Contents
Architecture and basic concepts
This section explains the application architecture and basic concepts related to Kaspersky Security Center Cloud Console.
Architecture
This section provides a description of the components of Kaspersky Security Center Cloud Console and their interaction.
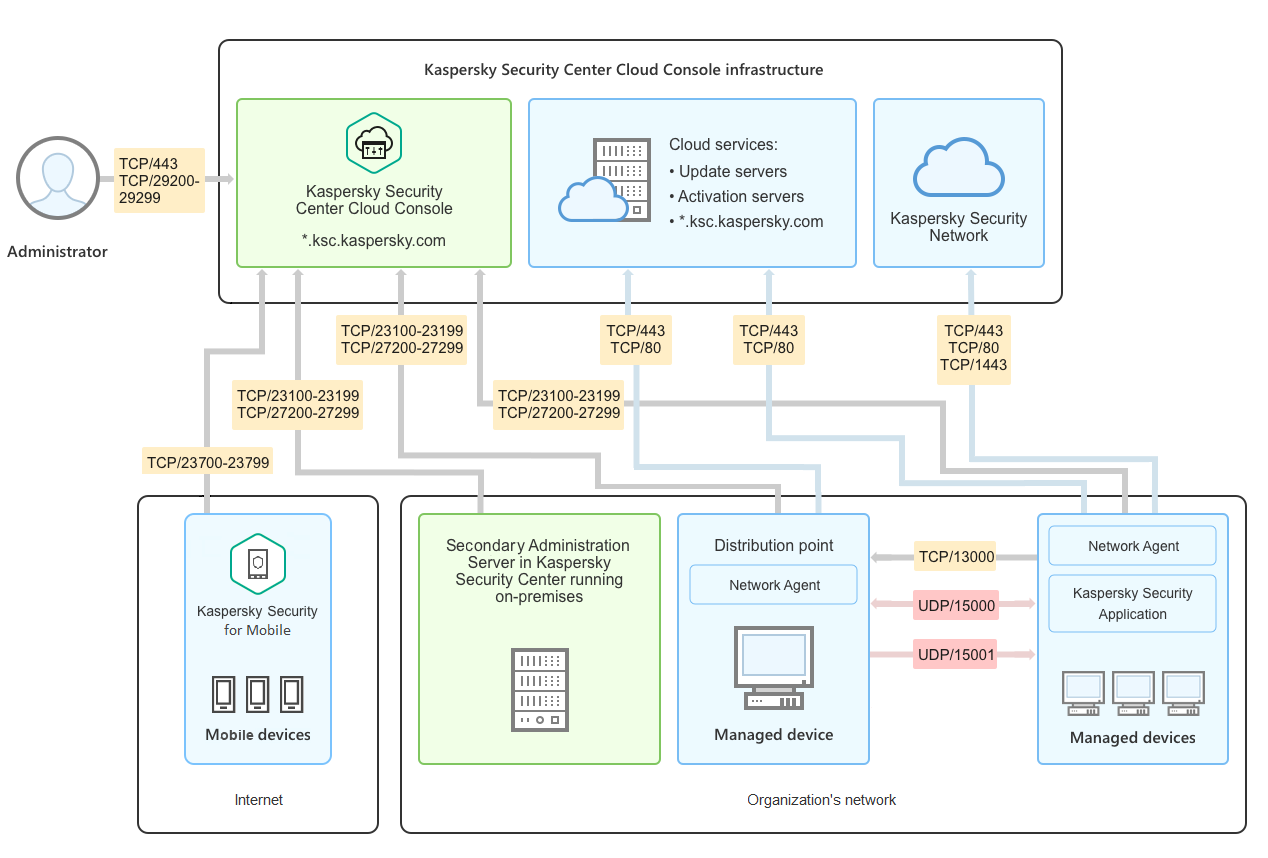
Kaspersky Security Center Cloud Console architecture
Kaspersky Security Center Cloud Console managed via the cloud-based console includes two main components: Kaspersky Security Center Cloud Console infrastructure and customer's infrastructure.
Kaspersky Security Center Cloud Console infrastructure consists of the following:
- Cloud-based Administration Console. Provides a web interface for creating and maintaining the protection system of a client organization's network that is managed by Kaspersky Security Center Cloud Console.
- Cloud services. Includes update servers and activation servers.
- Kaspersky Security Network (KSN). Servers that contain a Kaspersky database with continuously updated information about the reputation of files, web resources, and software. Kaspersky Security Network ensures faster responses by Kaspersky applications to threats, improves the performance of some protection components, and reduces the likelihood of false positives.
Customer's infrastructure may consist of the following:
- Distribution point. Computer that has Network Agent installed and is used for update distribution, network polling, remote installation of applications, getting information about computers in an administration group, and / or broadcasting domain. The administrator selects the appropriate devices and assigns them distribution points manually.
- Managed devices. Computers of customer's network protected through Kaspersky Security Center Cloud Console. Network Agent and a Kaspersky security application must be installed on each managed device.
- Secondary Administration Server running on-premises (optional). You can use an on-premises Administration Server to create a hierarchy of Administration Servers.
Ports used by Kaspersky Security Center Cloud Console
To use Kaspersky Security Center Cloud Console, which is part of the Kaspersky infrastructure, you must open the following ports on the client devices to allow the internet connection (see table below):
Ports that must be open on client devices to allow the internet connection
Port (or port range) |
Protocol |
Purpose of the port (or port range) |
|---|---|---|
23100-23199 |
TCP/TLS |
Receiving connections from Network Agents and secondary Administration Servers on Kaspersky Security Center Cloud Console Administration Server at *.ksc.kaspersky.com. The Kaspersky infrastructure can use any port within this range and any web address within this mask. The port and the web address can change from time to time. |
23700-23799 (only if you manage mobile devices) |
TCP/TLS |
Receiving connections from mobile devices. Connection to the Kaspersky Security Center Cloud Console Administration Server at *.ksc.kaspersky.com. The Kaspersky infrastructure can use any port within this range and any web address within this mask. The port and the web address can change from time to time. |
27200-27299 |
TCP/TLS |
Receiving connections for application activation from managed devices (except for mobile devices). Connection to the Kaspersky Security Center Cloud Console Administration Server at *.ksc.kaspersky.com. The Kaspersky infrastructure can use any port within this range and any web address within this mask. The port and the web address can change from time to time. |
29200-29299 |
TCP/TLS |
Tunneling connections to managed devices by using the klsctunnel utility through Kaspersky Security Center Cloud Console Administration Server at *.ksc.kaspersky.com. The Kaspersky infrastructure can use any port within this range and any web address within this mask. The port and the web address can change from time to time. |
443 |
HTTPS |
Connection to Kaspersky Security Center Cloud Console discovery service at *.ksc.kaspersky.com. The Kaspersky infrastructure can use any web address within this mask. |
1443 |
TCP |
Connection to Kaspersky Security Network |
80 |
TCP |
Connection is used to check validity of the Kaspersky Security Center certificates at *.digicert.com. The Kaspersky infrastructure can use any web address within this mask. |
The table below lists the ports that must be open on client devices where Network Agent is installed.
Ports that must be open on client devices
Port number |
Protocol |
Port purpose |
Scope |
|---|---|---|---|
15000
|
UDP |
Receiving data from connection gateways (if in use) |
Managing client devices |
15000 |
UDP broadcast |
Getting data about other Network Agents within the same broadcasting domain |
Delivering updates and installation packages |
15001 |
UDP |
Receiving multicast requests from a distribution point (if in use) |
Receiving updates and installation packages from a distribution point |
Please note that the klnagent process can also request free ports from the dynamic port range of an endpoint operating system. These ports are allocated to the klnagent process automatically by the operating system, so klnagent process can use some ports that are used by another software. If the klnagent process affects that software operations, change the port settings in this software, or change the default dynamic port range in your operating system to exclude the port used by the software affected.
Also take into account that recommendations on the compatibility of Kaspersky Security Center Cloud Console with third-party software are described for reference only and may not be applicable to new versions of third-party software. The described recommendations for configuring ports are based on the experiences of Technical Support and our best practices.
The table below lists the additional ports that must be open on client devices where Network Agent is installed as a distribution point.
Ports used by Network Agent functioning as distribution point
Port number |
Protocol |
Port purpose |
Scope |
|---|---|---|---|
13000 |
TCP/TLS |
Receiving connections from Network Agents |
Managing client devices and delivering updates and installation packages |
13111 |
TCP |
Receiving requests from managed devices to KSN proxy server |
KSN proxy server |
13295 |
TCP/TLS |
Sending push notifications to managed devices |
Distribution point used as a push server |
15111 |
UDP |
Receiving requests from managed devices to KSN proxy server |
KSN proxy server |
17111 |
HTTPS |
Receiving requests from managed devices to KSN proxy server |
KSN proxy server |
If you have one or more Administration Servers on your network and use them as secondary Administration Servers when the primary Administration Server is located in the Kaspersky infrastructure, please refer to the list of ports that are used by Kaspersky Security Center running on-premises. Use those ports for interaction between your secondary Administration Server (or secondary Administration Servers) and client devices.
Basic concepts
This section explains basic concepts related to Kaspersky Security Center Cloud Console.
Network Agent
Interaction between the Administration Server and devices is performed by the Network Agent component of Kaspersky Security Center Cloud Console. Network Agent must be installed on all devices on which Kaspersky Security Center Cloud Console is used to manage Kaspersky applications.
Network Agent is installed on a device as a service with the following set of attributes:
- With the name "Kaspersky Security Center Network Agent"
- Set to automatically start when the operating system starts
- Using the LocalSystem account
A device that has Network Agent installed is called a managed device or device. You can install Network Agent on a Windows, Linux, or Mac device.
The name of the process that Network Agent starts is klnagent.exe.
Network Agent synchronizes the managed device with the Administration Server. Kaspersky Security Center Cloud Console automatically synchronizes the Administration Server with the managed devices several times per hour. The Administration Server sets the synchronization interval (also referred to as the heartbeat) depending on the number of managed devices.
Administration groups
An administration group (hereinafter also referred to as group) is a logical set of managed devices combined on the basis of a specific trait for the purpose of managing the grouped devices as a single unit within Kaspersky Security Center Cloud Console.
All managed devices within an administration group are configured to do the following:
- Use the same application settings (which you can specify in group policies).
- Use a common operating mode for all applications through the creation of group tasks with specified settings. Examples of group tasks include creating and installing a common installation package, updating the application databases and modules, scanning the device on demand, and enabling real-time protection.
A managed device can belong to only one administration group.
You can create hierarchies that have any degree of nesting for Administration Servers and groups. A single hierarchy level can include secondary and virtual Administration Servers, groups, and managed devices. You can move devices from one group to another without physically moving them. For example, if a worker's position in the enterprise changes from that of accountant to developer, you can move this worker's computer from the Accountants administration group to the Developers administration group. Thereafter, the computer will automatically receive the application settings required for developers.
Hierarchy of Administration Servers
Administration Servers can be arranged in a "primary/secondary" hierarchy. Each Administration Server can have several secondary Administration Servers on different nesting levels of the hierarchy. The nesting level for secondary Administration Servers is unrestricted. The administration groups of the primary Administration Server will then include the client devices of all secondary Administration Servers.
Kaspersky Security Center Cloud Console Administration Server can only act as a primary Administration Server and can have as secondary servers only Administration Servers running on-premises.
When migrating from the Administration Server that runs on-premises to the Kaspersky Security Center Cloud Console Administration Server, you can arrange the Administration Servers in a hierarchy. Then, to mitigate the migration, you can shift only part of your managed devices to the management of the Kaspersky Security Center Cloud Console Administration Server. The rest of the managed devices remain under the management of the on-premises Administration Server. This enables you to test management features of Kaspersky Security Center Cloud Console on a limited number of managed devices. At the same time, you can configure policies, tasks, reports and other objects to test management and monitoring of your entire network. This lets you switch back to the objects configured on the on-premises Administration Server if necessary.
Each device included in the hierarchy of administration groups can be connected to one Administration Server only. You must independently monitor the connection of devices to Administration Servers. Use the feature for device search in administration groups of different Administration Servers based on network attributes.
Virtual Administration Server
Virtual Administration Server (also referred to as virtual Server) is a component of Kaspersky Security Center Cloud Console intended for managing anti-virus protection of the network of a client organization. Each virtual Administration Server can have its own structure of administration groups and its own means of management and monitoring, such as policies, tasks, reports, and events. The functional scope of virtual Administration Servers can be used by organizations with complicated workflows.
Virtual Administration Server has the following restrictions:
- Virtual Administration Servers are supported only in the commercial mode of Kaspersky Security Center Cloud Console.
- Virtual Administration Server does not support creation of secondary Administration Servers (including virtual Servers).
- You cannot migrate virtual Administration Servers from Kaspersky Security Center to Kaspersky Security Center Cloud Console.
- Virtual Administration Servers cannot be managed by dedicated administrators. By default, the administrator that manages the primary Administration Server also manages all of the virtual Administration Servers.
- Users created on a virtual Server cannot be assigned a role on the Administration Server.
- In the virtual Administration Server properties window, the number of sections is limited.
Distribution point
A distribution point is a device with Network Agent installed that is used for update distribution, remote installation of applications, and retrieval of information about networked devices.
The features and use cases of Network Agent installed on a device used as a distribution point vary depending on the operating system.
A distribution point can perform the following functions:
- Distribute updates and installation packages to client devices within the group (including distribution through multicasting using UDP). Updates can be received from Kaspersky update servers through an update task created for the distribution point.
Distribution point devices running macOS cannot download updates from Kaspersky update servers.
If one or more devices running macOS are within the scope of the Download updates to the repositories of distribution points task, the task completes with the Failed status, even if it has successfully completed on all Windows devices.
- Distribute policies and group tasks through multicasting using UDP.
- Act as a gateway for connection to the Administration Server for managed devices since a direct connection cannot be established in the cloud infrastructure.
- Poll the network to detect new devices and update information about existing ones.
- Perform remote installation of third-party software and Kaspersky applications through Microsoft Windows tools, including installation on client devices without Network Agent.
This feature enables you to remotely transfer Network Agent installation packages to client devices located on networks to which the Administration Server has no direct access.
- Act as a proxy server participating in the Kaspersky Security Network.
This feature is not supported by distribution point devices running Linux or macOS.
You can enable KSN proxy server on the distribution point side to make the device act as a KSN proxy server. In this case, the KSN proxy service (ksnproxy) is run on the device.
Files are transmitted from the Administration Server to a distribution point over HTTP or, if SSL connection is enabled, over HTTPS. Using HTTP or HTTPS results in a higher level of performance, compared to SOAP, through reducing traffic.
Devices with Network Agent installed must be assigned distribution points manually according to administration groups. The full list of distribution points for specified administration groups is displayed in the report about the list of distribution points.
The scope of a distribution point is the administration group to which it has been assigned by the administrator, as well as its subgroups of all levels of embedding. However, the device acting as the distribution point may not be included in the administration group to which it has been assigned. If multiple distribution points have been assigned in the hierarchy of administration groups, Network Agent on the managed device connects to the nearest distribution point in the hierarchy.
A network location can also be the scope of distribution points. The network location is used for manual creation of a set of devices to which the distribution point will distribute updates. Network location can be determined only for devices running a Windows operating system.
Kaspersky Security Center Cloud Console assigns each Network Agent a unique IP multicast address that differs from every other address. This enables you to avoid network overload that might occur due to IP overlaps.
If two or more distribution points are assigned to a single network area or to a single administration group, one of them becomes the active distribution point, and the rest become standby distribution points. The active distribution point downloads updates and installation packages directly from the Administration Server, while standby distribution points receive updates from the active distribution point only. In this case, files are downloaded once from the Administration Server and then are distributed among distribution points. If the active distribution point becomes unavailable for any reason, one of the standby distribution points becomes active. The Administration Server automatically assigns a distribution point to act as standby.
The distribution point status (Active/Standby) is displayed with a check box in the klnagchk report.
A distribution point requires at least 4 GB of free disk space. If the free disk space of the distribution point is less than 2 GB, Kaspersky Security Center Cloud Console creates a security issue with the Warning importance level. The security issue will be published in the device properties, in the Security issues section.
Running remote installation tasks on a device assigned as distribution point requires additional free disk space. The volume of free disk space must exceed the total size of all installation packages to be installed.
Running any updating (patching) tasks and vulnerability fix tasks on a device assigned as distribution point requires additional free disk space. The volume of free disk space must be at least twice the total size of all patches to be installed.
Devices functioning as distribution points must be protected, including physical protection, against any unauthorized access.
Management web plug-in
A special component—the management web plug-in—is used for remote administration of Kaspersky software by means of Kaspersky Security Center Cloud Console. Hereinafter, a management web plug-in is also referred to as a management plug-in. A management plug-in is an interface between Kaspersky Security Center Cloud Console and a specific Kaspersky application. With a management plug-in, you can configure tasks and policies for the application.
The management plug-in provides the following:
- Interface for creating and editing application tasks and settings
- Interface for creating and editing policies and policy profiles for remote and centralized configuration of Kaspersky applications and devices
- Transmission of events generated by the application
- Kaspersky Security Center Cloud Console functions for displaying operational data and events of the application, and statistics relayed from client devices
Policies
A policy is a set of Kaspersky application settings that are applied to an administration group and its subgroups. You can install several Kaspersky applications on the devices of an administration group. Kaspersky Security Center Cloud Console provides a single policy for each Kaspersky application in an administration group. A policy has one of the following statuses (see the table below):
The status of the policy
Status |
Description |
|---|---|
Active |
The current policy that is applied to the device. Only one policy may be active for a Kaspersky application in each administration group. Devices apply the settings values of an active policy for a Kaspersky application. |
Inactive |
A policy that is not currently applied to a device. |
Out-of-office |
If this option is selected, the policy becomes active when the device leaves the corporate network. |
Policies function according to the following rules:
- Multiple policies with different values can be configured for a single application.
- Only one policy can be active for the current application.
- You can activate an inactive policy when a specific event occurs. For example, you can enforce stricter anti-virus protection settings during virus outbreaks.
- A policy can have child policies.
Generally, you can use policies as preparations for emergency situations, such as a virus attack. For example, if there is an attack via flash drives, you can activate a policy that blocks access to flash drives. In this case, the current active policy automatically becomes inactive.
In order to prevent maintaining multiple policies, for example, when different occasions assume changing of several settings only, you may use policy profiles.
A policy profile is a named subset of policy settings values that replaces the settings values of a policy. A policy profile affects the effective settings formation on a managed device. Effective settings are a set of policy settings, policy profile settings, and local application settings that are currently applied for the device.
Policy profiles function according to the following rules:
- A policy profile takes an effect when a specific activation condition occurs.
- Policy profiles contain values of settings that differ from the policy settings.
- Activation of a policy profile changes the effective settings of the managed device.
- A policy can include a maximum of 100 policy profiles.
Policy profiles
Sometimes it may be necessary to create several instances of a single policy for different administration groups; you might also want to modify the settings of those policies centrally. These instances might differ by only one or two settings. For example, all the accountants in an enterprise work under the same policy—but senior accountants are allowed to use flash drives, while junior accountants are not. In this case, applying policies to devices only through the hierarchy of administration groups can be inconvenient.
To help you avoid creating several instances of a single policy, Kaspersky Security Center Cloud Console enables you to create policy profiles. Policy profiles are necessary if you want devices within a single administration group to run under different policy settings.
A policy profile is a named subset of policy settings. This subset is distributed on target devices together with the policy, supplementing it under a specific condition called the profile activation condition. Profiles only contain settings that differ from the "basic" policy, which is active on the managed device. Activation of a profile modifies the settings of the "basic" policy that were initially active on the device. The modified settings take values that have been specified in the profile.
How local application settings relate to policies
You can use policies to set identical values of the application settings for all devices in a group.
The values of the settings that a policy specifies can be redefined for individual devices in a group by using local application settings. You can set only the values of settings that the policy allows to be modified, that is, the unlocked settings.
The value of a setting that the application uses on a client device is defined by the lock position ( ) for that setting in the policy:
) for that setting in the policy:
- If a setting modification is locked, the same value (defined in the policy) is used on all client devices.
- If a setting modification is unlocked, the application uses a local setting value on each client device instead of the value specified in the policy. The setting can then be changed in the local application settings.
This means that, when a task is run on a client device, the application applies settings that have been defined in two different ways:
- By task settings and local application settings, if the setting is not locked against changes in the policy.
- By the group policy, if the setting is locked against changes.
Local application settings are changed after the policy is first applied in accordance with the policy settings.