Segmentation rules
Segmentation rules allow you to automatically split related alerts into different incidents based on the conditions that you specify when creating the rules.
Use segmentation rules to create different incidents based on related alerts. For example, you can combine several alerts with an important distinguishing feature into a separate incident.
Alerts can only be linked to an incident that belongs to the same tenant.
The segmentation rules are triggered according to the specified priority. The higher the rule is in the list of segmentation rules, the higher its priority. If you want to change the segmentation rule priority, drag and drop the rule by clicking its name.
We recommend that you use segmentation rules together with aggregation rules to define more precise rules for creating incidents.
To create a segmentation rule:
- In the main menu, go to Settings → Tenants.
The tenant list opens. The list contains only the tenants to which you have at least the Read access right.
- Click the tenant for which you want to create a segmentation rule.
- In the Settings tab, click the Segmentation rules subsection of the Detection and response section.
The list of segmentation rules opens.
- Click the Create button.
A Create segmentation rule window appears.
- Specify the segmentation rule settings:
- Status
Enable or disable the rule. By default, the rule is disabled.
- Rule
A unique name for the rule.
- Max alerts in incident
Maximum number of alerts in a single incident. The value must be between 1 and 200, and also must be greater than or equal to Min alerts in incident. The default value is 200. If the number of alerts exceeds the specified value, another incident is created.
- Min alerts in incident
Minimum number of alerts in a single incident. The minimum and default value is 1. The value must be less then or equal to Max alerts in incident. If the number of alerts does not reach the specified value, an incident is not created.
- Search interval
A time interval from which to select alerts and incidents. You can specify the value in days or in hours. The default value is 30 days.
- Description
Optional. Rule description.
- Groups
A jq expression that defines the array of string identifiers by which to assign alerts to incidents.
If necessary, you can copy the jq expression for Groups section from another segmentation rule. To do that, click the Copy from another rule button.
Example:
if any(.Observables[]? | select(.Type | ascii_downcase == "username") | .Value; startswith("adm_")) then ["Brute force admin"] else ["Brute force not admin"] end - Incident name
A jq expression that defines the template for naming the incidents created according to this segmentation rule. By default, the following expression is specified:
"\(.Rules[]?.Name), \(.SourceCreatedAt)"If necessary, you can copy the jq expression for Incident name section from another segmentation rule. To do that, click the Copy from another rule button.
Example:
if any(.Observables[]? | select(.Type | ascii_downcase == "username") | .Value; startswith("adm_")) then "Brute force admin" else "Brute force not admin" end - Trigger
A jq expression that defines the condition for including alerts in the incident.
If necessary, you can copy the jq expression for Trigger section from another segmentation rule. To do that, click the Copy from another rule button.
Example:
any(.Rules[]?; .ID == "123")
- Status
- Click the Save button.
The segmentation rule is saved and displayed in the table of segmentation rules. If necessary, you can edit the rule setting by clicking its name in the table.
When an alert is created, it is checked by all active segmentation rules in accordance with their priority. After the first rule is triggered, an array of string identifiers is formed for the alert, and the search starts for the incident to which the alert will be linked.
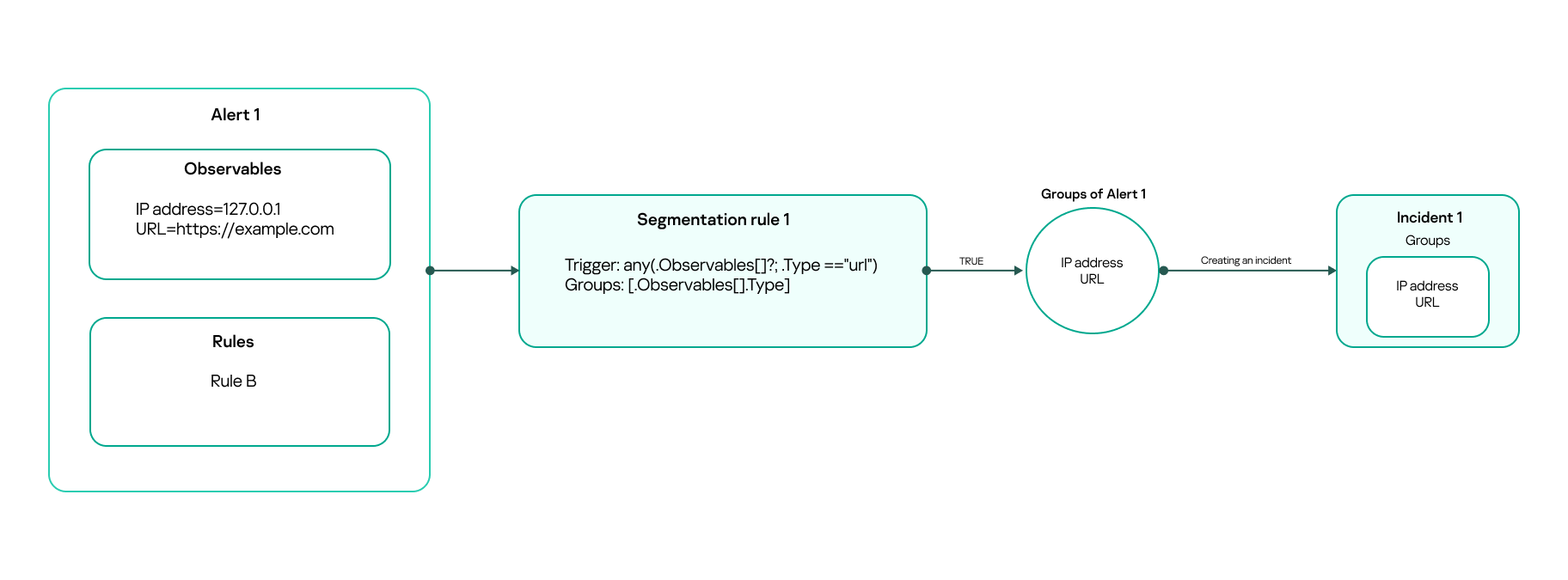
Creating a new incident after the first segmentation rule is triggered
A rule is triggered if the jq expression that you have specified in the Trigger section returns true.
Alerts cannot be linked to incidents created manually.
An incident also has an array of string identifiers, which include the arrays of the alerts already linked to this incident. If the alert for which the segmentation rule was triggered has at least one element in its array that matches with any of those in the incident's array, the alert is linked to the incident. As a result, the array of this alert is added to the incident's array.

Linking an alert to an existing incident after detecting matching elements
If there are several incidents meeting the condition, the alert is linked to the one with the most recent update. If there are no incidents with matching elements in arrays, a new incident is created.
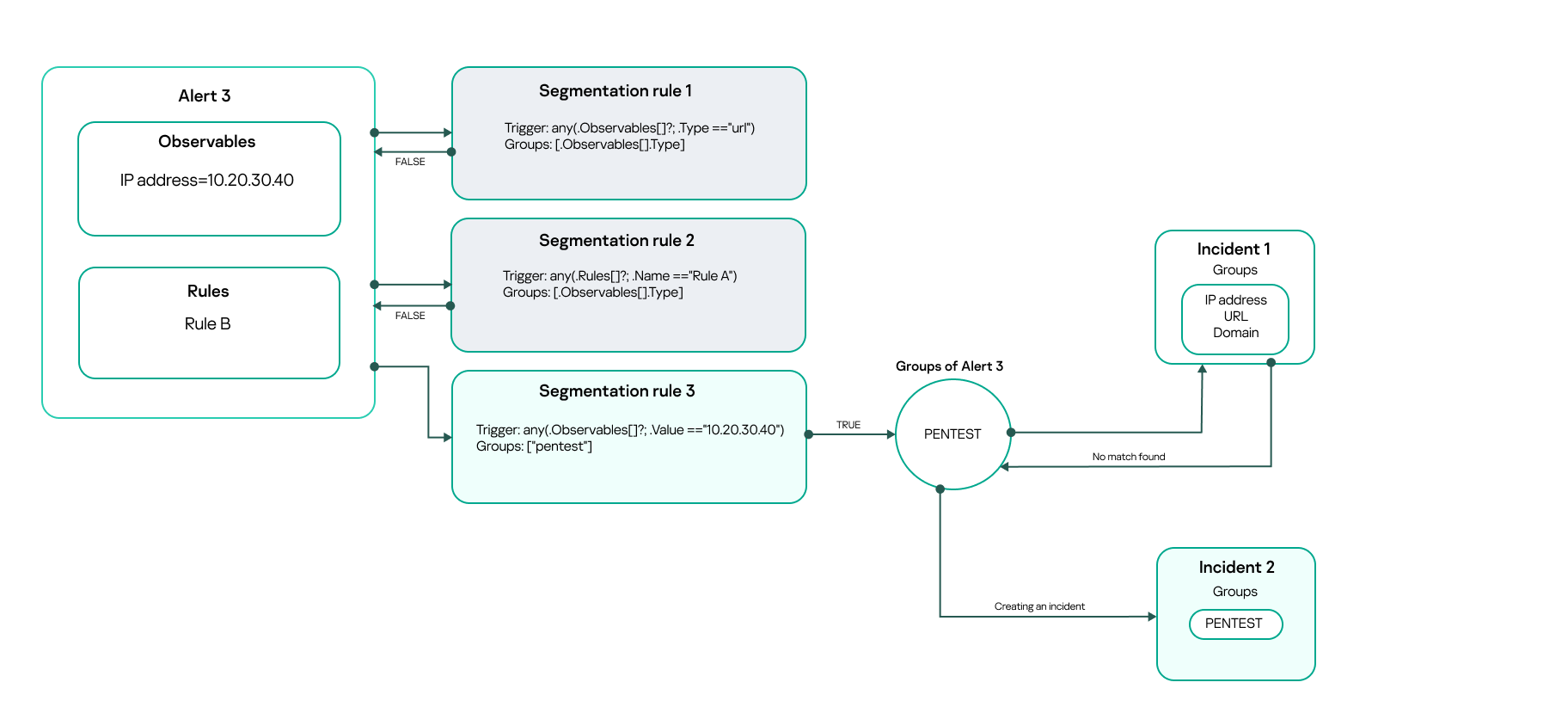
Creating a new incident after no matching elements are found based on the first two segmentation rules
When an incident is new, its array is empty. A new incident takes the array of string identifiers from an alert after the alert is linked.
Segmentation rule. Example
Configure the aggregation rules from the Aggregation rules. Example section in this topic.
The table below illustrates how to combine all penetration testing alerts in a single incident.
Segmentation rule
Attribute |
Value |
Trigger |
.AggregationID == "Pentest" |
Groups |
["Pentest"] |
Incident Name |
"Pentest incident" |
Aggregation and segmentation rules. Example
The table below illustrates how to combine alerts that have the same rule id in two incidents based on the user name prefix.
Aggregation rule
Attribute |
Value |
Description |
Trigger |
any(.Rules[]?; .ID == "123") |
Searches alerts with the rule id set to "123". |
Aggregation ID |
if any(.OriginalEvents[]?.BaseEvents[]?.DestinationUserName // empty; startswith("adm_")) then "rule123_DestinationUserName_adm" else "rule123_DestinationUserName_not_adm" end |
Searches for user names with the "adm_" prefix. |
Alert Name |
if any(.OriginalEvents[]?.BaseEvents[]?.DestinationUserName // empty; startswith("adm_")) then "Rule123 admin" else "Rule123 not admin" end |
Sets the alert name depending on the user name prefix. |
Segmentation rule
Attribute |
Value |
Trigger |
.AggregationID | startswith("rule123_DestinationUserName") |
Groups |
[.AggregationID] |
Incident Name |
.Name |