Example of analyzing a Data Discovery detection
This section contains an example of a Data Discovery detection and how you can analyze and process it.
Let's consider that you open the Data Discovery widget (see the figure below) and see a file that is accessible to everyone (the value in the Access type column is Public).
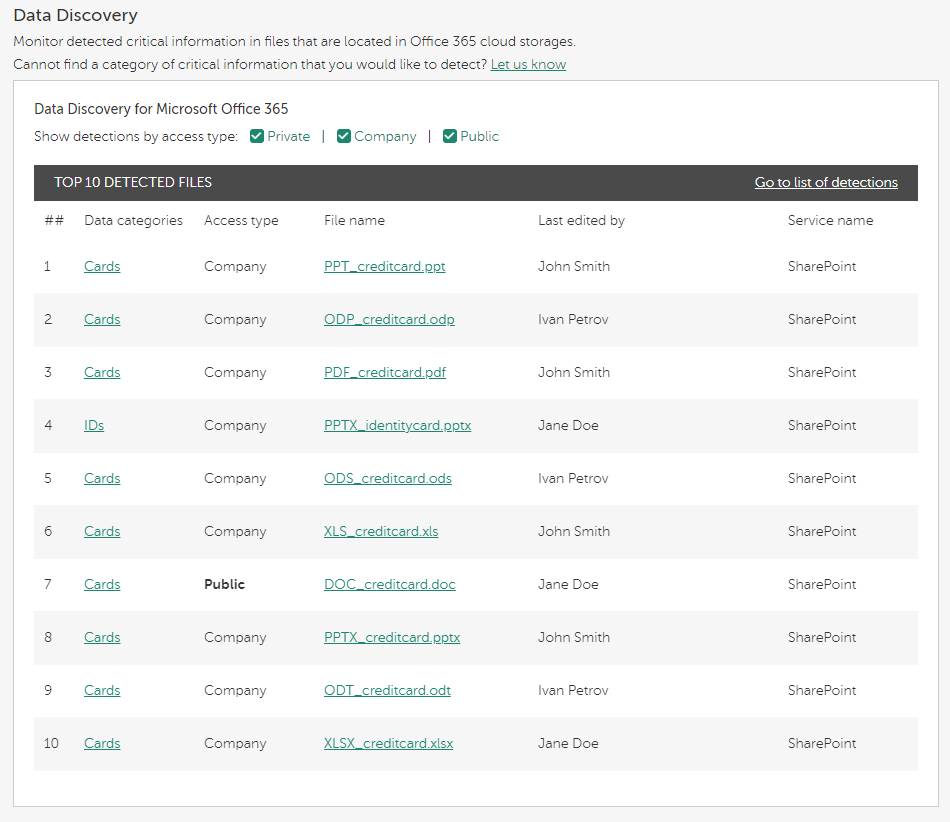
Data Discovery widget with a file that is accessible to everyone
From the value in the Data categories column, you conclude that the file contains credit card details. The value in the Last edited by column most often shows the user who configured the accessibility of the file.
By clicking the link in the Data categories or File name column, you can view detailed information about the detected file (see the figure below).
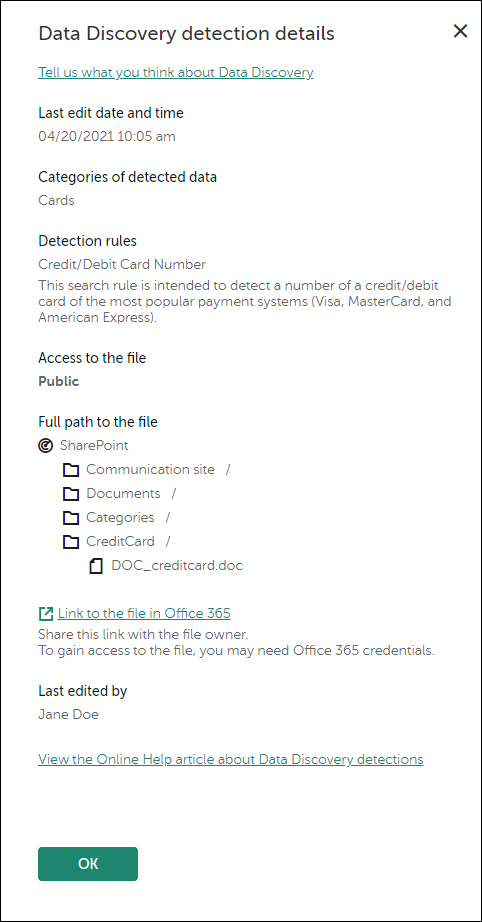
Data Discovery detection details
You can copy either the direct link to the file (Link to the file in Microsoft 365) or the structure of the path to it (under Full path to the file).
Then you can address the user directly, show him or her the file, and explain that making a file with personal details accessible to everyone may lead to a data breach. Then, you can ask the user to reduce the file audience to the user himself or herself.
Some time later, after the user follows your advice, you can open the Data Discovery table, apply the filters (if necessary), and see the same document that is accessible only to its owner (see the figure below).

Data Discovery table with applied filters
Page top