Contents
- Security
- Scanning the computer
- How to run a Quick Scan
- How to run a Full Scan
- How to run a Custom Scan
- How to run a removable drive scan
- How to run a Context Menu File or Folder Scan
- How to enable or disable a background scan
- How to create a scan schedule
- How to search for vulnerabilities in applications installed on your computer
- How to exclude a file, folder, or threat type from scanning
- Scanning files in OneDrive cloud storage
- Updating anti-virus databases and application modules
- Intrusion Prevention
- Weak Settings Scan
- Network Monitor
- Smart Home Monitor
- About the Smart Home Monitor component
- How to enable or disable Smart Home Monitor
- How to view devices on my network
- How to deny network access for a device
- How to delete a network with no connections from the list
- How to disable notifications when devices connect to my network
- How to send feedback about Smart Home Monitor
- Pre-Kaspersky virus removal
- How to restore a deleted or disinfected file
- Protecting email
- Participating in Kaspersky Security Network
- Protection using hardware virtualization
- Protection using Antimalware Scan Interface (AMSI)
- Remote management of computer protection
- Scanning the computer
Security
Today's hackers are getting smarter in their target to break into your devices. New ransomware, phishing and other malware types call out for new cybersecurity solutions to get you a step ahead the growing threats. We created the new Kaspersky application to help you stay on top of today's threats. Find out what you can do to feel secured.
Scanning the computer
During scanning, the application searches for infected files and malware. There are several types of scans that vary in their search duration and scope.
- Full Scan. Scans all areas of the computer. This scan requires a lot of time to complete.
- Quick Scan. Scans objects that are loaded when the operating system starts as well as system memory and boot files. This scan does not require a lot of time to complete.
- Selective Scan. Scans the selected file or folder.
- Removable drives scan. Scan of removable drives, such as hard drives and USB sticks connected to the computer.
- Instant File Scan. This option scans files from the context menu.
- Background Scan. Scan of system memory, the system partition, boot sectors, and startup objects, as well as rootkits search.
- Application Vulnerability Scan. Scan the computer for vulnerabilities in applications that malware can exploit to infect your system.
After you install the application, we recommend that you perform a full scan of your computer.
How to run a Quick Scan
During a quick scan, the application scans the following objects by default:
- Objects loaded at the startup of the operating system;
- System memory
- Disk boot sectors.
To run a Quick Scan:
- Open the main window of the application and perform the following actions:
- Go to Home section, and click the Quick Scan button.
- Go to the Security section.
- In the Scan block, click the Choose scan button.
- This opens the Scan window.
- In the Scan window select the Quick Scan section.
- In the Quick Scan section, click the Run scan button.
The application starts a quick scan of your computer.
How to run a Full Scan
During a full scan, the application scans the following objects by default:
- System memory
- Objects loaded on operating system startup;
- System backup storage;
- Hard drives and removable drives.
We recommend running a full scan immediately after installing the application to your computer.
To run a Full Scan:
- Open the main window of the application and go to the Security section.
- In the Scan block, click the Choose scan button.
This opens the Scan window.
- In the Scan window select the Full Scan section.
- In the drop-down list next to the Run scan button, select the action to perform when the scan is complete.
- Click Run scan.
The application starts a full scan of your computer.
How to run a Custom Scan
A Selective Scan lets you scan a file, folder, or drive for viruses and other threats.
To run a Custom Scan:
- Open the main application window.
- Go to the Security section.
- In the Scan block, click the Choose scan button.
This opens the Scan window.
- In the Scan window select the Selective Scan section.
- Click the Select button and specify an object in the file or folder selection window that opens.
- Click Run scan.
How to run a removable drive scan
Removable drives that you connect to the computer may contain viruses or other applications that present a threat. The Kaspersky application scans removable drives to prevent your computer from becoming infected. You can configure a removable drive scan to be started manually or automatically when a removable drive is connected to the computer. Automatic scanning of removable drives is enabled by default.
To run a removable drive scan manually:
- Open the main application window.
- Go to the Security section.
- In the Scan block, click the Choose scan button.
This opens the Scan window.
- In the Scan window select the Removable Drive Scan section.
- In the drop-down list, select the drive letter of the external device and click on the Run scan button.
The application will start scanning the connected device.
How to run a Context Menu File or Folder Scan
To run a Context Menu File or Folder Scan:
- Right-click on the file or folder that needs to be scanned.
- In the context menu that opens, select Scan for viruses.
The application will start scanning the selected file or folder.
In Microsoft Windows 11, you must expand the context menu of an object to see the application commands.
How to enable or disable a background scan
A Background scan is an automatic scan mode that does not display notifications. This scan requires fewer computer resources than other types of scans (for example, Full Scan). When in this mode, the application scans the system memory, system volumes, boot sectors and startup objects, and searches for rootkits.
A background scan is started in the following cases:
- After the databases and application modules are updated
- 30 minutes after application launch
- Every six hours.
- If the computer remains idle for five or more minutes (after the screen saver is started).
A background scan is interrupted when any of the following conditions is met:
- The computer becomes active again.
- The computer (laptop) switches to battery mode.
If a background scan has not been performed for over ten days, the scan is not stopped. When running a background scan, the application does not scan files whose contents are located in OneDrive cloud storage.
To enable or disable a background scan:
- Open the main application window.
- Go to the Security section.
- In the Scan block, click the Choose scan button.
This opens the Scan window.
- Click the
 icon in the Background scan block.
icon in the Background scan block.This opens the Background scan settings window.
- In the Background scan settings window, switch the toggle to On or Off.
How to create a scan schedule
To create a scan schedule:
- Open the main application window.
- Go to the Security section.
- In the Scan block, click the Choose scan button.
This opens the Scan window.
- In the Scan window, select the type of scan and click the
 icon.
icon. - In the opened window, click the Scan schedule link to proceed to the Scan schedule window.
- In the Scan schedule window, in the Run scan list, select a period, such as Every day, and specify the time to start the scan.
A scan schedule cannot be created for the Scan from Context Menu or Background Scan.
How to search for vulnerabilities in applications installed on your computer
Applications installed on your computer may have vulnerabilities that can be exploited by malware. Scanning your computer will help find these vulnerabilities and prevent infection of your computer.
To run the Application Vulnerability Scan:
- Open the main application window.
- Go to the Security section.
- In the Scan block, click the Choose scan button.
This opens the Scan window.
- In the Scan window select the Application Vulnerability Scan section.
- Click Run scan.
The application starts scanning your computer for vulnerabilities in applications.
How to exclude a file, folder, or threat type from scanning
To exclude a file, folder, or threat type from scanning:
- Open the main application window.
- Click
 in the lower part of the main window.
in the lower part of the main window.This opens the Settings window.
- Go to Security settings → Threats and exclusions.
- Click the Manage exclusions link to open the Exclusions window.
- Click Add.
- Add an exclusion in one of the following ways:
- Click Browse and select the folder or file that you want to exclude from scanning. Click Select.
- In the File or folder field, enter the full name or mask of the file or folder.
- In the Object field, enter the full name or mask of the threat type in accordance with the Kaspersky classification of detected object.
- If you fill in both fields, File or folder and Object, the specified file or folder is not scanned for the specified threat type.
- In the File hash field, enter the hash if you want files to be excluded from scanning by their hashes.
- Clear the check boxes for protection components that the exclusion rule must not apply to. Enter a comment if you like.
- Select the Active status for the rule and click Add.
Specified objects are excluded from scanning.
Additional information about settings in the Threats and Exclusions window
Scanning files in OneDrive cloud storage
In Windows 10 RS3 or later, the application does not scan files in OneDrive cloud storage. If the application detects such files during a scan, it shows a notification stating that the files in cloud storage were not scanned.
The following components do not scan files in OneDrive cloud storage:
- Full Scan
- Selective Scan
- Quick Scan
- Background Scan.
The report on the operation of the application contains a list of files in OneDrive cloud storage that were skipped during scan.
Files downloaded from OneDrive cloud storage to a local computer are scanned by real-time protection components. If a file scan was postponed and the file has been uploaded back to OneDrive cloud storage before the scan is started, this file may be skipped during a scan.
When running applications and scripts, the Intrusion Prevention and System Watcher components download applications from the OneDrive cloud storage to the local computer to scan.
In order to make sure that OneDrive files are displayed in Explorer, turn on the Files on demand in the OneDrive client application feature. If you are connected to the Internet, you can use them just like any other files on your computer.
Page topUpdating anti-virus databases and application modules
This section contains information about database and application module updates.
About updating databases and application modules
The installation package of the application includes databases and application modules. Using these databases:
- The application detects the majority of threats using Kaspersky Security Network, which requires an Internet connection.
- The application detects adware, auto dialers, and other legitimate software that can be used by intruders to damage your computer or personal data.
To get full protection, we recommend updating the anti-virus databases and application modules as soon as the application has been installed.
Databases and application modules are updated in stages:
- The application starts updating databases and application modules according to the specified settings: automatically, on schedule, or on demand. The application contacts an update source that stores a anti-virus databases and application modules update package.
- The application compares the existing databases with the databases available at the update source. If the databases are different, the application downloads the missing parts of the databases.
The application then uses the updated databases and application modules to scan the computer for viruses and other threats.
Update sources
You can use the following update sources:
- Kaspersky update servers
- HTTP or FTP server
- Network folder
Special considerations involved in updating anti-virus databases and application modules
Updates of anti-virus databases and application modules are subject to the following restrictions and specifics:
- Anti-virus databases are considered out of date after one day and extremely out of date after seven days.
- To download an update package from Kaspersky servers, an Internet connection is required.
- Updates of anti-virus databases and application modules are unavailable in the following cases:
- The subscription has expired, and the grace period or limited functionality mode is not available.
- A metered mobile Internet connection is used. This limitation applies on computers running under Microsoft Windows 8 or more recent versions of this operating system if automatic updates or scheduled updates are enabled and a traffic limit has been set for a metered mobile connection. If you want the application to update anti-virus databases and application modules in this case, clear the Limit traffic on metered connections check box in Settings → Security settings → Advanced settings → Network settings.
- The application is used under subscription from a service provider, and you have suspended your subscription on the website of the service provider.
Installing an update package
When an update package (patch) is received, the application installs it automatically. To complete the installation of an update package, you must restart the computer. Until the computer is restarted, the application icon in the notification area is red, and the application Notification Center window displays a prompt to restart the computer.
How to start an update of databases and application modules
By default, databases and application modules are updated automatically. You do not need to take any action. If automatic updates are disabled, you can update application databases and modules manually.
To start an update of databases and application modules:
- Open the main application window.
- Go to the Security section.
- In the Anti-Virus Database Update block, click the Update button.
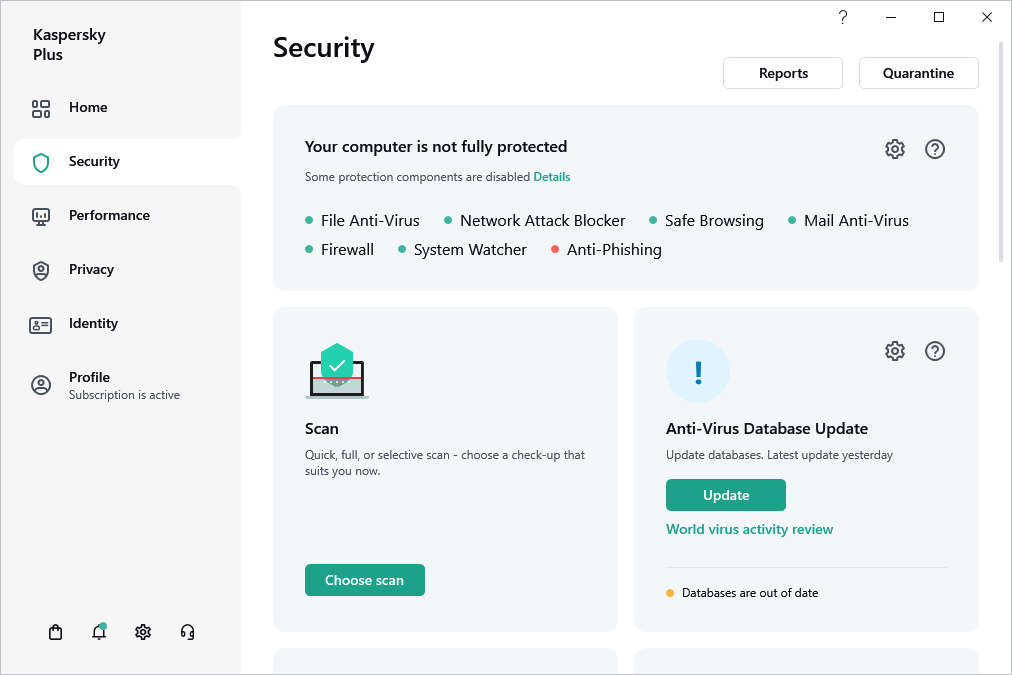
Anti-Virus Database Update
Intrusion Prevention
The Kaspersky application helps to minimize the risk associated with using unknown applications (such as the risk of infection with viruses and other malware).
The Kaspersky application includes components and tools that allow checking an application's reputation and controlling its activities on your computer.
About Intrusion Prevention
Available only in Kaspersky Standard, Kaspersky Plus, and Kaspersky Premium.
The Intrusion Prevention component prevents applications from performing actions that may be dangerous for the operating system, and controls access to operating system resources (including file resources located on remote computers) and your personal data.
Intrusion Prevention tracks actions performed in the operating system by applications installed on the computer and regulates them based on rules. These rules restrict suspicious activity of applications, including access by applications to protected resources, such as files and folders, registry keys, and network addresses.
On 64-bit operating systems, applications' rights for the following actions cannot be configured:
- Direct access to physical memory
- Managing printer driver
- Service creation
- Service reading
- Service editing
- Service reconfiguration
- Service management
- Service start
- Service removal
- Access to internal browser data
- Access to critical objects of the operating system
- Access to password storage
- Setting debug privileges
- Use of program interfaces of the operating system
- Use of program interfaces of the operating system (DNS)
- Use of program interfaces of other applications
- Change system modules (KnownDlls)
- Start drivers
On 64-bit Microsoft Windows 8 and Microsoft Windows 10, applications' rights for the following actions cannot be configured:
- Sending windows messages to other processes
- Suspicious operations
- Installation of keyloggers
- Interception of inbound stream events
- Making of screenshots
Applications' network activity is controlled by the Firewall component.
When an application is started on the computer for the first time, Intrusion Prevention checks the safety of the application and assigns it to a group (Trusted, Untrusted, High Restricted, or Low Restricted). The group defines the rules that Kaspersky applies for controlling the activity of the application.
The Kaspersky application assigns applications to trust groups (Trusted, Untrusted, High Restricted, or Low Restricted) only if Intrusion Prevention or Firewall is enabled, and also when both these components are enabled. If both these components are disabled, the functionality that assigns applications to trust groups does not work.
You can edit application control rules manually.
The rules you create for applications are inherited by child applications. For example, if you deny all network activity for cmd.exe, that activity will also be denied for notepad.exe when it is started using cmd.exe. When an application is not a child of the application it runs from, rules are not inherited.
Page topHow to change Intrusion Prevention settings
Available only in Kaspersky Standard, Kaspersky Plus, and Kaspersky Premium.
To change Intrusion Prevention settings:
- Open the main application window.
- Click
 in the lower part of the main window.
in the lower part of the main window.This opens the Settings window.
- Select the Security settings section.
- Select the Intrusion Prevention component.
- In the Intrusion Prevention settings window, click the Manage applications link to open the Manage applications window.
- Select the application you need in the list and double-click its name to open the Application rules window.
- To configure the rules for access by an application to operating system resources:
- On the Files and system registry tab, select the relevant resource category.
- Click the icon in the column with an available action for the resource (Read, Write, Delete, or Create) to open the menu. In the menu, select the relevant item (Inherit, Allow, Ask user, or Deny).
- To configure the rights of an application to perform various actions in the operating system:
- On the Rights tab, select the relevant category of rights.
- In the Action column, click the icon to open the menu and select the relevant item (Inherit, Allow,Ask user, or Deny).
- To configure the rights of an application to perform various actions on the network:
- On the Network rules tab, click the Add button.
This opens the Network rule window.
- In the window that opens, specify the required rule settings and click Save.
- Assign a priority to the new rule. To do so, select the rule and move it up or down the list.
- On the Network rules tab, click the Add button.
- To exclude certain application actions from the scan, on the Exclusions tab, select the check boxes for actions that you do not want to be controlled.
- Click Save.
All exclusions created in the Intrusion Prevention rules are accessible in the Kaspersky application settings window, in the Threats and exclusions section.
Intrusion Prevention monitors and restricts the actions of the application in accordance with the specified settings.
Checking application reputation
Kaspersky allows you to verify the reputation of applications with users all over the world. The reputation of an application comprises the following criteria:
- Name of the vendor
- Information about the (if the application is digitally signed)
- Information about the group to which the application has been assigned by Intrusion Prevention or most users of Kaspersky Security Network;
- Number of users of Kaspersky Security Network who use the application (available if the application has been included in the Trusted group in the Kaspersky Security Network database);
- Time at which the application become known to Kaspersky Security Network;
- Countries in which the application is the most widespread.
Checking of application reputation is available if you have agreed to participate in Kaspersky Security Network.
To learn the reputation of an application:
Open the context menu of the application’s executable file and select Check reputation in KSN.
This opens a window with information about the reputation of the application in Kaspersky Security Network.
Weak Settings Scan
In this section, you will learn about weak operating system settings, and how to search for and fix weak settings in the operating system.
About weak settings of the operating system
When you are working with a computer, operating system settings can be changed as a result of your actions or the actions of applications that you run. Changing the operating system settings can pose a risk to the security of your computer. For example, if automatic sign-in with the current user name and password is enabled in the browser, a third-party website can intercept your password.
Weak settings in the operating system can be divided into two types:
- Critical settings. Such settings are equated with vulnerabilities of the operating system.
- Recommended settings. You are advised to fix these settings to improve the security of the operating system.
By default, the application scans for weak settings of the operating system at least once a day. If the application detects weak settings in the operating system, it prompts you to fix them to restore the security of the operating system. For details about each weak setting, click the link next to the relevant setting in the application window.
You can click the link in the notification window to go to the Weak Settings Scan window that displays the weak settings detected in the operating system. Information about weak settings is also displayed in the Notification Center. You can proceed to view and fix the weak settings from the Notification Center.
In the Weak Settings Scan window, you can perform the following actions:
- Fix weak settings in the operating system.
- Ignore: Leave weak settings of the operating system unchanged.
- Cancel: Restore previously fixed weak settings of the operating system to their original state.
The application identifies weak settings of the operating system for all user accounts on your computer. You can fix weak settings for other user accounts on the computer only if you have logged in to the operating system under an administrator account.
If you are not an administrator of the computer, you can ignore weak settings only for your own user account. Only a computer administrator can ignore weak settings of all user accounts.
You can manually start a scan for weak settings or disable the scan for weak settings.
You can remotely manage the protection of your computer and send a command to fix weak settings from My Kaspersky.
Page topHow to find and fix weak settings in the operating system
To find and fix weak settings of the operating system:
- Open the main application window.
- Select the Security section.
- Under Security, select Weak Settings Scan.
- Click Scan.
This runs a Weak Settings Scan. After the scan is complete, you will see scan results in the Weak Settings Scan section.
- Click View to go to the Weak Settings Scan window.
- In the Weak Settings Scan window, select an action to take on weak settings:
- Detected weak settings. Do one of the following:
- Click the Fix all button to fix all weak settings.
- Click the Fix button to fix a weak setting.
- If open applications are interfering with fixing a weak setting, click the View button to view the list of interfering applications.
To close applications that prevent the setting from getting fixed, do one of the following:
- Click the
 button to the right of the name of the interfering application to shut it down normally. If the application detects any unsaved changes, it will prompt you to save them.
button to the right of the name of the interfering application to shut it down normally. If the application detects any unsaved changes, it will prompt you to save them. - Click the Force close link to close all interfering applications without saving data.
- Click the
- In the drop-down list next to the Fix button, select Ignore to leave a weak setting unchanged.
- In the drop-down list next to the Fix button, select Read more to view information about a weak setting on the Kaspersky Support website.
- Previously fixed weak settings.
- Click the Roll back button to restore the fixed setting to its original state.
- In the drop-down list next to the Roll back button, select Read more to view information about a weak setting on the Kaspersky Support website.
- Detected weak settings. Do one of the following:
- Ignored settings. Click the Show all link next to the N ignored settings message to open the list of weak settings that you left unchanged, and click the Fix button.
How to enable Weak Settings Scan
To disable the Weak Settings Scan:
- Open the main application window.
- Click
 in the lower part of the main window.
in the lower part of the main window.This opens the Settings window.
- Go to the Performance settings section.
- Click PC resource consumption.
- Clear the Scan for weak operating system settings check box.
The application will not scan for weak settings of the operating system or show alerts about them.
Network Monitor
Available only in Kaspersky Standard, Kaspersky Plus, and Kaspersky Premium.
Network Monitor allows you to view your PC's network activity data in real time, block network activity, or create network and packet rules for applications installed on your PC.
To go to the Network Monitor settings:
- Open the main application window.
- Go to the Security section.
- In the Network Monitor block, click the View button.
This opens the Network Monitor window.
The Network activity section displays all the currently active network connections. It displays both the inbound and outbound connections. You can use the Block all network activity link to block all network connections.
The Open ports section lists all the open network ports. You can also use this section to create network and packet rules for applications.
The Network traffic section displays the volume of inbound and outbound network traffic between your PC and other computers on your network.
The Blocked computers section contains a list of IP addresses for remote computers from which the Network Attack Blocker has detected network attack attempts and has blocked their network activity.
Page topSmart Home Monitor
This section contains information about how to use the Kaspersky application to find out which devices are connected to your wireline Ethernet network and the Wi-Fi network.
About the Smart Home Monitor component
Available only in Kaspersky Plus and Kaspersky Premium.
Hackers could potentially capture your password or hack into your home network to take advantage of your Internet or steal your data. The Kaspersky application protects your wireline Ethernet networks and Wi-Fi networks against unauthorized connections.
As soon as you confirm that your home network is detected correctly, we begin monitoring devices connected to that network and some vulnerabilities such as a weak Wi-Fi password or router encryption. If we detect vulnerabilities or a new device on the network that you have not previously identified as a known device, we will warn you about it and suggest recommendations to let you take steps to protect your home network and devices that use it.
Notifications about home network vulnerabilities are only available in Kaspersky Premium. Notifications about new devices connecting to your home network are available in Kaspersky Plus and Kaspersky Premium.
When a device connects your network, the Kaspersky application displays a relevant notification and asks if you would like to view the devices connected to this network:
- If you agree, the Kaspersky application shows a list of devices connected to this network and notifies you if a new device has connected to it.
- If you refuse, the Kaspersky application does not notify you when a connection to this network is established again, and does not display the list of devices that are connected.
You can disable Smart Home Monitor. When you disable the component, the Kaspersky application stops notifying you about connections to your network.
To learn other available security methods for connecting to Wi-Fi networks, visit the Kaspersky Support website.
Page topHow to enable or disable Smart Home Monitor
To enable or disable Smart Home Monitor:
- Open the main application window.
- Click
 in the lower part of the window.
in the lower part of the window.This opens the Settings window.
- Select the Security settings section.
- Select the Firewall component.
- Do one of the following:
- To enable Smart Home Monitor, select the Show devices that are connected to my networks check box.
- To disable Smart Home Monitor, clear the Show devices that are connected to my networks check box.
How to view devices on my network
The Kaspersky application shows the following information about devices connected to your Wi-Fi network or the wireline Ethernet network:
- Device name
- Device manufacturer
- Device type (e.g., computer, mobile device, router, gaming console, or video camera)
- Operating system installed on the device
- MAC address (unique network ID of the device)
- IP address of the device
- Time when disconnected devices were last detected in the network
- Kaspersky applications installed on your device
To view devices that are connected to your network:
Page topHow to deny network access for a device
To deny network access for a device:
- Open the main application window.
- Do one of the following:
- Go to the Security block, and click the View button in the Smart Home Monitor section.
- In the main application window, click the View button in the Smart Home Monitor section.
- Click the <network name> link that is displayed in the lower part of the main window.
- In the Smart Home Monitor window, select the device that you want to disconnect.
This opens a window with information about this device that includes information about the MAC address of the device.
- Write down the MAC address of the device
- Block the device MAC address in your browser settings. Visit the website of the specific vendor to view the User Guide for your router.
After the MAC address is blocked, the device will not be able to connect to your network.
Page topHow to delete a network with no connections from the list
To delete a network with no connections from the list:
- Open the main application window.
- Do one of the following:
- Go to the Security block, and click the View button in the Smart Home Monitor section.
- In the main application window, click the View button in the Smart Home Monitor section.
- Click the <network name> link that is displayed in the lower part of the main window.
This takes you to the Smart Home Monitor window.
- Click the arrow in the right part of the list to expand it and click
 next to the network that you want to remove.
next to the network that you want to remove.
The network will be deleted from the list.
Page topHow to disable notifications when devices connect to my network
To disable notifications when devices connect to the network:
- Open the main application window.
- Do one of the following:
- Go to the Security block, and click the View button in the Smart Home Monitor section.
- In the main application window, click the View button in the Smart Home Monitor section.
- Click the <network name> link that is displayed in the lower part of the main window.
- In the Smart Home Monitor window, click the
 button next to the network and select the item Disable notifications.
button next to the network and select the item Disable notifications.
The Kaspersky application will no longer show you notifications if any devices connect to this network.
You can also disable notifications for the selected network when the Kaspersky application shows you a notification that a device has connected to this network. To do this, in the notification window click the link Disable notifications for this network.
Page topHow to send feedback about Smart Home Monitor
To send feedback to Kaspersky about the operation of the Smart Home Monitor component:
- Open the main application window.
- Do one of the following:
- Go to the Security block, and click the View button in the Smart Home Monitor section.
- In the main application window, click the View button in the Smart Home Monitor section.
- Click the <network name> link that is displayed in the lower part of the main window.
- In the Smart Home Monitor window, click the
 button and select the item Send feedback.
button and select the item Send feedback.This opens the Help us improve! Leave your feedback window.
- Please rate the component on a 5-point scale by choosing from 1 to 5 stars.
- If you awarded a component 3-5 stars:
- If you want to add a comment to your feedback, enter it in the Details field.
- Select the I agree to provide my personal data (unique ID of my computer) to improve the software and I accept the terms of the Privacy Policy check box.
- If you awarded a component 1-2 stars:
- If you want to notify Kaspersky about a problem with the Smart Home Monitor component, select the subject with the closest meaning from the Topic drop-down list.
You can select one of the following options from the list:
- Inconvenient to use. Select this item if you are experiencing inconveniences when using the Smart Home Monitor component.
- Application takes a long time to search for devices in the network. Select this item if the Smart Home Monitor component is operating too slowly.
- Application incorrectly identifies devices in the network. Select this item if the application incorrectly determines the names and/or types of devices connected to the Wi-Fi network or the wireline Ethernet network.
- Too many notifications about new devices in the network. Select this item if the application shows you too many notifications about new devices in the Wi-Fi network or the wireline Ethernet network.
- Reduced computer performance. Select this item if the use of the Smart Home Monitor component slows the performance of your computer.
- Cannot configure the component. Select this item if you experience difficulties when configuring the Smart Home Monitor component.
- Other. Select this item if the problem you are experiencing is not covered by the other items.
- If you want to add a comment to your feedback, enter it in the Details field.
- Select the I agree to provide my personal data (unique ID of my computer) to improve the software and I accept the terms of the Privacy Policy check box.
- If you want to notify Kaspersky about a problem with the Smart Home Monitor component, select the subject with the closest meaning from the Topic drop-down list.
- Click Send.
When this data is sent, Kaspersky receives and processes the following information:
- Your feedback, which contains an assessment of component performance, the issue topic, and comments.
- Operating system information and version.
- Information about the installed application and its version.
Kaspersky receives and processes this information in encrypted form for the purpose of analyzing errors and improving the performance of the Smart Home Monitor component. Kaspersky does not require you to provide any personal information when sending feedback, and does not collect such information. For details on how personal data is processed, please refer to the Kaspersky Privacy Policy.
Page topPre-Kaspersky virus removal
This section contains information on restoring the operating system after it has been infected with malware.
Recovering the operating system after infection
If you suspect that the operating system of your computer has been corrupted or modified due to malware activity or a system failure, use the Microsoft Windows Troubleshooting Wizard, which clears the system of any traces of malicious objects. Kaspersky recommends that you run the Wizard after the computer has been disinfected to make sure that all threats and damage caused by infections have been fixed.
The Wizard checks whether there are any changes to the system, which can include access to the network being blocked, file name extensions for known formats being changed, Control Panel being blocked, etc. There are different reasons for these different kinds of damage. These reasons may include malware activity, incorrect system configuration, system failures, or malfunctioning applications for system optimization.
After the review is complete, the Wizard analyzes the information to evaluate whether there is system damage that requires immediate attention. Based on the review, the Wizard generates a list of actions that are necessary to eliminate the damage. The Wizard groups these actions by category based on the severity of the problems detected.
Troubleshooting the operating system by using the Microsoft Windows Troubleshooting Wizard
To run the Microsoft Windows Troubleshooting Wizard:
- Open the main application window.
- Go to Security → Microsoft Windows Troubleshooting.
- Click Find damage.
The Microsoft Windows Troubleshooting Wizard window opens.
The Wizard consists of a series of pages (steps), which you can navigate through by clicking the Back and Next buttons. To close the Wizard after it finishes, click the Done button. To stop the Wizard at any stage, click the Cancel button.
Let us review the steps of the Wizard in more detail.
Start recovery of the operating system
- Select one of the two options for Wizard operation:
- Search for damage caused by malware activity. The Wizard will search for problems and possible damages.
- Roll back changes. The Wizard will roll back the fixes applied to previously identified problems and damages.
- Click Next.
Search for problems
If you selected the Search for damage caused by malware activity option, the Wizard searches for problems and possible damages that should be fixed. When the search is complete, the Wizard proceeds automatically to the next step.
Select actions to fix damage
All damage found at the previous step is grouped based on the type of danger that it poses. For each damage group, Kaspersky recommends a set of actions to repair the damage.
There are three groups:
- Strongly recommended actions eliminate problems that pose a serious security threat. You are advised to repair all damage in this group.
- Recommended actions are aimed at repairing damage that may pose a threat. You are also advised to repair damage in this group.
- Additional actions repair operating system damage that is not dangerous now, but may pose a threat to the computer's security in the future.
Expand the list of the selected group to view damage within the group.
To get the Wizard to fix a specific type of damage, select the check box next to the damage description. By default, the Wizard fixes damage belonging to the groups of recommended and strongly recommended actions. If you do not want to fix a specific type of damage, clear the check box next to it.
It is strongly recommended that you not clear the check boxes selected by default, as doing so will leave your computer vulnerable to threats.
After you define the set of actions for the Wizard to perform, click the Next button.
Fix damage
The Wizard performs the actions selected during the previous step. It may take a while to fix damage. After fixing damage, the Wizard automatically proceeds to the next step.
Wizard completion
Click the Done button to exit the Wizard.
Operating system emergency recovery
Kaspersky Rescue Disk is intended for emergency recovery of the operating system. You can use Kaspersky Rescue Disk for scanning and disinfecting infected computer that cannot be disinfected using other methods (for example, with anti-virus applications).
More details on using Kaspersky Rescue Disk are available on the Kaspersky Support website.
Page topHow to restore a deleted or disinfected file
Backup copies of deleted or disinfected files are placed in a special folder on your computer, named Quarantine. Backup copies of files are stored in a special format that is not dangerous to your computer. You can restore deleted or disinfected file from the backup copy stored in Quarantine.
We recommend that you avoid restoring deleted or disinfected files since they may pose a threat to your computer.
The application does not disinfect Windows Store apps. If scanning results indicate that such an app is dangerous, it is deleted from your computer. When a Windows Store app is deleted, the Kaspersky application does not create a backup copy of it. To restore such objects, you must use the recovery tools included with the operating system (for detailed information, see the documentation for the operating system that is installed on your computer) or update apps via the Windows Store.
To restore deleted or disinfected file:
- Open the main application window.
- Go to the Security section.
- In the upper-right corner of the Kaspersky application window, click the Quarantine button.
This opens the Quarantine window.
- In the Quarantine window that opens, select the required file from the list and click the Restore button.
Protecting email
This section provides information about how to protect your email against spam, viruses, and other threats.
Configuring Mail Anti-Virus
The Kaspersky application allows scanning email messages for dangerous objects by using Mail Anti-Virus. Mail Anti-Virus starts when the operating system is started and remains constantly in the RAM of the computer, scanning all email messages that are sent or received over the POP3, SMTP, IMAP, and NNTP protocols, as well as via encrypted connections (SSL) over the POP3, SMTP, and IMAP protocols.
By default, Mail Anti-Virus scans both incoming and outgoing messages. If necessary, you can enable scanning of incoming messages only.
To configure Mail Anti-Virus:
- Open the main application window.
- Click
 in the lower part of the main window.
in the lower part of the main window.This opens the Settings window.
- Select the Security settings section.
- In the Security settings window, select the Mail Anti-Virus component.
This takes you to the Mail Anti-Virus settings window.
- Make sure that the switch in the upper part of the window that enables / disables Mail Anti-Virus, is enabled.
- Select a security level:
- Optimal. When this security level is set, Mail Anti-Virus scans incoming and outgoing messages and attached archives, and performs heuristic analysis with the Medium scan level of detail.
- Low. If you select this security level, Mail Anti-Virus scans incoming messages only, without scanning attached archives.
- Extreme. When this security level is set, Mail Anti-Virus scans incoming and outgoing messages and attached archives, and performs heuristic analysis with the Deep scan level of detail.
- In the Action on threat detection section, select the action that you want Mail Anti-Virus to perform when an infected object is detected (for example, disinfect).
If no threats are detected in an email message, or if all infected objects have been successfully disinfected, the message becomes available for further access. If the component fails to disinfect an infected object, Mail Anti-Virus renames or deletes the object from the message and adds a notification to the message subject line, stating that the message has been processed by the Kaspersky application. Before deleting an object, the Kaspersky application creates a backup copy of it and places a copy in Quarantine.
When you upgrade to a more recent application version, the user-configured Mail Anti-Virus settings are not saved. The new application version will use the default Mail Anti-Virus settings.
If the Kaspersky application detects the password for the archive in the message text during scanning, the password is used to scan the contents of that archive for malware. The password is not saved. The archive is unpacked before scanning. If the application crashes while unpacking the archive, you can manually delete the files that are unpacked at the following path: %systemroot%\temp. The files have the PR prefix.
Blocking unwanted email (spam)
If you receive large amounts of unwanted messages (spam), we recommend that you enable the Anti-Spam component and set the Optimal security level for it.
To enable Anti-Spam and set the Optimal security level:
- Open the main application window.
- Click
 in the lower part of the main window.
in the lower part of the main window.This opens the Settings window.
- Select the Privacy settings section.
- Select the Anti-Spam component.
The window displays the settings of Anti-Spam.
- Enable Anti-Spam using the switch.
- In the Security level section, make sure that the Optimal security level is set.
The following limitations apply to Anti-Spam:
- The Anti-Spam component can only analyze messages that are fully downloaded from the mail server, regardless of the protocol used.
- The Anti-Spam component does not check mail transferred using MAPI protocol.
The Anti-Spam component is disabled when you upgrade to a more recent application version. You can enable the component manually.
In some versions of the application, to enable the Anti-Spam component, you must accept the terms of the Statement regarding data processing for Anti-Spam.
Participating in Kaspersky Security Network
The Kaspersky application uses cloud protection to make protection of your computer more effective. Cloud protection is implemented using the Kaspersky Security Network infrastructure that uses data received from users all over the world.
Kaspersky Security Network (KSN) is the cloud-based knowledge base of Kaspersky containing information about the reputation of applications and websites. The use of data from Kaspersky Security Network ensures faster responses by the Kaspersky application to new threats, improves the performance of some protection components, and reduces the likelihood of false positives.
Users' participation in Kaspersky Security Network allows Kaspersky to promptly receive information about types and sources of new threats, develop solutions for neutralizing them, and minimize the number of false positives. Participation in Kaspersky Security Network lets you access reputation statistics for applications and websites.
If you participate in Kaspersky Security Network, you automatically send information about the configuration of your operating system and the start and completion time of processes in the Kaspersky applications to Kaspersky.
How to enable or disable participation in Kaspersky Security Network
Participation in Kaspersky Security Network is voluntary. You can enable or disable the use of Kaspersky Security Network (KSN) when installing the Kaspersky application and/or at any moment after the application is installed.
To enable or disable participation in Kaspersky Security Network:
- Open the main application window.
- Click
 in the lower part of the main window.
in the lower part of the main window.This opens the Settings window.
- Go to Security settings → Kaspersky Security Network.
The Kaspersky Security Network window opens showing the details of Kaspersky Security Network and Kaspersky Security Network participation settings.
- Enable or disable participation in Kaspersky Security Network by using the toggle in the upper part of the window:
- If you want to participate in Kaspersky Security Network, set the toggle to On.
A window with the text of the Kaspersky Security Network Statement opens. If you accept the terms of the statement, click I agree.
- If you do not want to participate in Kaspersky Security Network, set the toggle to Off.
- If you want to participate in Kaspersky Security Network, set the toggle to On.
In some versions of the Kaspersky application, the Kaspersky Security Network window shows the Kaspersky Security Network Statement instead of information about Kaspersky Security Network.
To accept Kaspersky Security Network Statement:
- Click the Accept button in the Kaspersky Security Network Statement section.
Kaspersky Security Network Statement opens. This statement allows Kaspersky experts to promptly receive information about threats detected on your computer, about applications being run and signed applications being downloaded, as well as operating system information to improve your protection.
- If you accept the terms of the statement, click the Accept button.
To decline the Kaspersky Security Network Statement,
click the Decline button in the Kaspersky Security Network Statement section.
How to check the connection to Kaspersky Security Network
Your connection to Kaspersky Security Network may be lost for the following reasons:
- You do not participate in Kaspersky Security Network.
- Your computer is not connected to the Internet.
- Current key status does not allow connecting to Kaspersky Security Network. For example, a connection to KSN may be unavailable due to the following reasons:
- The application is not activated.
- License or subscription has expired.
- License key issues have been identified (for example, the key has been added to denylist).
The current status of the key is displayed in My Kaspersky.
To check the connection to Kaspersky Security Network:
- Open the main application window.
- Go to Security settings → Kaspersky Security Network.
The Kaspersky Security Network window shows the status of your connection to Kaspersky Security Network.
Page topProtection using hardware virtualization
In this section, you will learn how you can protect your computer using hardware virtualization.
About protection using hardware virtualization
When the Kaspersky application is installed in 64-bit Microsoft Windows 8, Microsoft Windows 8.1 or Microsoft Windows 10, it uses
technology for additional protection against complex malware that could intercept your personal data by using the clipboard or phishing.Protection using hardware virtualization is enabled by default. If protection has been disabled manually, you can enable it in the application settings window.
On computers running 64-bit Microsoft Windows 8, Microsoft Windows 8.1 or Microsoft Windows 10, the protection provided by Kaspersky hardware virtualization (hypervisor) has the following limitations:
- This feature is not available when a third-party hypervisor is running, such as the hypervisor used by the VMware virtualization software. After you close the third-party hypervisor, protection against screenshots becomes available again.
- The feature is not available if the CPU of your computer does not support hardware virtualization technology. For more details on whether your CPU supports hardware virtualization, please refer to the documentation shipped with your computer or to the website of the CPU manufacturer.
- The feature is not available if a third-party hypervisor (such as the VMware hypervisor) is running when you start Protected Browser.
- The feature is not available if hardware virtualization is disabled on your computer. For details on how to enable hardware virtualization on your computer, please refer to your computer's technical documentation or visit the website of your processor's manufacturer.
- The feature is not available if Device Guard is enabled in the Microsoft Windows 10 operating system.
- The feature is not available if Virtualization Based Security (VBS) is enabled in the Microsoft Windows 10 operating system.
How to enable protection using hardware virtualization
To enable protection using hardware virtualization:
- Open the main application window.
- Click
 in the lower part of the main window.
in the lower part of the main window.This opens the Settings window.
- Go to Security settings → Privacy settings → Secure Data Input.
- Select the Use hardware virtualization if available check box. This check box is displayed when the application is installed on a 64-bit version of Windows 8, Windows 8.1 and Windows 10.
- Select the Use advanced features of hardware virtualization check box if you want to turn hardware virtualization on when the operating system starts.
If hardware virtualization is disabled on your computer, protection using hardware virtualization will be disabled.
Protection using Antimalware Scan Interface (AMSI)
This section informs you that third-party applications such as Microsoft Office can send scripts to the Kaspersky application to be scanned using the Antimalware Scan Interface (AMSI), and describes how to disable protection using the AMSI in the Kaspersky application.
About protection using Antimalware Scan Interface
Antimalware Scan Interface (AMSI) allows a third-party application that supports AMSI to send objects (for example, PowerShell scripts) to the Kaspersky application for additional scanning and to receive scan results for these objects. For example, Microsoft Office applications can be such third-party applications. For more information about the AMSI interface, refer to Microsoft documentation.
Antimalware Scan Interface allows only to detect a threat and notify a third-party application about the detected threat. After receiving the threat notification, the third-party application prevents malicious actions (for example, shuts down).
The Kaspersky application may decline a request from a third-party application if, for example, this application exceeds the maximum number of requests allowed for a period. In this case, the Kaspersky application displays a notification about the declined request. If you receive such a notification, you do not have to perform any actions.
Protection using Antimalware Scan Interface is available on Windows 10 Home / Pro / Education / Enterprise and Windows 11 Home / Pro / Enterprise operating systems.
Page topHow to enable protection using Antimalware Scan Interface
To enable protection using Antimalware Scan Interface:
- Open the main application window.
- Click
 in the lower part of the main window.
in the lower part of the main window.This opens the Settings window.
- Go to Security settings → AMSI Protection.
- In the Script scanner section, select the Scan scripts using Antimalware Scan Interface (AMSI) check box.
How to exclude a script from scanning using Antimalware Scan Interface
To exclude a script from scanning using Antimalware Scan Interface:
- Open the main application window.
- Click
 in the lower part of the main window.
in the lower part of the main window.This opens the Settings window.
- Go to Security settings → AMSI Protection.
- In the Script scanner section, select the Scan scripts using Antimalware Scan Interface (AMSI) check box.
- Click the Manage exclusions link to go to the Exclusions window.
- In the Exclusions window, click the Add button.
The Add new exclusion window opens.
- In the File or folder field, specify the folder with the script.
- In the Object field, specify the name of the script.
You can also add several files of the same type to the exclusions by using a mask.
- In the Protection components section, select the check box next to the File Anti-Virus component.
- Select the Active status.
The specified object will not be scanned using Antimalware Scan Interface.
Remote management of computer protection
If your computer has Kaspersky installed and is connected to My Kaspersky, you can manage protection of this computer remotely.
To manage computer protection remotely, sign in to your My Kaspersky account and go to the Devices section.
In the Devices section, you can:
- View the list of computer security problems and fix them remotely
- Scan the computer for viruses and other threats
- Update databases and application modules
- Configure Kaspersky components
If a computer scan is started from My Kaspersky, Kaspersky processes objects that are detected automatically without your involvement. On detecting a virus or other threat, the Kaspersky application attempts to perform disinfection without rebooting the computer. If disinfection without restarting the computer is impossible, the list of computer security problems on My Kaspersky shows a message to the effect that the computer needs restarting to perform disinfection.
If the list of detected objects on My Kaspersky includes more than 10 items, they are grouped. In this case, the detected objects can be processed via My Kaspersky only together without the ability to examine each object separately. To view separately objects in this case, you are advised to use the interface of the application installed on the computer.
How to proceed to remote management of computer protection
To proceed to remote management of computer protection:
- Open the main application window.
- Go to the Profile section.
- In the Sign in to My Kaspersky block, click the Sign in button.
- In the window that opens, perform one of the following operations:
- If you have an account, enter your email address and password and connect to My Kaspersky.
- If you do not have an account, enter your email address in the text box and click Create. A message with a password creation link is sent to the specified email address.
After a successful connection, the Profile section displays information about your connection to the account. You can now manage protection of this computer remotely from your My Kaspersky account.
To learn more about remotely managing device protection, see My Kaspersky Help.
Page top