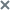Viewing the prevention rule table
The table of prevention rules is in the Prevention section of the application web interface window.
The table contains the following information:
- Type is the type of the rule depending on the operating mode of the application and the role of the server which generated the rule:
- Global—Created on the PCN. These prevention rules apply to hosts that are connected to this PCN server and to all SCN servers that are connected to this PCN server. Prevention rules belong to the tenant which the user is managing in the program web interface.
- Local—Created on the SCN server. These prevention rules apply only to hosts that are connected to this SCN server. Prevention rules belong to the tenant which the user is managing in the program web interface.
- Name is the name of the prevention rule.
- Created by—Name of the user whose account was used to create the rule.
- File hash—Hashing algorithm applied to identify a file.
A file can be identified based on one of the following hashing algorithms:
- MD5.
- SHA256.
Clicking the link with the name of the hashing algorithm opens a list in which you can view the file hash and select one of the following actions:
- Filter by this value.
- Exclude from filter.
- Find on TIP.
- Find on virustotal.com (for SHA256).
- Find events.
When this action is performed, the Threat Hunting section opens with events that are already filtered based on the hash you selected.
- Find alerts.
When this action is performed, the Alerts section opens with alerts that are already filtered based on the hash you selected.
- Enable prevention rule.
- Disable prevention rule.
- Delete prevention rule.
- Copy value to clipboard.
- Servers are names of servers with the PCN or SCN role to which the prevention rule applies.
This field is displayed if you are using the distributed solution and multitenancy mode.
- Hosts is the name of the server with the Central Node component to whose hosts the prevention rule is applied.
This field is displayed only when you are using a standalone Central Node server.
- State is the current state of the prevention rule.
A prevention rule can have one of the following states:
- Enabled
- Disabled