource is not in the set of definedstates. - The
sidresource is not associated with a finite-state machine of the Flow security model object being used. - The
sidvalue is outside of the permissible range.
Example:
/* Any client in the solution is allowed to query a server
* of the Server class if the finite-state machine associated with this server
* is in the started or stopped state. Otherwise any client
* in the solution will be prohibited from querying a server of the Server class. */
request dst=Server {
service_flow.allow {sid : dst_sid, states : ["started", "stopped"]}
}
Flow security model query expression
query {sid : <Sid>}
It is intended to be used as an expression that verifies fulfillment of the conditions in the choice construct (for details on the choice construct, see "Binding methods of security models to security events"). It checks the state of the finite-state machine associated with the sid resource. Depending on the results of this check, various options for security event handling can be performed.
It runs incorrectly in the following cases:
- The
sidresource is not associated with a finite-state machine of the Flow security model object being used. - The
sidvalue is outside of the permissible range.
When the expression runs incorrectly, the Kaspersky Security Module returns the "denied" decision.
Example:
/* Any client in the solution is allowed to query
* a server of the ResourceDriver class if the finite-state machine
* associated with this server is in the
* "started" or "stopped" state. Otherwise any client in the solution
* is prohibited from querying a server of the ResourceDriver class. */
request dst=ResourceDriver {
choice (service_flow.query {sid : dst_sid}) {
"started" : grant ()
"stopped" : grant ()
_ : deny ()
}
}
Mic security model
The Mic security model lets you implement mandatory integrity control. In other words, this security model provides the capability to manage data streams between different processes and between processes and the KasperskyOS kernel by controlling the integrity levels of processes, the kernel, and resources that are used via IPC.
In Mic security model terminology, processes and the kernel are called subjects while resources are called objects. However, the information provided in this section slightly deviates from the terminology of the Mic security model. In this section, the term "object" is not used to refer to a "resource".
Data streams are generated between subjects when the subjects interact via IPC.
The integrity level of a subject/resource is the level of trust afforded to the subject/resource. The degree of trust in a subject depends on whether the subject interacts with untrusted external software/hardware systems or whether the subject has a proven quality level, for example. (The kernel has a high level of integrity.) The degree of trust in a resource depends on whether this resource was created by a trusted subject within a software/hardware system running KasperskyOS or if it was received from an untrusted external software/hardware system, for example.
The Mic security model is characterized by the following provisions:
- By default, data streams from subjects with less integrity to subjects with higher integrity are prohibited. You have the option of permitting such data streams if you can guarantee that the subjects with higher integrity will not be compromised.
- A resource consumer is prohibited from writing data to a resource if the integrity level of the resource is higher than the integrity level of the resource consumer.
- By default, a resource consumer is prohibited from reading data from a resource if the integrity level of the resource is lower than the integrity level of the resource consumer. You have the option to allow the resource consumer to perform such an operation if you can guarantee that the resource consumer will not be compromised.
Methods of the Mic security model let you assign integrity levels to subjects and resources, check the permissibility of data streams based on a comparison of integrity levels, and elevate the integrity levels of resources.
A PSL file containing a description of the Mic security model is located in the KasperskyOS SDK at the following path:
toolchain/include/nk/mic.psl
For an example of using the Mic security model, we can examine a secure software update for a software/hardware system running KasperskyOS. Four processes are involved in the update:
Downloaderis a low-integrity process that downloads a low-integrity update image from a remote server on the Internet.Verifieris a high-integrity process that verifies the digital signature of the low-integrity update image (high-integrity process that can read data from a low-integrity resource).FileSystemis a high-integrity process that manages the file system.Updateris a high-integrity process that applies an update.
A software update is performed according to the following scenario:
- The
Downloaderdownloads an update image and saves it to a file by transferring the contents of the image to theFileSystem. A low integrity level is assigned to this file. - The
Verifierreceives the update image from theFileSystemby reading the high-integrity file, and verifies its digital signature. If the signature is correct, theVerifierqueries theFileSystemso that theFileSystemcreates a copy of the file containing the update image. A high integrity level is assigned to the new file. - The
Updaterreceives the update image from theFileSystemby reading the high-integrity file, and applies the update.
In this example, the Mic security model ensures that the high-integrity Updater process can read data only from a high-integrity update image. As a result, the update can be applied only after the digital signature of the update image is verified.
Mic security model object
To use the Mic security model, you need to create an object or objects of this model. You also need to assign a set of integrity levels for subjects and resources.
A Mic security model object has the following parameters:
configrefers to a set of integrity levels or configuration of a set of integrity levels:degreesrefers to a set of gradations for generating a set of integrity levels.categoriesrefers to a set of categories for generating a set of integrity levels.
Examples:
policy object mic : Mic {
config = ["LOW", "MEDIUM", "HIGH"]
}
policy object mic_po : Mic {
config =
{ degrees : ["low", "high"]
, categories : ["net", "log"]
}
}
A set of integrity levels is a partially ordered set that is linearly ordered or contains incomparable elements. The set {LOW, MEDIUM, HIGH} is linearly ordered because all of its elements are comparable to each other. Incomparable elements arise when a set of integrity levels is defined through a set of gradations and a set of categories. In this case, the set of integrity levels L is a Cartesian product of the Boolean set of categories C multiplied by the set of gradations D:
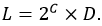
The degrees and categories parameters in this example define the following set:
{
{}/low, {}/high,
{net}/low, {net}/high,
{log}/low, {log}/high,
{net,log}/low, {net,log}/high
}
In this set, {} means an empty set.
The order relation between elements of the set of integrity levels L is defined as follows:
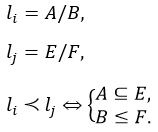
According to this order relation, the jth element exceeds the ith element if the subset of categories E includes the subset of categories A, and gradation F is greater than or equal to gradation A. Examples of comparing elements of the set of integrity levels L:
- The {net,log}/high element exceeds the {log}/low element because the "high" gradation is greater than the "low" gradation, and the subset of categories {net,log} includes the subset of categories {log}.
- The {net,log}/low element exceeds the {log}/low element because the levels of gradations for these elements are equal, and the subset of categories {net,log} includes the subset of categories {log}.
- The {net,log}/high element is the highest because it exceeds all other elements.
- The {}/low element is the lowest because all other elements exceed this element.
- The {net}/low and {log}/high elements are incomparable because the "high" gradation is greater than the "low" gradation but the subset of categories {log} does not include the subset of categories {net}.
- The {net,log}/low and {log}/high elements are incomparable because the "high" gradation is greater than the "low" gradation but the subset of categories {log} does not include the subset of categories {net,log}.
For subjects and resources that have incomparable integrity levels, the Mic security model provides conditions that are analogous to the conditions that the security model provides for subjects and resources that have comparable integrity levels.
By default, data streams between subjects that have incomparable integrity levels are prohibited. However, you have the option to allow such data streams if you can guarantee that the subjects receiving data will not be compromised. A resource consumer is prohibited from writing data to a resource and read data from a resource if the integrity level of the resource is incomparable to the integrity level of the resource consumer. You have the option to allow the resource consumer to read data from a resource if you can guarantee that the resource consumer will not be compromised.
A Mic security model object can be covered by a security audit. There are no audit conditions specific to the Mic security model.
It is necessary to create multiple objects of the Mic security model in the following cases:
- You need to configure a security audit differently for different objects of the Mic security model (for example, you can apply different audit profiles or different audit configurations of the same profile for different objects).
- You need to distinguish between calls of methods provided by different objects of the Mic security model (audit data includes the name of the security model method and the name of the object that provides this method, so you can verify that the method of a specific object was called).
- You need to use multiple variants of mandatory integrity control that may have different sets of integrity levels for subjects and resources, for example.
Mic security model create rule
create { source : <Sid>
, target : <Sid>
, container : <Sid | ()>
, driver : <Sid>
, level : <Level | ... | ()>
}
Assign the specified integrity level to the target resource in the following situation:
- The
sourceprocess initiates creation of thetargetresource. - The
targetresource is managed by thedriversubject, which is the resource provider or the KasperskyOS kernel. - The
containerresource is a container for thetargetresource (for example, a directory is a container for files and/or other directories).
If the container value is not defined (container : ()), the target resource is considered to be the root resource, which means that it has no container.
To define the integrity level, values of the Level type are used:
type Level = LevelFull | LevelNoCategory
type LevelFull =
{ degree : Text | ()
, categories : List<Text> | ()
}
type LevelNoCategory = Text
The rule returns the "granted" result if a specific integrity level was assigned to the target resource.
The rule returns the "denied" result in the following cases:
- The
levelvalue exceeds the integrity level of thesourceprocess,driversubject orcontainerresource. - The
levelvalue is incomparable to the integrity level of thesourceprocess,driversubject orcontainerresource. - An integrity level was not assigned to the
sourceprocess,driversubject, orcontainerresource. - The value of
source,target,containerordriveris outside of the permissible range.
Example:
/* A server of the updater.Realmserv class will be allowed to respond to
* queries of any client in the solution calling the resolve method
* of the realm.Reader endpoint if the resource whose creation is requested
* by the client will be assigned the LOW integrity level during response initiation.
* Otherwise a server of the updater.Realmserv class will be prohibited from responding to
* queries of any client calling the resolve method of the realm.Reader endpoint. */
response src=updater.Realmserv,
endpoint=realm.Reader {
match method=resolve {
mic.create { source : dst_sid
, target : message.handle.handle
, container : ()
, driver : src_sid
, level : "LOW"
}
}
}
Mic security model execute rule
execute <ExecuteImage | ExecuteLevel>
type ExecuteImage =
{ image : Sid
, target : Sid
, level : Level | ... | ()
, levelR : Level | ... | ()
}
type ExecuteLevel =
{ image : Sid | ()
, target : Sid
, level : Level | ...
, levelR : Level | ... | ()
}
This assigns the specified integrity level to the target subject and defines the minimum integrity level of subjects and resources from which this subject can receive data (levelR). The code of the target subject is in the image executable file.
If the level value is not defined (level : ()), the integrity level of the image executable file is assigned to the target subject. If the image value is not defined (image : ()), the level value must be defined.
If the levelR value is not defined (levelR : ()), the value of levelR is equal to level.
To define the integrity level and levelR, values of the Level type are used. For the definition of the Level type, see "Mic security model create rule".
The rule returns the "granted" result if it assigned the specified integrity level to the target subject and defined the minimum integrity level of subjects and resources from which this subject can receive data (levelR).
The rule returns the "denied" result in the following cases:
- The
levelvalue exceeds the integrity level of theimageexecutable file. - The
levelvalue is incomparable to the integrity level of theimageexecutable file. - The value of
levelRexceeds the value oflevel. - The
levelandlevelRvalues are incomparable. - An integrity level was not assigned to the
imageexecutable file. - The
imageortargetvalue is outside of the permissible range.
Example:
/* A process of the updater.Manager class will be allowed to start
* if, at startup initiation, this process will be assigned
* the integrity level LOW, and the minimum
* integrity level will be defined for the processes and resources from which this
* process can received data (LOW). Otherwise the startup of a process
* of the updater.Manager class will be denied. */
execute src=Einit, dst=updater.Manager, method=main {
mic.execute { target : dst_sid
, image : ()
, level : "LOW"
, levelR : "LOW"
}
}
Mic security model upgrade rule
upgrade { source : <Sid>
, target : <Sid>
, container : <Sid | ()>
, driver : <Sid>
, level : <Level | ...>
}
This elevates the previously assigned integrity level of the target resource to the specified level in the following situation:
- The
sourceprocess initiates elevation of the integrity level of thetargetresource. - The
targetresource is managed by thedriversubject, which is the resource provider or the KasperskyOS kernel. - The
containerresource is a container for thetargetresource (for example, a directory is a container for files and/or other directories).
If the container value is not defined (container : ()), the target resource is considered to be the root resource, which means that it has no container.
To define the integrity level, values of the Level type are used. For the definition of the Level type, see "Mic security model create rule".
The rule returns the "granted" result if it elevated the previously assigned integrity level of the target resource to the level value.
The rule returns the "denied" result in the following cases:
- The
levelvalue does not exceed the integrity level of thetargetresource. - The
levelvalue exceeds the integrity level of thesourceprocess,driversubject orcontainerresource. - The integrity level of the
targetresource exceeds the integrity level of thesourceprocess. - An integrity level was not assigned to the
sourceprocess,driversubject, orcontainerresource. - The value of
source,target,containerordriveris outside of the permissible range.
Mic security model call rule
call {source : <Sid>, target : <Sid>}
This verifies the permissibility of data streams from the target subject to the source subject.
It returns the "allowed" result in the following cases:
- The integrity level of the
sourcesubject does not exceed the integrity level of thetargetsubject. - The integrity level of the
sourcesubject exceeds the integrity level of thetargetsubject, but the minimum integrity level of subjects and resources from which thesourcesubject can receive data does not exceed the integrity level of thetargetsubject. - The integrity level of the
sourcesubject is incomparable to the integrity level of thetargetsubject, but the minimum integrity level of subjects and resources from which thesourcesubject can receive data does not exceed the integrity level of thetargetsubject.
It returns the "denied" result in the following cases:
- The integrity level of the
sourcesubject exceeds the integrity level of thetargetsubject, and the minimum integrity level of subjects and resources from which thesourcesubject can receive data exceeds the integrity level of thetargetsubject. - The integrity level of the
sourcesubject exceeds the integrity level of thetargetsubject, and the minimum integrity level of subjects and resources from which thesourcesubject can read data is incomparable to the integrity level of thetargetsubject. - The integrity level of the
sourcesubject is incomparable to the integrity level of thetargetsubject, and the minimum integrity level of subjects and resources from which thesourcesubject can receive data exceeds the integrity level of thetargetsubject. - The integrity level of the
sourcesubject is incomparable to the integrity level of thetargetsubject, and the minimum integrity level of subjects and resources from which thesourcesubject can receive data is incomparable to the integrity level of thetargetsubject. - An integrity level was not assigned to the
sourcesubject or to thetargetsubject. - The
sourceortargetvalue is outside of the permissible range.
Example:
/* Any client in the solution is allowed to query
* any server (kernel) if data streams from
* the server (kernel) to the client are permitted by the
* Mic security model. Otherwise any client in the solution
* is prohibited from querying any server (kernel). */
request {
mic.call { source : src_sid
, target : dst_sid
}
}
Mic security model invoke rule
invoke {source : <Sid>, target : <Sid>}
This verifies the permissibility of data streams from the source subject to the target subject.
It returns the "granted" result if the integrity level of the target subject does not exceed the integrity level of the source subject.
It returns the "denied" result in the following cases:
- The integrity level of the
targetsubject exceeds the integrity level of thesourcesubject. - The integrity level of the
targetsubject is incomparable to the integrity level of thesourcesubject. - An integrity level was not assigned to the
sourcesubject or to thetargetsubject. - The
sourceortargetvalue is outside of the permissible range.
Mic security model read rule
read {source : <Sid>, target : <Sid>}
This verifies that the source resource consumer is allowed to read data from the target resource.
It returns the "allowed" result in the following cases:
- The integrity level of the
sourceresource consumer does not exceed the integrity level of thetargetresource. - The integrity level of the
sourceresource consumer exceeds the integrity level of thetargetresource, but the minimum integrity level of subjects and resources from which thesourceresource consumer can receive data does not exceed the integrity level of thetargetresource. - The integrity level of the
sourceresource consumer is incomparable to the integrity level of thetargetresource, but the minimum integrity level of subjects and resources from which thesourceresource consumer can receive data does not exceed the integrity level of thetargetresource.
It returns the "denied" result in the following cases:
- The integrity level of the
sourceresource consumer exceeds the integrity level of thetargetresource, and the minimum integrity level of subjects and resources from which thesourceresource consumer can receive data exceeds the integrity level of thetargetresource. - The integrity level of the
sourceresource consumer exceeds the integrity level of thetargetresource, and the minimum integrity level of subjects and resources from which thesourceresource consumer can receive data is incomparable to the integrity level of thetargetresource. - The integrity level of the
sourceresource consumer is incomparable to the integrity level of thetargetresource, and the minimum integrity level of subjects and resources from which thesourceresource consumer can receive data exceeds the integrity level of thetargetresource. - The integrity level of the
sourceresource consumer is incomparable to the integrity level of thetargetresource, and the minimum integrity level of subjects and resources from which thesourceresource consumer can receive data is incomparable to the integrity level of thetargetresource. - An integrity level was not assigned to the
sourceresource consumer or to thetargetresource. - The
sourceortargetvalue is outside of the permissible range.
Example:
/* Any client in the solution is allowed to query a server of
* the updater.Realmserv class by calling the read method of the
* realm.Reader service if the Mic security model permits
* this client to read data from the resource needed by
* this client. Otherwise any client in the solution is prohibited from
* querying a server of the updater.Realmserv class by calling
* the read method of the realm.Reader endpoint. */
request dst=updater.Realmserv,
endpoint=realm.Reader {
match method=read {
mic.read { source : src_sid,
, target : message.handle.handle
}
}
}
Mic security model write rule
write {source : <Sid>, target : <Sid>}
This verifies that the source resource consumer is allowed to write data to the target resource.
It returns the "granted" result if the integrity level of the target resource does not exceed the integrity level of the source resource consumer.
It returns the "denied" result in the following cases:
- The integrity level of the
targetresource exceeds the integrity level of thesourceresource consumer. - The integrity level of the
targetresource is incomparable to the integrity level of thesourceresource consumer. - An integrity level was not assigned to the
sourceresource consumer or to thetargetresource. - The
sourceortargetvalue is outside of the permissible range.
Mic security model query_level expression
query_level {source : <Sid>}
It is intended to be used as an expression that verifies fulfillment of the conditions in the choice construct (for details on the choice construct, see "Binding methods of security models to security events"). It checks the integrity level of the source resource or subject. Depending on the results of this check, various options for security event handling can be performed.
It runs incorrectly in the following cases:
- An integrity level was not assigned to the subject or
sourceresource. - The
sourcevalue is outside of the permissible range.
When the expression runs incorrectly, the Kaspersky Security Module returns the "denied" decision.
Page topMethods of KasperskyOS core endpoints
From the perspective of the Kaspersky Security Module, the KasperskyOS kernel is a container of components that provide endpoints. The list of kernel components is provided in the Core.edl file located in the sysroot-*-kos/include/kl/core directory of the KasperskyOS SDK. This directory also contains the CDL and IDL files for the formal specification of the kernel.
Methods of core endpoints can be divided into secure methods and potentially dangerous methods. Potentially dangerous methods could be used by a cybercriminal in a compromised solution component to cause a denial of service, set up covert data transfer, or hijack an I/O device. Secure methods cannot be used for these purposes.
Access to methods of core endpoints must be restricted as much as possible by the solution security policy (according to the least privilege principle). For that, the following requirements must be fulfilled:
- Access to a secure method must be granted only to the solution components that require this method.
- Access to a potentially dangerous method must be granted only to the trusted solution components that require this method.
- Access to a potentially dangerous method must be granted to untrusted solution components that require this method only if the verifiable access conditions limit the possibilities of malicious use of this method, or if the impact from malicious use of this method is acceptable from a security perspective.
For example, an untrusted component may be allowed to use a limited set of I/O ports that do not allow this component to take control of I/O devices. In another example, covert data transfer between untrusted components may be acceptable from a security perspective.
Virtual memory endpoint
This endpoint is intended for managing virtual memory.
Information about methods of the endpoint is provided in the table below.
Methods of the vmm.VMM endpoint (kl.core.VMM interface)
Method |
Method purpose and parameters |
Potential danger of the method |
|---|---|---|
|
Purpose Allocates a virtual memory region (reserves and optionally maps it to physical memory). Parameters
|
Allows the following:
|
|
Purpose Maps the virtual memory region (or part of it) reserved by the Parameters
|
Lets you exhaust RAM. |
|
Purpose Cancels mapping of the virtual memory region to physical memory. Parameters
|
N/A |
|
Purpose Modifies the access rights to the virtual memory region. Parameters
|
N/A |
|
Purpose Frees up the virtual memory region. Parameters
|
N/A |
|
Purpose Lets you get information about a virtual memory page. Parameters
|
N/A |
|
Purpose Creates an MDL buffer. Parameters
|
Allows the following:
|
|
Purpose Creates an MDL buffer from physical memory that is mapped to the defined virtual memory region and maps the created MDL buffer to this region. Parameters
|
Allows the following:
|
|
Purpose Gets the size of the MDL buffer. Parameters
|
N/A |
|
Purpose Maps an MDL buffer to a virtual memory region. Parameters
|
Allows the following:
|
|
Purpose Creates an MDL buffer based on an existing one. The MDL buffer is created from the same regions of physical memory as the original buffer. Parameters
|
Allows the kernel memory to be used up by creating a multitude of objects within it. |
I/O endpoint
This endpoint is intended for working with I/O ports, MMIO, DMA, and interrupts.
Information about methods of the endpoint is provided in the table below.
Methods of the io.IO endpoint (kl.core.IO interface)
Method |
Method purpose and parameters |
Potential danger of the method |
|---|---|---|
|
Purpose Registers I/O ports. Parameters
|
Allows the following:
|
|
Purpose Registers an MMIO memory region. Parameters
|
Allows the kernel memory to be used up by creating a multitude of objects within it. |
|
Purpose Creates an DMA buffer. Parameters
|
Allows the following:
|
|
Purpose Registers an interrupt. Parameters
|
Allows the kernel memory to be used up by creating a multitude of objects within it. |
|
Purpose Maps an MMIO memory region to a virtual memory region. Parameters
|
Allows the following:
|
|
Purpose Opens access to I/O ports. Parameters
|
Allows the following:
|
|
Purpose Attaches an interrupt to the handle used by the interrupt handler. Parameters
|
Allows the following:
|
|
Purpose Attaches an interrupt to the handle used by the interrupt handler. Parameters
|
Allows the following:
|
|
Purpose Detaches an interrupt from the handle used by the interrupt handler. Parameters
|
N/A |
|
Purpose Resumes interrupt handling. Parameters
|
N/A |
|
Purpose Blocks interrupt handling. Parameters
|
Lets you block interrupt handling in another process. |
|
Purpose Modifies DMA parameters. Parameters
|
N/A |
|
Purpose Maps an DMA buffer to a virtual memory region. Parameters
|
Allows the following:
|
|
Purpose Lets you get information about a DMA buffer. Parameters
|
N/A |
|
Purpose Lets you get information about the physical memory that was used to create a DMA buffer. Parameters
|
N/A |
|
Purpose Opens access to a DMA buffer for a device. Parameters
|
Allows the kernel memory to be used up by creating a multitude of objects within it. |
Threads endpoint
This endpoint is intended for managing threads.
Information about methods of the endpoint is provided in the table below.
Methods of the thread.Thread endpoint (kl.core.Thread interface)
Method |
Method purpose and parameters |
Potential danger of the method |
|---|---|---|
|
Purpose Creates a thread. Parameters
|
Allows the following:
|
|
Purpose Blocks a thread. Parameters
|
Lets you lock a standard thread that has captured the synchronization entity expected by the real-time thread in whose context the interrupt is being handled. This could stop the handling of this interrupt by other processes. |
|
Purpose Resumes a thread. Parameters
|
N/A |
|
Purpose Terminates a thread. Parameters
|
N/A |
|
Purpose Terminates the current thread. Parameters
|
N/A |
|
Purpose Locks the current thread until the defined thread is terminated. Parameters
|
N/A |
|
Purpose Defines the priority of a thread. Parameters
|
Allows the priority of a thread to be elevated to reduce the CPU time available to all other threads, including from other processes. It is recommended to monitor thread priority. |
|
Purpose Allows access to the local memory of the current thread (TLS of the current thread). Parameters
|
N/A |
|
Purpose Defines the base address of the local memory of the current thread (TLS of the current thread). Parameters
|
N/A |
|
Purpose Locks the current thread for the specified duration. Parameters
|
N/A |
|
Purpose Lets you get information about a thread. Parameters
|
N/A |
|
Purpose Detaches the current thread from the interrupt handled in its context. Parameters
|
N/A |
|
Purpose Lets you get a thread affinity mask. Parameters
|
N/A |
|
Purpose Defines a thread affinity mask. Parameters
|
N/A |
|
Purpose Defines the thread scheduler class. Parameters
|
Allows the following:
|
|
Purpose Lets you get information about the thread scheduler class. Parameters
|
N/A |
Handles endpoint
This endpoint is intended for working with handles.
Information about methods of the endpoint is provided in the table below.
Methods of the handle.Handle endpoint (kl.core.Handle interface)
Method |
Method purpose and parameters |
Potential danger of the method |
|---|---|---|
|
Purpose Creates a handle based on an existing one. Parameters
|
Allows the kernel memory to be used up by creating a multitude of objects within it. |
|
Purpose Creates a handle for a user resource. Parameters
|
Allows the kernel memory to be used up by creating a multitude of objects within it. |
|
Purpose Deletes a handle. Parameters
|
N/A |
|
Purpose Creates and connects the client-, server-, and listener IPC handles. Parameters
|
Allows the kernel memory to be used up by creating a multitude of objects within it. |
|
Purpose Disconnects the client- and server IPC handles. Parameters
|
N/A |
|
Purpose Creates a handle and connects it to a security interface. Parameters
|
Allows a multitude of possible kernel process handle values to be used up. |
|
Purpose Disconnects a handle from a security interface. Parameters
|
N/A |
|
Purpose Allocates a unique ID value. This method is used for backward compatibility because handles are currently being used instead of unique IDs. Parameters
|
Allows a multitude of possible unique ID values to be used up. |
|
Purpose Frees the value of a unique ID. (This value must be freed so that it can be available for re-use.) This method is used for backward compatibility because handles are currently being used instead of unique IDs. Parameters
|
Allows a unique ID value used by another process to be freed. |
|
Purpose Lets you receive a security ID (SID) based on a handle. Parameters
|
N/A |
|
Purpose Deletes a handle and revokes its descendants. Parameters
|
N/A |
|
Purpose Revokes the handles that make up the inheritance subtree of the specified handle. Parameters
|
N/A |
|
Purpose Creates a resource transfer context object and configures a notification mechanism for monitoring the life cycle of this object. Parameters
|
Allows the kernel memory to be used up by creating a multitude of objects within it. |
Processes endpoint
This endpoint is intended for managing processes.
Information about methods of the endpoint is provided in the table below.
Methods of the task.Task endpoint (kl.core.Task interface)
Method |
Method purpose and parameters |
Potential danger of the method |
|---|---|---|
|
Purpose Creates a process. Parameters
|
Allows the following:
|
|
Purpose Loads a program image segment into process memory from the MDL buffer. Parameters
|
Allows code to be loaded into process memory for subsequent execution of that code. |
|
Purpose Defines a process entry point. Parameters
|
Creates conditions for executing code loaded into process memory. |
|
Purpose Loads the character table and string table from MDL buffers into process memory. MDL buffers contain a character table and string table from non-loadable segments of the ELF file. These tables are necessary for receiving stack backtrace data (information about call stacks). Parameters
|
N/A |
|
Purpose Loads the parameters of a process into its memory. Parameters
|
Allows the kernel memory to be used up by creating a multitude of objects within it. |
|
Purpose Frees the memory of the current process occupied by parameters that were loaded by the Parameters
|
N/A |
|
Purpose Starts a process. Parameters
|
Allows the following:
|
|
Purpose Terminates the current process. Parameters
|
N/A |
|
Purpose Terminates a process. Parameters
|
Allows another process to be terminated if its handle is available. (The handle permissions mask must allow termination of the process.) |
|
Purpose Lets you get information about a terminated process. Parameters
|
N/A |
|
Purpose Lets you receive the context of a thread that is part of a process that has been frozen due to an unhandled exception. When a process is frozen, execution of the process stops but its resources are not freed. Therefore, data on this process can be collected. Parameters
|
Lets you disrupt isolation of a process that has been frozen due to an unhandled exception. For example, the received thread context can contain the values of variables. |
|
Purpose Lets you get information about the virtual memory region belonging to a process that has been frozen due to an unhandled exception. When a process is frozen, execution of the process stops but its resources are not freed. Therefore, data on this process can be collected. Parameters
|
Lets you disrupt isolation of a process that has been frozen due to an unhandled exception. Process isolation is disrupted due to the opened access to the process memory region. |
|
Purpose Terminates a process that has been frozen due to an unhandled exception. When a process is frozen, execution of the process stops but its resources are not freed. Therefore, data on this process can be collected. A frozen process cannot be restarted. It can only be terminated. Parameters
|
Allows termination of a process that has been frozen due to an unhandled exception. This will not allow collection of data about this process for diagnostic purposes. |
|
Purpose Lets you get the name of the current process. Parameters
|
N/A |
|
Purpose Lets you get the name of the executable file that was used to start the current process. Parameters
|
N/A |
|
Purpose Lets you get the priority of the initial thread of a process. Parameters
|
N/A |
|
Purpose Defines the priority of the initial thread of a process. Parameters
|
Allows the priority of the initial thread of a process to be elevated to reduce the CPU time available to all other threads, including from other processes. It is recommended to monitor the priority of an initial thread. |
|
Purpose Lets you get information about existing processes. Parameters
|
Allows the kernel memory to be used up by creating a multitude of objects within it. |
|
Purpose Defines the scheduler class and priority of the initial thread of a process. Parameters
|
Allows the following:
|
|
Purpose Defines the initial vector in the random number generator for ASLR support. Affects the results from calling the Parameters
|
N/A |
Synchronization endpoint
This endpoint is intended for working with futexes.
Information about methods of the endpoint is provided in the table below.
Methods of the sync.Sync endpoint (kl.core.Sync interface)
Method |
Method purpose and parameters |
Potential danger of the method |
|---|---|---|
|
Purpose Locks execution of the current thread if the futex value is equal to the expected value. Parameters
|
N/A |
|
Purpose Resumes execution of threads that were blocked by a Parameters
|
N/A |
File system endpoints
These endpoints are intended for working with the ROMFS file system used by the KasperskyOS kernel.
Information about methods of endpoints is provided in the tables below.
Methods of the fs.FS endpoint (kl.core.FS interface)
Method |
Method purpose and parameters |
Potential danger of the method |
|---|---|---|
|
Purpose Opens a file. Parameters
|
Allows the kernel memory to be used up by creating a multitude of objects within it. |
|
Purpose Closes a file. Parameters
|
N/A |
|
Purpose Reads data from a file. Parameters
|
N/A |
|
Purpose Lets you get the size of a file. Parameters
|
N/A |
|
Purpose Lets you get the unique ID of a file. Parameters
|
N/A |
|
Purpose Lets you get the number of files in the file system. Parameters
|
N/A |
|
Purpose Lets you get the name and unique ID of a file based on the file index. Parameters
|
N/A |
|
Purpose Lets you get the size of the file system. Parameters
|
N/A |
Methods of the fs.FSUnsafe endpoint (kl.core.FSUnsafe interface)
Method |
Method purpose and parameters |
Potential danger of the method |
|---|---|---|
|
Purpose Changes the file system image. A different ROMFS image loaded into process memory will be used instead of the ROMFS image that was created during the solution build. Parameters
|
Allows the following:
|
Time endpoint
This endpoint is intended for setting the system time.
Information about methods of the endpoint is provided in the table below.
Methods of the time.Time endpoint (kl.core.Time interface)
Method |
Method purpose and parameters |
Potential danger of the method |
|---|---|---|
|
Purpose Sets the system time. Parameters
|
Allows the system time to be set. |
Hardware abstraction layer endpoint
This endpoint is intended for receiving the values of HAL parameters, working with privileged registers, clearing the processor cache, and diagnostic output.
Information about methods of the endpoint is provided in the table below.
Methods of the hal.HAL endpoint (kl.core.HAL interface)
Method |
Method purpose and parameters |
Potential danger of the method |
|---|---|---|
|
Purpose Lets you get the value of a HAL parameter. Parameters
|
Lets you get values of HAL parameters that could contain critical system information. |
|
Purpose Lets you get the value of a privileged register. Parameters
|
Lets you set up a data transfer channel with a process that has access to the It is recommended to monitor the name of a register. |
|
Purpose Sets the value of a privileged register. Parameters
|
Allows the following:
It is recommended to monitor the name of a register. |
|
Purpose Lets you get the value of a privileged register. Parameters
|
Lets you set up a data transfer channel with a process that has access to the It is recommended to monitor the name of the registers range and the register offset in this range. |
|
Purpose Sets the value of a privileged register. Parameters
|
Allows the following:
It is recommended to monitor the name of the registers range and the register offset in this range. |
|
Purpose Clears the processor cache. Parameters
|
Allows the processor cache to be cleared. |
|
Purpose Puts data into the diagnostic output that is written, for example, to a COM port or USB port (version 3.0 or later, with DbC support). Parameters
|
Lets you populate diagnostic output with fictitious (uninformative) data. |
XHCI controller management endpoint
This endpoint is intended for disabling and re-enabling debug mode for the XHCI controller (with DbC support) when it is restarted.
Information about methods of the endpoint is provided in the table below.
Methods of the xhcidbg.XHCIDBG endpoint (kl.core.XHCIDBG interface)
Method |
Method purpose and parameters |
Potential danger of the method |
|---|---|---|
|
Purpose Enables debug mode of the XHCI controller. Parameters
|
Lets you configure the XHCI controller to send diagnostic output through a USB port (version 3.0 or later). |
|
Purpose Disables debug mode of the XHCI controller. Parameters
|
Lets you configure the XHCI controller to not send diagnostic output through a USB port (version 3.0 or later). |
Audit endpoint
This endpoint is intended for reading messages from KasperskyOS kernel logs. There are two kernel logs: kss and core. The kss log contains security audit data. The core log contains diagnostic output. (Diagnostic output includes kernel output and the output of programs.)
Information about methods of the endpoint is provided in the table below.
Methods of the audit.Audit endpoint (kl.core.Audit interface)
Method |
Method purpose and parameters |
Potential danger of the method |
|---|---|---|
|
Purpose Opens the kernel log to read data from it. Parameters
|
N/A |
|
Purpose Closes the kernel log. Parameters
|
N/A |
|
Purpose Lets you receive a message from a kernel log. Parameters
|
Lets you extract messages from the kernel log so that these messages are not received by another process. |
Profiling endpoint
This endpoint is intended for profiling user code and kernel code, receiving information about coverage of kernel code and user code, and receiving values of performance counters.
Information about methods of the endpoint is provided in the table below.
Methods of the profiler.Profiler endpoint (kl.core.Profiler interface)
Method |
Method purpose and parameters |
Potential danger of the method |
|---|---|---|
|
Purpose Assigns user code profiling. Profiling generates statistics on the execution of user code in the context of the defined thread. These statistics show how many times the user code from different sections of the defined virtual address range was triggered during the profiling period. Parameters
|
Allows the kernel memory to be used up by creating a multitude of objects within it. |
|
Purpose Cancels user code profiling. Parameters
|
N/A |
|
Purpose Assigns kernel code profiling. Profiling results in statistics on kernel code execution. These statistics show how many times the kernel code was triggered from different sections of the memory address range of the process that called this method. The range of virtual addresses occupied by kernel code are identical for all processes. Kernel code execution statistics are gathered in the aggregate and not within the context of one process or thread. Parameters
|
N/A |
|
Purpose Cancels kernel code profiling. Parameters
|
N/A |
|
Purpose Starts kernel code profiling. Parameters
|
N/A |
|
Purpose Stops kernel code profiling. Parameters
|
N/A |
|
Purpose Lets you get data containing the kernel code execution statistics received during profiling. Parameters
|
N/A |
|
Purpose Lets you get information about kernel code coverage. Parameters
|
N/A |
|
Purpose Output of data on kernel code coverage in Parameters
|
N/A |
|
Purpose Output of data on code coverage in Parameters
|
N/A |
|
Purpose Lets you get the values of performance counters. Parameters
|
N/A |
I/O memory management endpoint
This endpoint is intended for managing the isolation of physical memory regions used by devices on a PCIe bus. (Isolation is provided by the IOMMU.)
Information about methods of the endpoint is provided in the table below.
Methods of the iommu.IOMMU endpoint (kl.core.IOMMU interface)
Method |
Method purpose and parameters |
Potential danger of the method |
|---|---|---|
|
Purpose Attaches a device on a PCIe bus to the IOMMU domain associated with the current process. Parameters
|
Lets you attach a device on a PCIe bus managed by another process to an IOMMU domain associated with the current process, which leads to failure of the device. It is recommended to monitor the address of a device on a PCIe bus. |
|
Purpose Detaches the device on a PCIe bus from the IOMMU domain associated with the current process. Parameters
|
N/A |
Connections endpoint
This endpoint is intended for dynamic creation of IPC channels.
Information about methods of the endpoint is provided in the table below.
Methods of the cm.CM endpoint (kl.core.CM interface)
Method |
Method purpose and parameters |
Potential danger of the method |
|---|---|---|
|
Purpose Requests to create an IPC channel with a server for use of the defined endpoint. Parameters
|
Lets you create a load on a server by sending a large number of requests to create an IPC channel. |
|
Purpose Checks for a client request to create an IPC channel for use of an endpoint. Parameters
|
N/A |
|
Purpose Rejects a client request to create an IPC channel for use of the defined endpoint. Parameters
|
N/A |
|
Purpose Accepts a client request to create an IPC channel for use of the defined endpoint. Parameters
|
N/A |
Power management endpoint
This endpoint is intended for changing the power management mode of a computer (for example, shutting down or restarting the computer), and for enabling and disabling processors (processor cores).
Information about methods of the endpoint is provided in the table below.
Methods of the pm.PM endpoint (kl.core.PM interface)
Method |
Method purpose and parameters |
Potential danger of the method |
|---|---|---|
|
Purpose Requests to change the power mode of a computer. Parameters
|
Allows the computer power mode to be changed. |
|
Purpose Requests to enable and/or disable processors. Parameters
|
Lets you disable and enable processors. |
|
Purpose Lets you get information regarding which processors are in the active state. Parameters
|
N/A |
Notifications endpoint
This endpoint is intended for working with notifications about events that occur with resources.
Information about methods of the endpoint is provided in the table below.
Methods of the notice.Notice endpoint (kl.core.Notice interface)
Method |
Method purpose and parameters |
Potential danger of the method |
|---|---|---|
|
Purpose Creates a notification receiver. Parameters
|
Allows the kernel memory to be used up by creating a multitude of objects within it. |
|
Purpose Adds a "resource–event mask" entry to the notification receiver so that it can receive notifications about events that occur with the defined resource and match the defined event mask. Parameters
|
Allows the kernel memory to be used up by creating a multitude of objects within it. |
|
Purpose Deletes notifications matching a "resource–event mask" entry with the defined ID from the notification receiver. Parameters
|
N/A |
|
Purpose Deletes notifications matching the defined resource from the notification receiver. Parameters
|
N/A |
|
Purpose Extracts notifications from the receiver. Parameters
|
N/A |
|
Purpose Deletes all "resource–event mask" entries from the defined notification receiver, resumes execution of all threads awaiting an event associated with the defined notification receiver, and (optionally) prohibits the addition of "resource–event mask" entries to the defined notification receiver. Parameters
|
N/A |
|
Purpose Signals that events from the defined event mask occurred with the defined user resource. Parameters
|
N/A |
Hypervisor endpoint
This endpoint is intended for working with a hypervisor.
Methods of the hypervisor.Hypervisor endpoint (kl.core.Hypervisor interface) are potentially dangerous. Access to these methods can be granted only to the specialized vmapp program.
Trusted Execution Environment endpoints
These endpoints are intended for transferring data between a Trusted Execution Environment (TEE) and a Rich Execution Environment (REE), and for obtaining access to the physical memory of the REE from the TEE.
Information about methods of endpoints is provided in the tables below.
Methods of the tee.TEE endpoint (kl.core.TEE interface)
Method |
Method purpose and parameters |
Potential danger of the method |
|---|---|---|
|
Purpose Sends and receives messages transferred between a TEE and a REE. This method is used in the TEE and in the REE. Parameters
|
Allows a process in a REE to receive a response from a TEE regarding a request from another process in the REE. |
|
Purpose Frees the values of unique IDs of messages transferred between a TEE and a REE. (These values must be freed so that they can become available for re-use.) This method is used in REE. Parameters
|
Lets you free the values used by other processes in a REE as unique IDs of messages transferred between a TEE and a REE. |
Methods of the tee.TEEVMM endpoint (kl.core.TEEVMM interface)
Method |
Method purpose and parameters |
Potential danger of the method |
|---|---|---|
|
Purpose Creates a blank MDL buffer so that physical memory from an REE can be subsequently added to it. This method is used in TEE. Parameters
|
Allows the kernel memory to be used up by creating a multitude of objects within it. |
|
Purpose Adds a REE physical memory region to the blank MDL buffer created by the This method is used in TEE. Parameters
|
Allows access to an arbitrary region of the physical memory of a REE from a TEE. |
IPC interrupt endpoint
This endpoint is intended for interrupting the Call() and Recv() locking system calls. (For example, this may be required to correctly terminate a process.)
Information about methods of the endpoint is provided in the table below.
Methods of the ipc.IPC endpoint (kl.core.IPC interface)
Method |
Method purpose and parameters |
Potential danger of the method |
|---|---|---|
|
Purpose Creates an IPC synchronization object. An IPC synchronization object is used to interrupt The handle of an IPC synchronization object cannot be transferred to another process because the necessary flag for this operation is not set in the permissions mask of this handle. Parameters
|
Allows the kernel memory to be used up by creating a multitude of objects within it. |
|
Purpose Switches the defined IPC synchronization object to a state in which the Parameters
|
N/A |
|
Purpose Switches the defined IPC synchronization object to a state in which the Parameters
|
N/A |
CPU frequency management endpoint
This endpoint is intended for changing the frequency of processors (processor cores).
Information about methods of the endpoint is provided in the table below.
Methods of the cpufreq.CpuFreq endpoint (kl.core.CpuFreq interface)
Method |
Method purpose and parameters |
Potential danger of the method |
|---|---|---|
|
Purpose Allows you to receive information about processor groups. Processor group information lists the existing processor groups while indicating the possible values of the performance parameter for each of them. This parameter is a combination of the matching frequency and voltage (Operating Performance Point, or OPP). The frequency is indicated in kiloherz (kHz) and the voltage is indicated in microvolts (µV). Parameters
|
N/A |
|
Purpose Lets you get the index of the current OPP for the defined processor group. Parameters
|
N/A |
|
Purpose Sets the defined OPP for the defined processor group. Parameters
|
Lets you change the frequency of a processor group. |